Disable Auto-Sandboxing on a Per-application Basis
The default auto-sandbox rules will
run unknown executables in sandboxed environment and queue them for
submission to Comodo Cloud scanners for behavior analysis. Users do,
however, have the option to exclude specific files or file types from
this auto-sandboxing process by creating a rule. This is particularly
useful for developers that are creating new applications which, by
their nature, are as yet unknown to the Comodo safe list.
To disable the auto-sandboxing selectively
1. Open 'Tasks' interface by clicking the green curved arrow at top right of the 'Home' screen
2. Open 'Sandbox Tasks' and click 'Open Advanced Settings'.
3. Click 'Security Settings' > 'Defense+ ' > 'Sandbox' > 'Auto-Sandbox' from the left hand side pane
4. Click the handle at the bottom of the interface and open the option panel
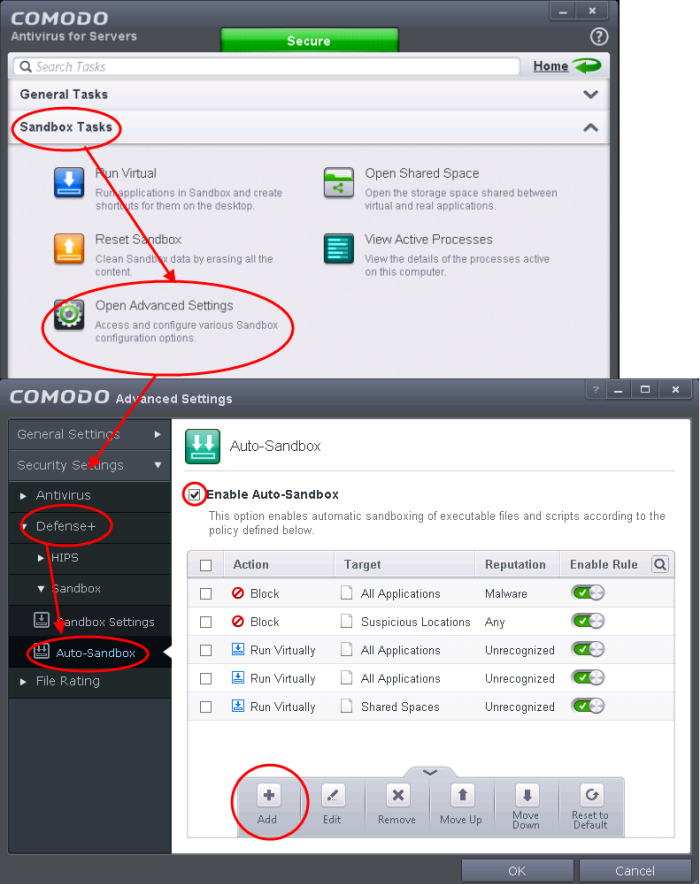
5. Click the 'Add' button
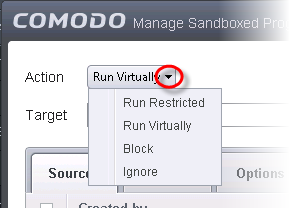
6. In the Manage Sandboxed Program interface, select 'Ignore' from the 'Action' drop-down options:
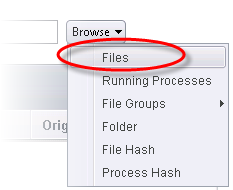
7. By default the Source tab will be selected. Click the Browse button beside the Target field then click Files from the options.
8. Navigate to the location where is the application is installed or stored, select it and click 'Open'. Click here for details about adding to target from other options.
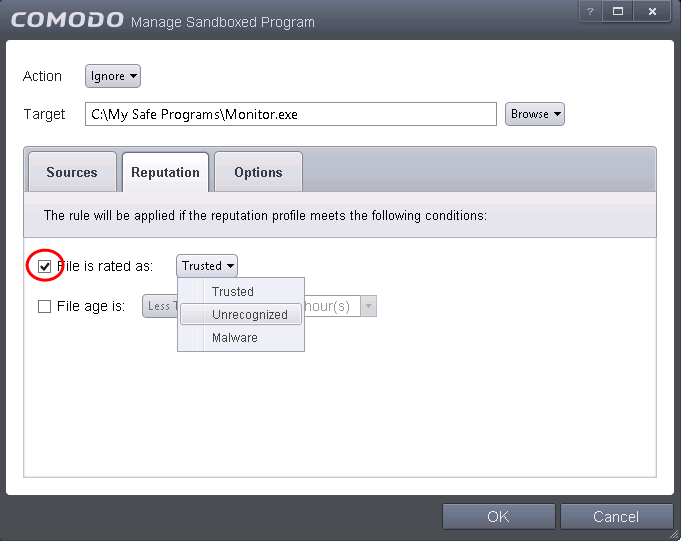
9. Click the Reputation tab, select the checkbox beside 'Select file rating' and click 'Unrecognized' from the drop-down options.
