Active HIPS Rules
The HIPS rules tab lists the different groups of applications installed in your system and the Rulesets applied to them. You can change the ruleset applied to selected applications and also create custom rulesets to be applied to selected applications.
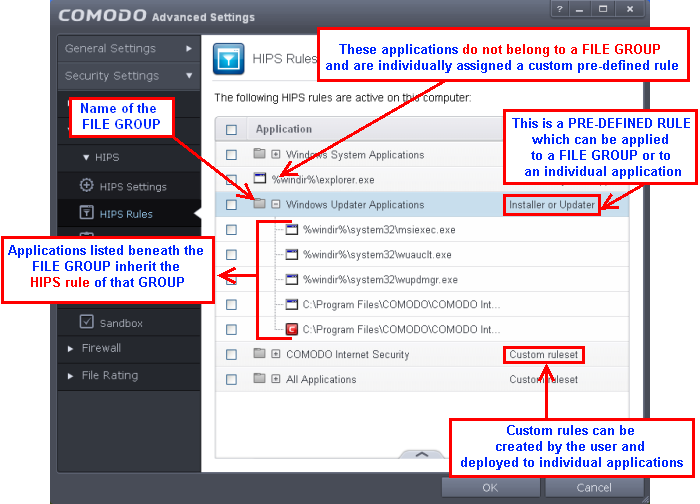
The first column, Application Name, displays a list of the applications on your system for which a HIPS ruleset has been deployed. If the application belongs to a file group, then all member applications assume the ruleset of the file group. The second column,Treat as, column displays the name of the HIPS ruleset assigned to the application or group of applications in column one.
You can use the search option to find a specific file or a company in the list.
To use the
search option, click the search icon  at the far right in the column
header.
at the far right in the column
header.
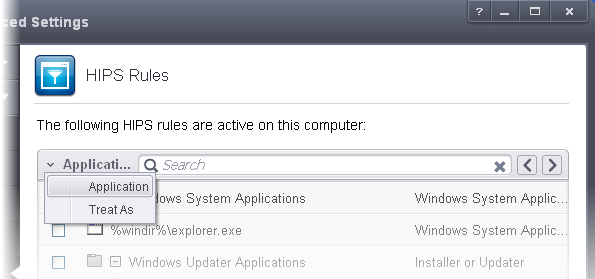
- Click the chevron on the left side of the column header and select the search criteria from the drop-down.
- Enter partly or fully the name of the item as per the selected criteria in the search field.
- Click the right or left arrow at the far right of the column header to begin the search.
- Click
the
 icon in the search field to close the search option.
icon in the search field to close the search option.
General Navigation:
Clicking the Up arrow at the bottom center of the interface opens an option panel with the following options:
- Add - Allows the user to Add a new Application to the list then create it's ruleset. See the section 'Creating or Modifying a HIPS Ruleset'.
- Edit - Allows the user to modify the HIPS rule of the selected application. See the section 'Creating or Modifying a HIPS Ruleset'.
- Remove - Deletes the selected ruleset.
|
Note: You cannot remove individual applications from a file group using this interface - you must use the 'File Groups' interface to do this. |
- Purge - Runs a system check to verify that all the applications for which rulesets are listed are actually installed on the host machine at the path specified. If not, the rule is removed, or 'purged', from the list.
Creating or Modifying a HIPS Ruleset
To begin defining a application's HIPS Ruleset
Step 1 - Select the application or file group that you wish the ruleset to apply to
If you wish to define a rule for a new application (i.e. one that is not already listed), click the handle from the HIPS Rules pane and select 'ADD'. This brings up the 'HIPS Rule' interface as shown below.
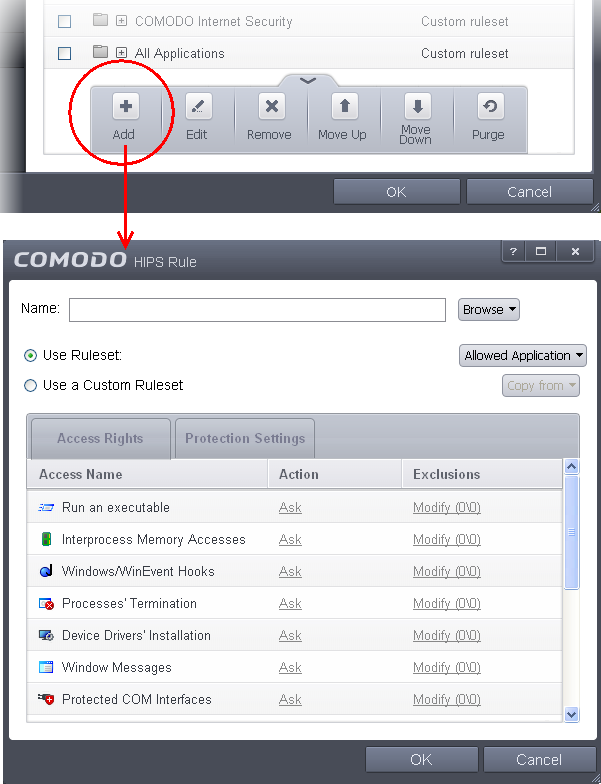
Because you are defining the HIPS rule settings for a new application, you can notice that the 'Name' box is blank. (If you were editing an existing rule instead, then this interface would show that application's name with installation path or application group's name.)
