The Dashboard
- The dashboard shows a summary of collected logs, events and incidents detected on customer networks over a selected period of time. This allows admins to more effectively track customer progress, diagnose potential issues and to make informed decisions should corrective actions need to be taken.
- The default view shows details collected for all enrolled customers. You view statistics for a particular customer by clicking 'Settings' > 'Customer Selection'. You can also can filter statistics by customer by choosing a customer on the left.
- Log Collection - Displays graphical summaries of logs collected from different networks.
- Security Events - The 'Security Events' tab provides critical information such as top 10 attack sources, top 10 attack destinations, top 10 firewall event sources and number of firewall events happened per minute.
- Incidents - The 'Incidents' tab provides details such as incident list, top 10
alerts, open incidents and unassigned incidents.
The 'Situational Awareness' dashboard is shown by default whenever you log-in to cWatch. You can reach the interface at any time by clicking 'Menu' > 'Dashboard' > 'Situational Awareness':
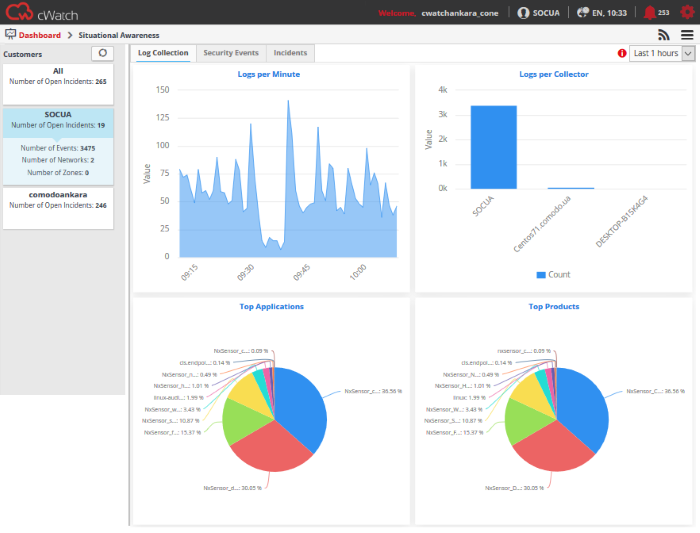
By default, the statistics for all customers will be displayed after logging-in.
Selecting Customer and Time Period
The left hand menu displays a list of all enrolled customers along with details such as the number of events, number of open incidents, number of networks, number of zones and number of agents for each customer. The top item in the list displays a consolidated summary of details from all the customers.
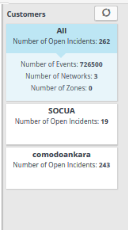
- To view the charts with details from all the customers on the dashboard, select 'All' from the list
- To view the charts pertaining to a selected customer on the dashboard, select the customer from the list
- To
update the list of customers and number of events, click the refresh
button at the top
The drop-down at top left allows you to choose the time period for which the statistics should be displayed. You can choose from the past hour up to the past 24 hours.
|
Tip: You can also create custom dashboards to show data tailored to your requirements. Custom dashboards let you view complex queries in easy-to-understand charts. This allows you to effectively track, monitor and analyze customer activity. See 'Configuring Custom Dashboards' for more details. |
Following sections explain more on:
The 'Log Collection' tab displays statistics of logs collected from the selected customer networks as four charts, 'Logs per Minute', 'Logs per Collector', 'Top Applications' and 'Top Products'. Comodo cWatch Network gathers logs from various systems, tools and devices so that the data may be searched, correlated and used to create reports.
Logs per Minute
The chart shows the number of logs collected from various sources in selected customer network at different time points.
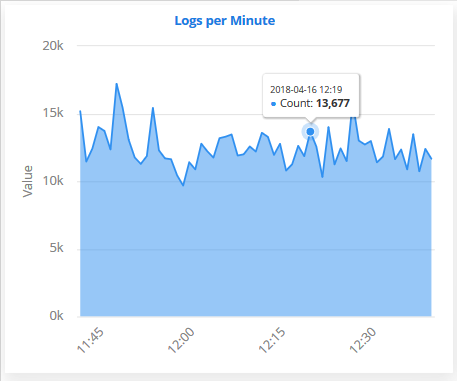
Placing the
mouse cursor on the graph shows the exact number of logs collected at
that time point as a tool tip.
Logs per Collector
The 'Logs per Collector' chart shows the number of log entries collected from different agents/networks pertaining to the selected customer's networks.

Placing the mouse cursor on a bar shows the exact number of the log entries collected from the respective agent as a tool tip.
Top Applications
The 'Top Applications' pie-chart shows the percentage breakup of number of log entries received from events generated by various applications running in the customer's network.