-
Click the 'Options' tab.
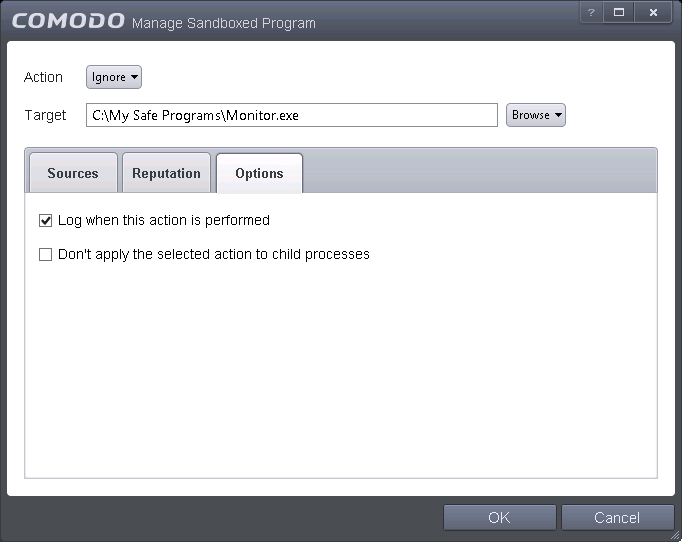
- By default, 'Log when this action is performed' will be selected.
- Log when this action is performed – Whenever this rule is applied for the action, it will be logged.
- Don't apply the selected action to child processes – Child processes are the processes initiated by the applications, such as launching some unwanted app, third party browsers plugins / toolbars that was not specified in the original setup options and / or EULA. CAVS treats all the child processes as individual processes and forces them to run as per the file rating and the Sandbox rules.
Select the options as required and click 'OK'.
- By default, this option is not selected and the ignore rule is applied also to the child process of the target application(s).
- If this option is selected, then the Ignore rule will be applied only for the target application and all the child processes initiated by it will be checked and Sandbox rules individually applied as per their file rating.
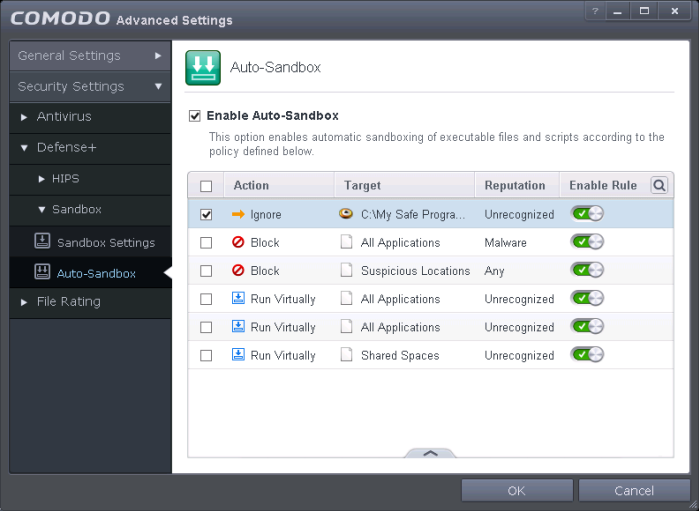
The Ignore rule will be saved for the specified application and displayed in the Auto-Sandbox screen. Make sure to keep this rule above all other rules for unrecognized files.
Alternatively…
1. Assign Trusted rating to the file from the File List interface
2. Digitally sign your files with a code signing certificate from a trusted CA then manually add your organization to the Trusted Software Vendors list
3. Disable Auto-Sandbox by de-selecting the 'Enable Auto-Sandbox' check box in the Auto-sandbox settings panel. Not recommended.
For more details on creating rules
for auto-sandboxing, refer to the section Configuring
Rules for Auto-Sandbox.