You now have 3 methods available to choose the application for which you wish to create a policy - File Groups; Applications and Running Processes.
-
File Groups - Choosing this option allows you to create a HIPS ruleset for a category of pre-set files or folders. For example, selecting 'Executables' would enable you to create a ruleset for all files with the extensions .exe .dll .sys .ocx .bat .pif .scr .cpl . Other such categories available include 'Windows System Applications' , 'Windows Updater Applications' , 'Start Up Folders' etc - each of which provide a fast and convenient way to apply a generic policy to important files and folders.
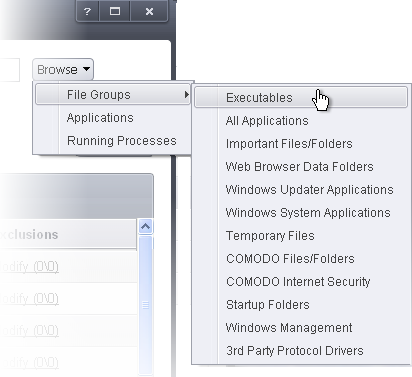
To view the file types and folders that are affected by choosing one of these options, you need to visit the 'File Groups' interface.
The ' File Groups interface can be accessed by the following method:
-
Navigate to Advanced Settings > Defense+ > HIPS > Protected Files, click the up arrow from the bottom of the interface and select 'Groups' from the options.
-
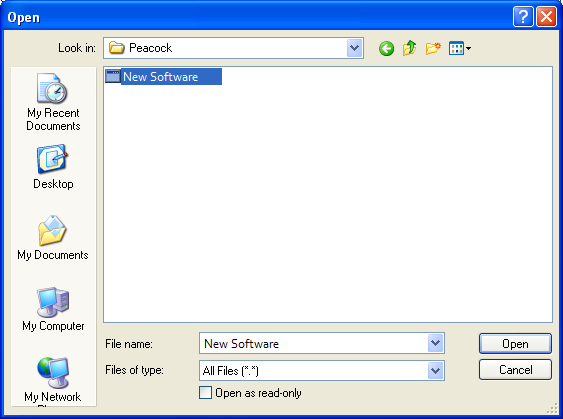
Applications - This option is the easiest for most users and simply allows you to browse to the location of the application for which you want to deploy the ruleset.
-
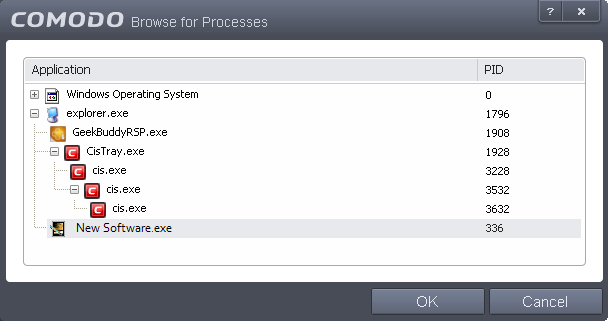
Running Processes - as the name suggests, this option allows you to create and deploy a ruleset for any process that is currently running on your PC.
Having selected the individual application, running process or file group, the next stage is to Configure the rules for this ruleset.
Step 2 - Configure the HIPS Ruleset for this application
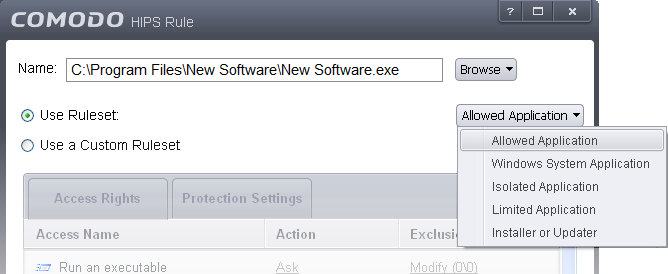
There are two broad options available for selecting a policy that applies to an application – Use Ruleset or Use a Custom Ruleset.
