Protected Files
The Protected Files tab displays a list of files and file groups that are protected from access by other programs, especially malicious programs such as virus, Trojans and spyware. It is also useful for safeguarding very valuable files (spreadsheets, databases, documents) by denying anyone and any program the ability to modify the file - avoiding the possibility of accidental or deliberate sabotage. If a file is 'Protected' it can still be accessed and read by users, but not altered. A good example of a file that ought to be protected is the Windows 'hosts' file (c:/windows/system32/drivers/etc/hosts). Placing this in the 'Protected Files' area would allow web browsers to access and read from the file as per normal. However, should any process attempt to modify it then Comodo Client Security blocks this attempt and produce a 'Protected File Access' pop-up alert.
If you add a file to Protected Files, but want to allow trusted application to access it, then rules can be defined in HIPS Rulesets. Refer to the section Exceptions for more details about how to allow access to files placed in Protected Files.
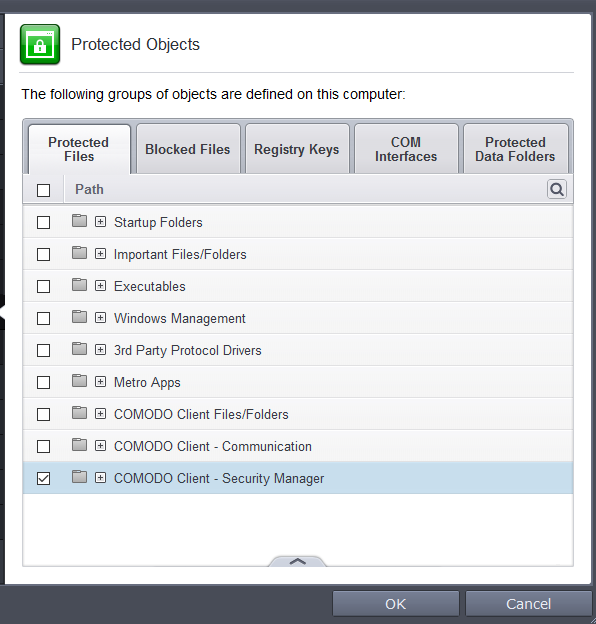
To open the 'Protected Files' screen, click 'Security Settings' > 'Advanced Protection' > 'Protected Objects' > then click the 'Protected Files' tab.
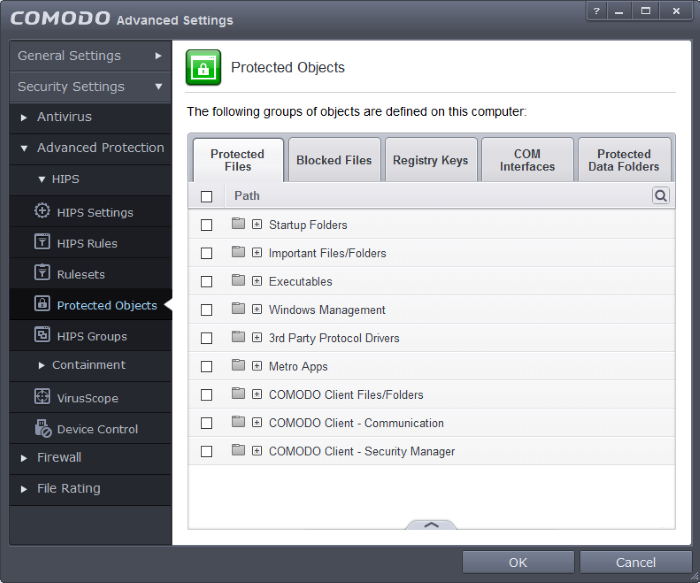
Clicking the handle at the bottom of the interface opens an options panel:
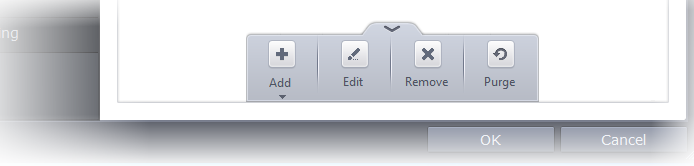
- Add – Allows you to add individual files, folders, programs, applications to Protected Files.