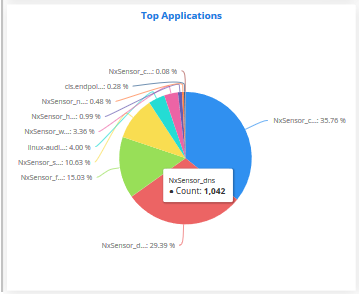
Placing
the mouse cursor on a sector shows the exact number of the log
entries collected from the respective application as a tool tip.
Top Products
The 'Top Products' pie-chart shows the percentage breakup of number of log entries of events generated by network appliances and firewalls connected to the customer's network.
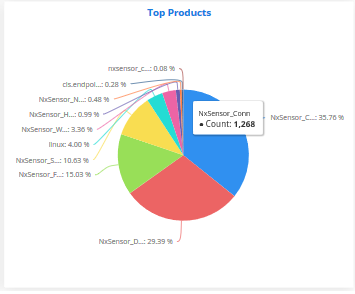
Placing the mouse cursor on
a sector shows the exact number of the log entries collected from the
respective product, as a tool tip.
The 'Security Events' tab in the dashboard displays summaries of events detected from the customer networks as four graphs, 'Top Attack Sources', 'Top Attack Destinations', 'Top Firewall Event Sources' and 'Firewall Events Per Minute'. Comodo cWatch Network gathers logs from various systems, tools and devices so that the data may be searched, correlated and used to create these reports. The data is then analyzed automatically and graphs are displayed accordingly.
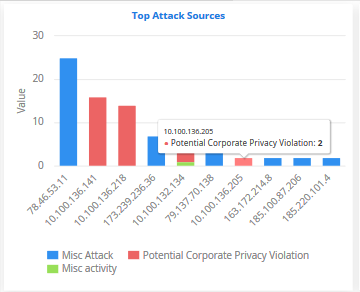
Top Attack Sources
The addresses from which most attacks originated, and the type of attack.
- Addresses are shown on the X-axis. Quantity of attacks are shown on the Y-axis. Attack types are color-coded and listed in the legend below the chart.
- Place your mouse cursor over an event to view attack details.
- You can hide/view a bar by clicking its name in the legend. The colored box beside an event name will be black if the bar graph for it is hidden.
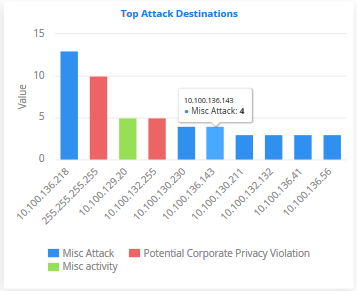
Top Attack
Destinations
- The systems that are most affected by the attacks
- Addresses are shown on the X axis. Quantity of attacks are shown on the Y axis.
- Place your mouse cursor over an event to view attack details. The colored box beside the event name will be black if the bar graph for it is hidden.
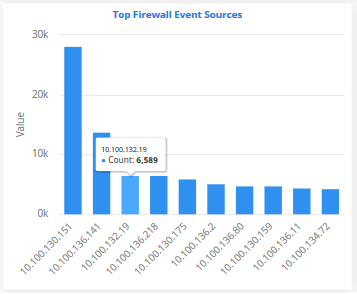
Top Firewall Event Sources
- The endpoints that are most affected by firewall attacks.
- IP addresses of systems from where the firewall events originated are shown on the X axis. Quantity of attack events are shown on the Y axis.
- Place your mouse cursor over an event to view attack details. The colored box beside the event name will be black if the bar graph for it is hidden.
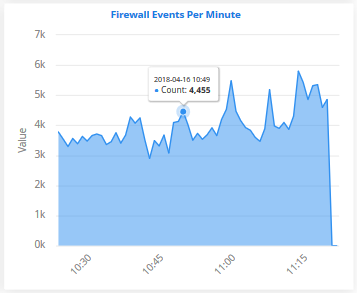
Firewall Events Per Minute
- The bar graph provides occurrence of firewall events per minute.
- For example, admins can get the time when the greatest number of firewall events occurs for a customer or if no events are coming from a customer, it may indicate malfunctioning communications with the agent or issue with log forwarding.
- Place your mouse cursor on a point in the graph to see more event details.
- cWatch generates alerts based on rules that defined in the 'Correlation Rules Management' interface
- These alerts are automatically assigned as incidents to the user responsible for the customer. See 'Administration' to know about assigning users to customers.
- Alerts that are assigned to users are called 'Incidents'. Incidents that are not closed are called 'Open Incidents'.
- Alerts that are not assigned are called 'Unassigned Incidents'.
- You can also add incidents manually in the 'Incidents' screen and assign them to users.
