Scan Results
- Scan results are automatically shown in the CFA interface after a scan finishes.
- The scan checks the reputation of each file against Comodo's file-lookup service, a huge database of blacklisted and white-listed files.
- Blacklisted files are flagged as malicious and should be deleted or quarantined. White-listed files are safe to run.
- If a file is not on either the blacklist or whitelist, then it is categorized as 'unknown'. Unknown files are automatically submitted to Comodo Valkyrie where they will undergo a range of static and dynamic behavioral tests to discover whether they are malicious or not.
- The CFA interface displays results of both files analyzed by Forensic Analysis and Valkyrie analysis:
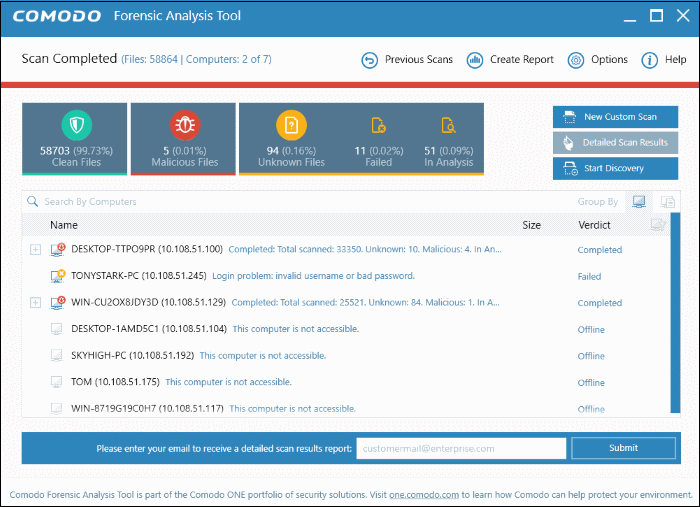
- Scan results are listed for each computer. Each row has a quick summary of the scan results, including total files scanned and how many were malicious or unknown.
- Click the plus symbol beside an endpoint to view unknown and malicious files detected by the scan.
- Click
the icons next to 'Group By' to view results by 'Computer' or by
'Files'.

- Expand an endpoint's results then click the 'Name', 'Size' or 'Verdict' column headers to sort files in order of the column name.
- To search for a particular endpoint, enter its name or IP address in the 'Search' box at the top right. Clear the search box to display all endpoints again.
- Click the funnel icon on the right
 to filter
endpoints by scan status:
to filter
endpoints by scan status:
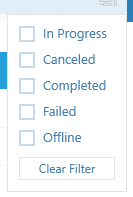
- In Progress – Endpoints which have a scan currently running
- Canceled - Endpoints on which a scan was aborted
- Completed - Endpoints on which a scan has successfully finished
- Failed - Endpoints on which CFA was unable to complete a scan
- Offline - Endpoints which are not responding at this time
- If the filter icon is blue
then filter(s) are applied. Click 'Clear Filter' to display all endpoints again.
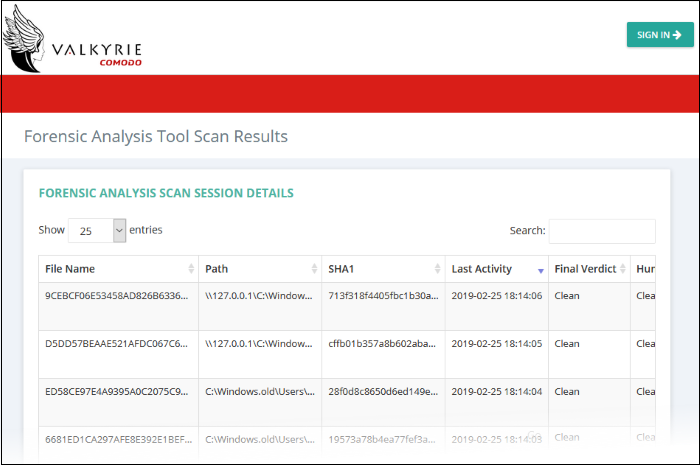
- Unknown files are uploaded to Valkyrie for analysis. You can view the results of the Valkyrie analysis by clicking the 'Detailed Scan Results' button. This will open the Valkyrie results page:
|
Valkyrie Detailed Analysis Results - Table of Column Descriptions |
|
|---|---|
|
Column Header |
Description |
|
File Name |
The name of the submitted file. |
|
Path |
The IP of the endpoint and the file's path details. |
|
SHA1 |
The SHA1 hash value of the file. |
|
Last Activity |
The date and time the last activity of analysis was performed. |
|
Final Verdict |
The Valkyrie dynamic and static analysis results for the file. The results available are:
|
|
Human Expert Verdict |
The results of the file after Human expert analysis:
|
|
Human Expert Analysis Status |
Indicates the status of files submitted for Human Expert analysis. The statuses are:
|
|
Request Type |
Indicates the type of input given to receive Valkyrie results.
|
|
Actions |
The available actions are:
|
You can also view detailed Valkyrie results in the reports area. See Reports for more details.




 - View Info - You can
view the complete details of the results for the file such as
summary, static analysis, dynamic analysis and file details.
- View Info - You can
view the complete details of the results for the file such as
summary, static analysis, dynamic analysis and file details.  - Download Automatic
Analysis Report - Allows you to download the report in PDF format.
- Download Automatic
Analysis Report - Allows you to download the report in PDF format.  - View Virus Total
Result - Takes you to the Virus Total website that displays its
results for the file.
- View Virus Total
Result - Takes you to the Virus Total website that displays its
results for the file.  - Send to Manual
Analysis - Allows you to submit the file for manual analysis by
Comodo technicians.
- Send to Manual
Analysis - Allows you to submit the file for manual analysis by
Comodo technicians.