- Edit – Allows you to edit the path of the file or group of a selected item in the Protected Files interface.
- Remove - Deletes the currently highlighted file or file group.
- Purge - Runs a system check to verify that all the files listed are actually installed on the host machine at the path specified. If not, the file or the file group is removed, or 'purged', from the list.
 at the far right in the column header and entering the
file/group name in full or part. You can navigate through the
successive results by clicking the left and right arrows.
at the far right in the column header and entering the
file/group name in full or part. You can navigate through the
successive results by clicking the left and right arrows.
To manually add an individual file, folder, file group or process
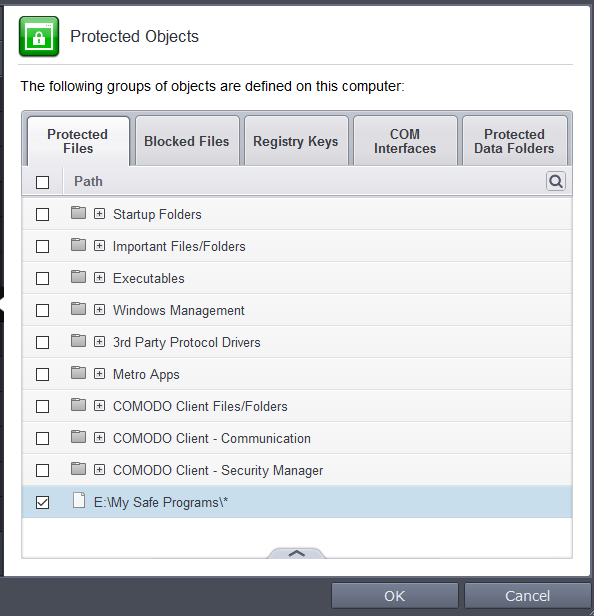
- Click the handle from the bottom center and select 'Add'.
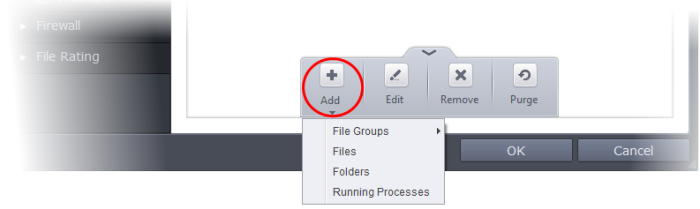
You can add the files by following methods:
Choosing File Groups allows you to add a category of pre-set files or folders. For example, selecting 'Executables' would enable you to exclude all files with the extensions .exe .dll .sys .ocx .bat .pif .scr .cpl . Other such categories available include 'Windows System Applications' , 'Windows Updater Applications' , 'Start Up Folders' and so on - each of which provide a fast and convenient way to apply a generic ruleset to important files and folders.
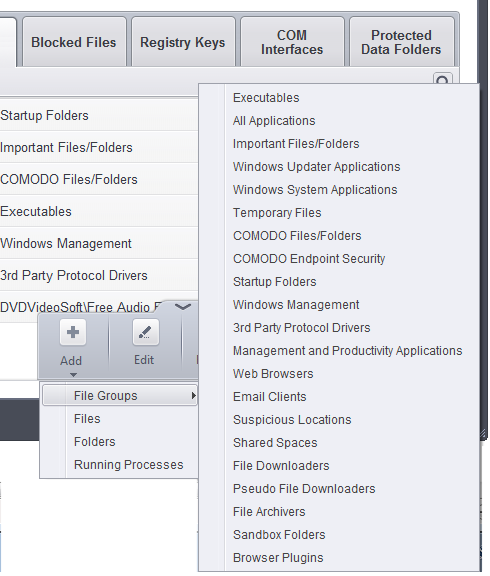
CCS ships with a set of predefined File Groups and can be viewed in Advanced Settings > File Rating > File Groups. You can also add new file groups here which will be displayed in the predefined list.