- See 'Manage Incidents' to learn more about incidents.
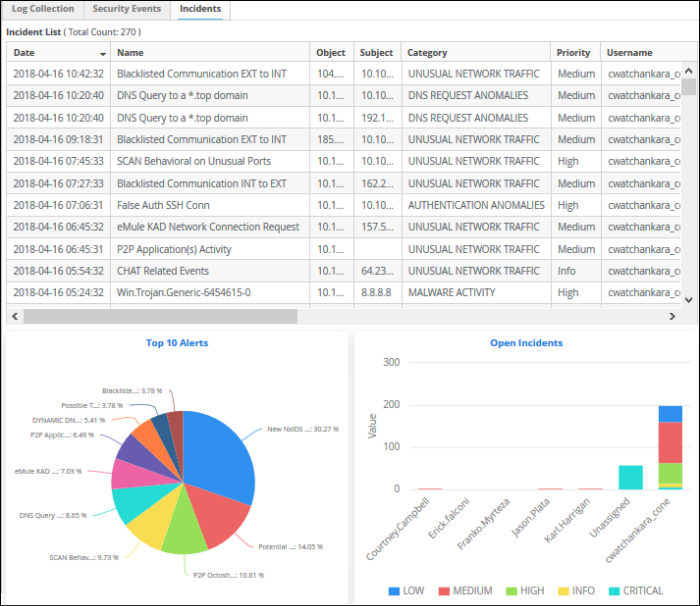
Incident List
The 'Incident List' table at the top displays a list of events with details like name, description and so on.
|
Incident List - Table of Column Descriptions |
|
|---|---|
|
Column Header |
Description |
|
Date |
Date and time of the incident. |
|
Name |
The rule that captured the event. |
|
Object |
The source IP of the assets. |
|
Subject |
The destination IP of the host. |
|
Category |
The incident type. For example, 'Malware activity' or 'Unusual network Traffic'. |
|
Customer |
Name of the affected customer. |
|
Username |
The administrator to whom the incident is assigned. |
|
Priority |
The severity of the event. Event priority can be specified in the 'Rule Creation' screen and in the 'Add Incident' screen. |
|
Status |
Shows whether the incident is 'Open', 'In-Progress', 'False Positive' or 'Closed'. |
|
Type |
Whether the event was automatically or manually generated. Automatic events are called 'Correlated'. Manual events are called 'Default'. |
|
Summary |
A short description of the incident. This description is provided when creating or editing the rule. |
|
Trigger Count |
The number of times the incident has occurred. |
|
Last Trigger Count |
Time and date that the rule was most recently breached. |
|
Identity |
Internal id of the incident. |
|
Report |
Whether the report for the selected incident is generated or not. |
You can sort the column items alphabetically/ascending or descending by clicking on the column header.
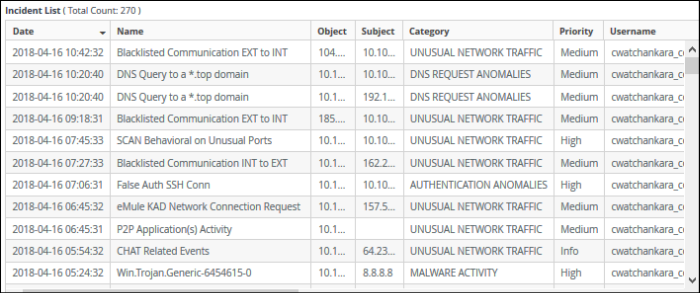
Top 10 Alerts
- Shows the 10 rules which generated the most alerts
- Place your mouse cursor over a chart slice to view more details.
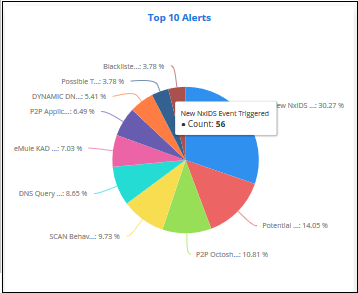
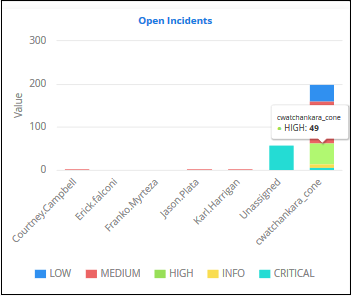
Open Incidents
- Shows unresolved incidents by assignee.
- Assignees are shown on the X axis. Quantity of attacks are shown on the Y axis.
- Place your mouse cursor over a bar to view the number of incidents, the severity of the incident and the user assigned.
- You can hide/view a graph bar by clicking the legend items
- The colored box beside the priority will be black if the bar graph for it is hidden. Click on it again to display the bar graph.