Miscellaneous Settings
-
Click 'Assets' > 'Configuration Templates' > 'Profiles'
-
Open the Windows profile you want to work on
-
Click the 'Miscellaneous' tab then 'Edit', if it has already been added to the profile
OR
-
Click 'Add Profile Section' > 'Miscellaneous' if it hasn't yet been added
Click 'Assets' > 'Configuration Templates' > 'Profiles'
Open the Windows profile you want to work on
-
Click the 'Miscellaneous' tab then 'Edit', if it has already been added to the profile
OR
-
Click 'Add Profile Section' > 'Miscellaneous' if it hasn't yet been added
The 'Miscellaneous' settings screen opens:

-
Detect shellcode injections:
A shellcode injection is an attack which exploits software vulnerabilities to give attackers control of a compromised machine.
For example, shellcode attacks are often used to create buffer-overflows on victim machines. Enable this setting to turn-on buffer overflow protection.
By default, Xcitium Client Security (XCS) monitors all applications to make sure they do not suffer shellcode attacks.
However, you may want to omit certain applications from protection for compatibility reasons. Click the 'Exclusions' link to do this.
The process to add exclusions is similar to that explained in Containment Settings.
Background: A buffer overflow is an anomalous condition where a process/executable attempts to store data beyond the boundaries of a fixed-length buffer. The result is that the extra data overwrites adjacent memory locations. The overwritten data may include other buffers, variables and program flow data, and may cause a process to crash or produce incorrect results. As such, buffer overflows cause many software vulnerabilities and are the basis of many exploits.
-
Apply the selected action to...' - XCS will monitor registry entries related to Windows services, auto-run items and scheduled tasks. If any entries are created or modified by unrecognized files/scripts, they will handled per the action chosen. (Default = Enabled)
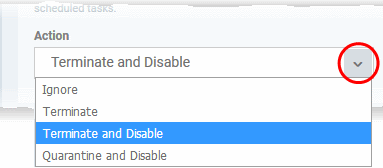
Xcitium recommends this setting is left enabled (Default = Enabled).
-
Apply the selected signature level while.... - XCS identifies untrusted DLLs, apps, portable executables (PE) and autoruns launched before XCS starts on the endpoint. These may expose the endpoint to a danger if those items turn to be malicious. (Default = Disabled)
XCS checks whether startup items are signed by a trusted authority and marks them as trusted or untrusted. The flag is used at next restart to allow or block the item.
You can choose how strict the certificate check should be:
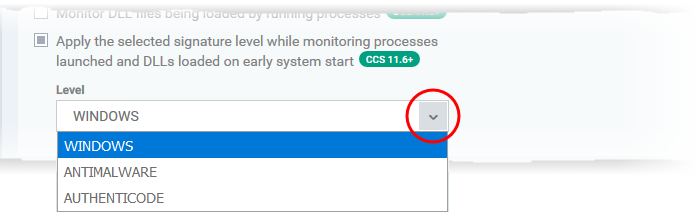
Windows- Only items signed by Microsoft certificates are marked as trusted
Antimalware - Trusts files signed by either Microsoft or Antimalware certificates
Authenticode - Flags all signed files as trusted
- Monitor DLL files being loaded by running processes - XCS monitors the DLL files loaded to system memory, by processes that are currently running on the endpoint (Default = Disabled).
If enabled, XCS runs a file rating scan on each DLL loaded to identify its trust rating.
The trust rating is reported to Xcitium. Files with an Unrecognized' rating are submitted to Valkyrie for analysis
Auto-block unknown DLL files(s) from being loaded by processes - XCS will block automatically if it detect the process loads unknown DLL file(s) (Default = Disabled)
1) If the 'Monitor DLL files being loaded by running processes' option is not enabled, the 'Auto-block unknown DLL files(s) from being loaded by processes' option should be displayed as disabled, it won't be selectable.
Click 'OK' to save your settings.