To add a file group to Protected Files, click Add > File Groups and select the type of File Group from the list.
The file group will be added to Protected Files.
- Repeat the process to add more file groups.
The items added to the Protected Files will be protected from access
by other programs.
Adding a Drive Partition/Folder
-
To add a folder, choose 'Folders' from the 'Add' drop-down.
The 'Browse for Folder' dialog will
appear.
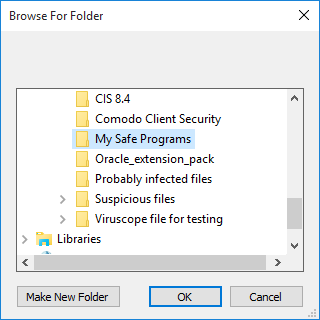
- Navigate to the drive partition or folder you want to add to Protected Files and click 'OK'
The drive partition/folder will be added to Excluded Paths.
- Repeat the process to add more folders. The items added to the Protected Files will be protected from access by other programs.
-
Choose 'Files' from the 'Add' drop-down.
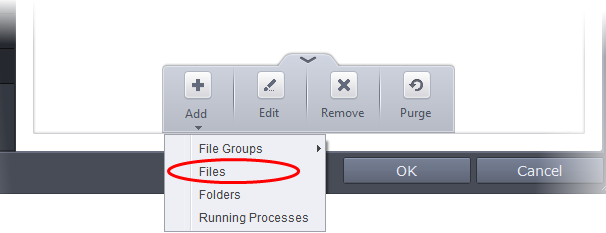
-
Navigate to the file you want to add to Protected Files in the 'Open' dialog and click 'Open'
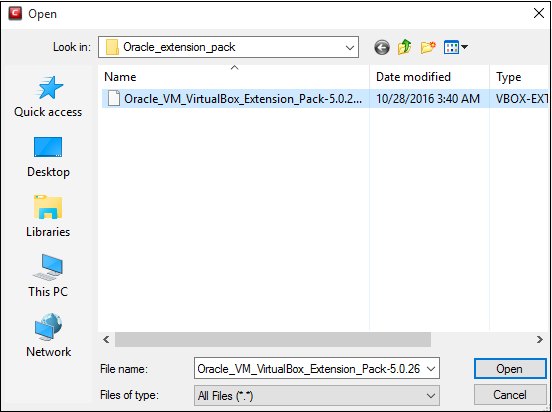
The file will be added to 'Protected
Files'.
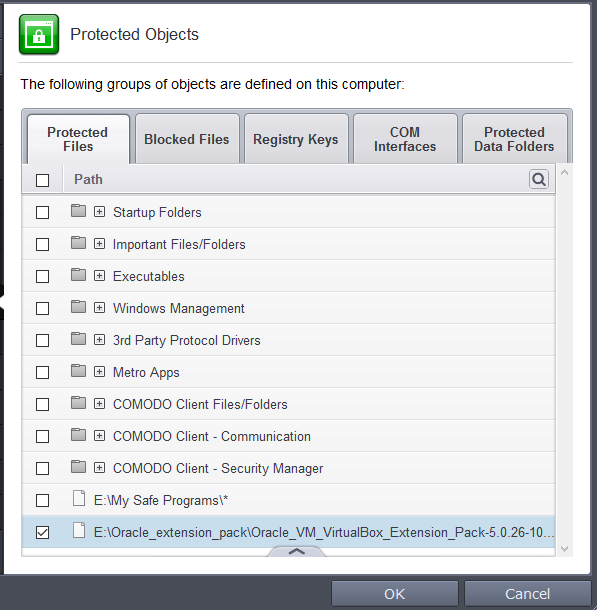
- Repeat the process to add more files. The
items added to the Protected Files will be protected from access by
other programs.
Adding an application from a running processes
-
Choose 'Running Processes' from the 'Add' drop-down
A list of currently running
processes in your computer will be displayed
-
Select the process, whose target application is to be added to Protected Files and click 'OK' from the Browse for Process dialog.
