Unknown Files: The Auto - Sandboxing and Scanning Processes
- When an executable is first run it passes through the following CIS security inspections:
- Antivirus scan
- HIPS Heuristic check
- Buffer Overflow check
- If the processes above determine that the file is malware then the user is alerted and the file is quarantined or deleted
- An application can become recognized as 'safe' by CIS (and therefore not auto-sandboxed or scanned in the cloud) in the following ways:
- Because it is on the local Comodo White List of known safe applications
- Because the user has added the application to the local 'Trusted Files'
- By the user granting the installer elevated privileges (CIS detects if an executable requires administrative privileges. If it does, it asks the user. If they choose to trust, CIS regards the installer and all files generated by the installer as safe)
- Additionally, a file is not auto-sandboxed or sent for analysis in the cloud if it is defined as an Installer or Updater in HIPS Ruleset (See Active HIPS Rules for more details)
- Cloud Scanning Part 1
Files and processes that pass the security inspections above but are not yet recognized as 'safe' (white-listed) are 'Unrecognized' files. In order to try to establish whether a file is safe or not, CIS will first consult Comodo's File Look-Up Server (FLS) to check the very latest signature databases:
- A digital hash of the unrecognized process or file is created.
- These hashes are uploaded to the FLS to check whether the signature of the file is present on the latest databases. This database contains the latest, global black list of the signatures of all known malware and a white list of the signatures of the 'safe' files.
- First, our servers check these hashes against the latest available black-list
- If the hash is discovered on this blacklist then it is malware
- The result is sent back to the local installation of CIS
- If the hash is not on the latest black-list, it's signature is checked against the latest white-list
- If the hash is discovered on this white-list then it is trusted
- The result is sent back to local installation of CIS
- The local white-list is updated
- The FLS checks detailed above are near instantaneous.
- Sandbox and Cloud Scanning Part 2
If the hash is not on the latest black-list or white-list then it remains as 'unrecognized'. CIS simultaneously takes two distinct but complementary actions -
(1) It will run the unrecognized file in the auto-sandbox so that it cannot access important operating system files or damage your computer, and
(2) It will leverage Comodo's Cloud Scanning technology to determine whether the file behaves in a malicious fashion.
- Unrecognized files and applications will be isolated and run in the auto-sandbox. CIS will alert the user that it is going to run the application in the sandbox.
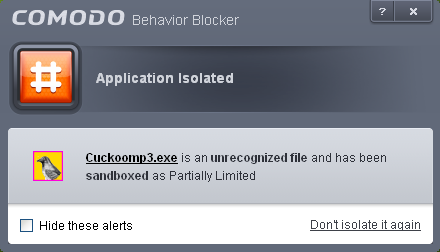
-
By defaullt, auto-sandboxed applications are run with 'Partially Limited' restrictions.
More detail: Auto-sandboxed applications are allowed to run under a specific set of conditions or privileges. In CIS, these are known as 'Restriction Levels'. In part, auto-sandbox restriction levels are implemented by enforcing or relaxing the native access rights that Windows can grant to an application. There are six levels - Partially Limited, Limited, Restricted, Untrusted, Blocked and Fully Virtualized. 'Partially Limited' is the default restriction level for auto-sandboxed applications, but you can change this to a different level in the Behavior Blocker Settings panel:
-
Partially Limited - The application is allowed to access all operating system files and resources like the clipboard. Modification of protected files/registry keys is not allowed. Privileged operations like loading drivers or debugging other applications are also not allowed.(Default)
-
Limited - Only selected operating system resources can be accessed by the application. The application is not allowed to execute more than 10 processes at a time and is run without Administrator account privileges.
-
Restricted - The application is allowed to access very few operating system resources. The application is not allowed to execute more than 10 processes at a time and is run with very limited access rights. Some applications, like computer games, may not work properly under this setting.
-
Untrusted - The application is not allowed to access any operating system resources. The application is not allowed to execute more than 10 processes at a time and is run with very limited access rights. Some applications that require user interaction may not work properly under this setting.
-
Blocked - The application is not allowed to run at all.
-
Fully Virtualized - The application will be run in a virtual environment completely isolated from your operating system and files on the rest of your computer.
-
Unrecognized files are simultaneously uploaded to Comodo's Instant Malware Analysis servers for further checks:
-
Firstly, the files undergo another antivirus scan on our servers.
-
If the scan discovers the file to be malicious (for example, heuristics discover it is a brand new variant) then it is designated as malware. This result is sent back to the local installation of CIS and the local and global black-list is updated.
-
If the scan does not detect that the file is malicious then it passes onto the the next stage of inspection - behavior monitoring.
-
The behavior analysis system is a cloud based service that is used to help determine whether a file exhibits malicious behavior. Once submitted to the system, the unknown executable will be automatically run in a virtual environment and all actions that it takes will be monitored. For example, processes spawned, files and registry key modifications, host state changes and network activity will be recorded.
-
If these behaviors are found to be malicious then the signature of the executable is automatically added to the antivirus black list.
-
If no malicious behavior is recorded then the file is placed into 'Unrecognized Files' and will be submitted to our technicians for further checks. Note: Behavior Analysis can identify malicious files and add to the global black list, but it cannot declare that a file is 'safe'. The status of 'safe' can only be given to a file after more in-depth checks by our technicians.
-
In either case, the result is reported back to your CIS installation in approximately 15 minutes. If the executable was not found to be malicious then it will be run in the auto-sandbox. It will simultaneously be added to the 'Unrecognized Files' list and uploaded to our technicians for analysis. If it is discovered to be a threat then CIS will show an AV alert to the user. From this alert the user can opt to quarantine, clean (delete) or disinfect the malicious file. This new threat will be automatically added to the global black list database and therefore benefit all CIS users.