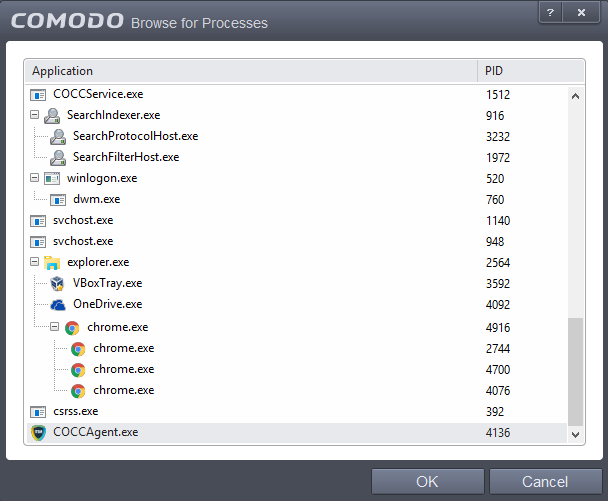
The application will be added to 'Protected Files'.
-
Repeat the process to add more files. The items added to the Protected Files will be protected from access by other programs.
To edit an item in the Protected Files list
-
Select the item from the list, click the up arrow from the bottom and select Edit. The 'Edit Property' dialog will appear.
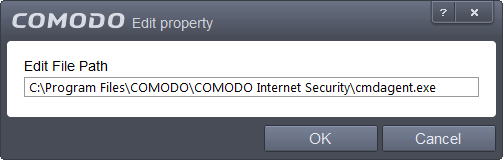
-
Edit the file path, if you have relocated the file and click 'OK'
To delete an item from Protected Files list
-
Select the item from the list, click the up arrow from the bottom and select 'Remove'.
The selected item will be deleted
from the protected files list. CCS will not generate alerts, if the
file or program is subjected to unauthorized access.
Users can choose to selectively allow another application (or file group) to modify a protected file by affording the appropriate Access Right in 'Active HIPS Rules' interface. A simplistic example would be the imaginary file 'Accounts.ods'. You would want the Open Office Calc program to be able to modify this file as you are working on it, but you would not want it to be accessed by a potential malicious program. You would first add the spreadsheet to the 'Protected Files' area. Once added to 'Protected Files', you would go into 'Active HIPS Rules' and create an exception for 'scalc' so that it alone could modify 'Accounts.ods'.
-
First add Accounts.ods to Protected Files area.
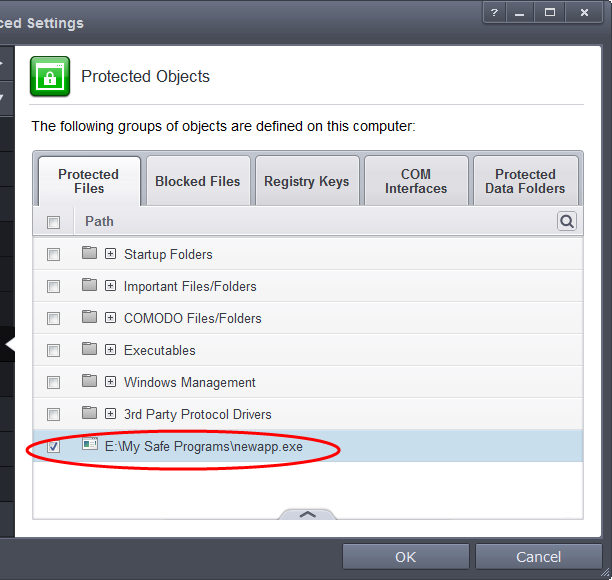
-
Then go to HIPS Rules interface and add it to the list of applications (Click 'Add' > select User Ruleset > Allowed Application > Browse and select the file).
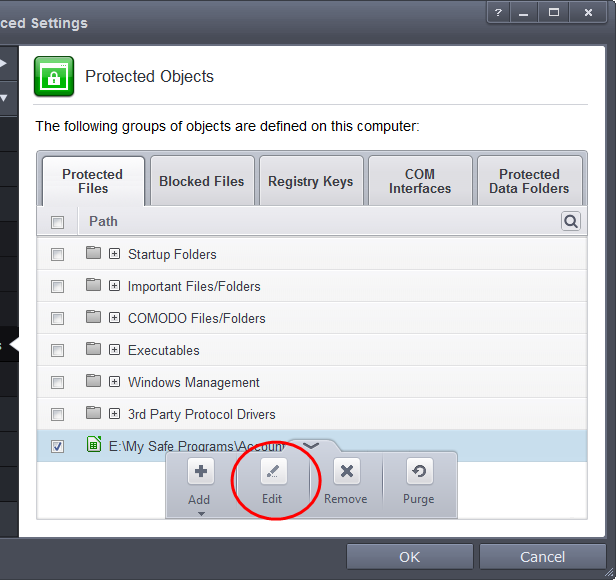
- Select the file, click the up arrow and choose 'Edit'.
- In the HIPS Rule interface, select 'Use a custom ruleset'.
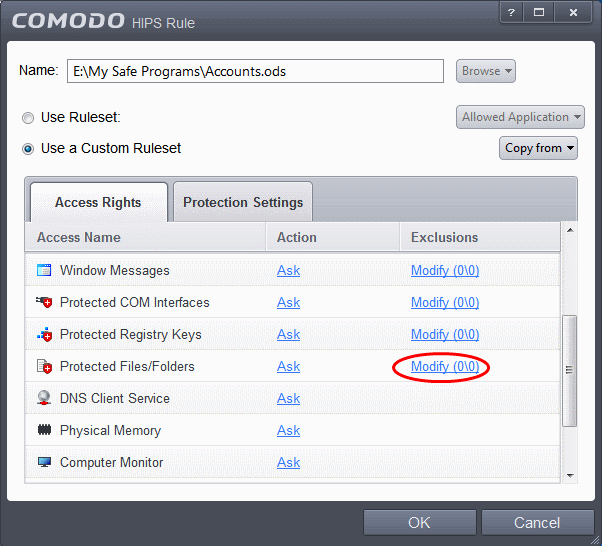
- Under the 'Access Rights' tab, click the link 'Modify' beside the entry Protected Files/Folders. The Protected Files and Folders interface will appear.
- Under the 'Allowed Files/Folders' tab, click the handle, choose 'Add' > 'Files' and add scalc.exe as exceptions to the 'Ask' or 'Block' rule in the 'Access Rights'.
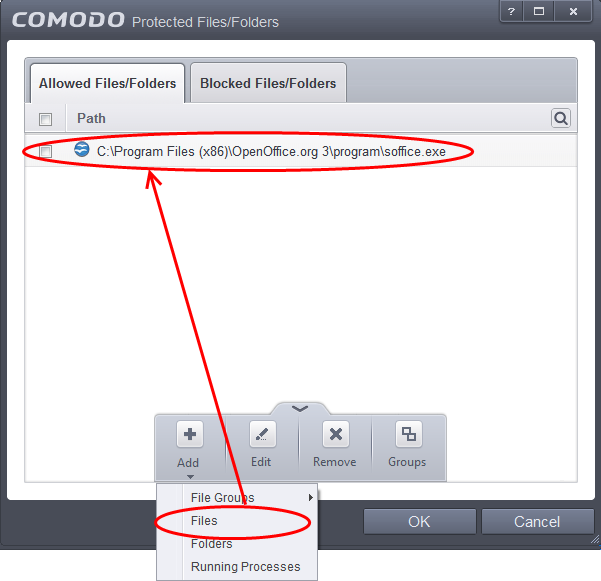
Another
example of where protected files should be given selective access is
the Windows system directory at 'c:/windows/system32'. Files in this
folder should be off-limits to modification by anything except
certain, Trusted, applications like Windows Updater Applications. In
this case, you would add the directory c:/windows/system32* to the
'Protected Files area (* = all files in this directory). Next go to 'HIPS Rules',
locate the file group 'Windows Updater Applications' in the list and
follow the same process outlined above to create an exception for
that group of executables.