-
Use Ruleset - Selecting this option allows the user to quickly deploy an existing HIPS ruleset on to the target application. Choose the ruleset you wish to use from the drop down menu. In the example below, we have chosen 'Allowed Application'. The name of the ruleset you choose is displayed in the 'Treat As' column for that application in the HIPS Rules interface (Default = enabled).
|
Note on 'Installer or Updater' Rule :Applying the Predefined Ruleset 'Installer or Updater' for an application defines it as a trusted installer and all files created by the application will also be considered as trusted files. Some applications may have hidden code that could impair the security of your computer if allowed to create files of their own. Comodo advises you to use this Predefined Ruleset - 'Installer or Updater' with caution. On applying this ruleset to any application, an alert dialog will be displayed, describing the risks involved.
|
|
General Note:Predefined Rulesets, once chosen, cannot be modified directly from this interface - they can only be modified and defined using the 'Rulesets' interface. If you require the ability to add or modify settings for an specific application then you are effectively creating a new, custom policy and should choose the more flexible Use a Custom Ruleset option instead. |
-
Use a Custom Ruleset - designed for more experienced users, the 'Custom Ruleset' option enables full control over the configuration specific security policy and the parameters of each rule within that ruleset. The Custom ruleset has two main configuration areas - Access Rights and Protection Settings (Default = Disabled).
In simplistic terms 'Access Rights' determine what the application can do to other processes and objects whereas 'Protection Settings' determine what the application can have done to it by other processes.
-
Access Rights - The Process Access Rights tab allows you to determine what activities the applications in your custom ruleset are allowed to execute. These activities are called 'Access Names'.
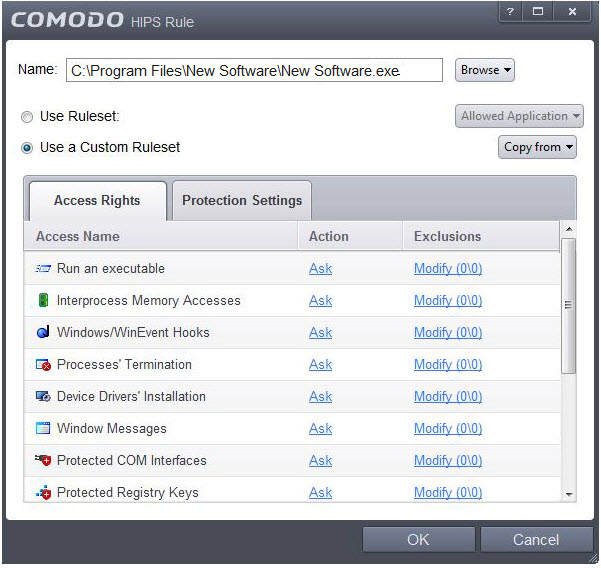
Refer to the section HIPS Behavior Settings > Activities to Monitor to view a list of definitions of the Action Names listed above and the implications of choosing the action from 'Ask', 'Allow' or 'Block' for each setting as shown below:
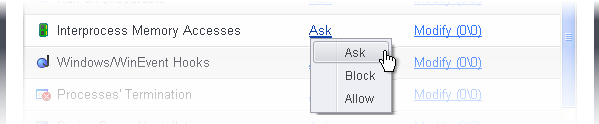
- Exceptions to your choice of 'Ask', 'Allow' or 'Block' can be specified for the ruleset by clicking the 'Modify' link on the right.
- Select the 'Allowed Applications' or 'Blocked Applications' tab depending on the type of exception you wish to create.
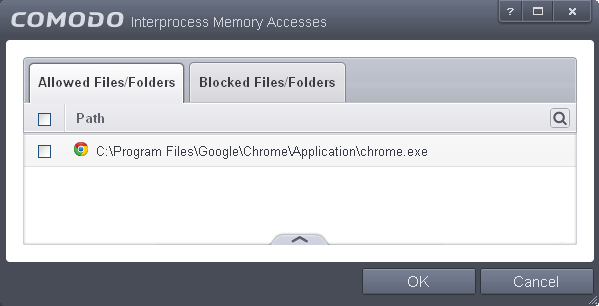
Clicking the handle and selecting 'Add' allows you to choose which applications or file groups you wish this exception to apply to. (click here for an explanation of available options).
In the example above, the default action for 'Interprocess Memory Access' is 'Ask'. This means HIPS will generate an alert asking your permission if 'New Software.exe' tries to modify the memory space of any other program. Clicking 'Modify' then adding 'opera.exe' to the 'Allowed Applications' tab creates an exception to this rule. New Software.exe can now modify the memory space of opera.exe.
-
Protection Settings - Protection Settings determine how protected the application or file group in your ruleset is against activities by other processes. These protections are called 'Protection Types'.
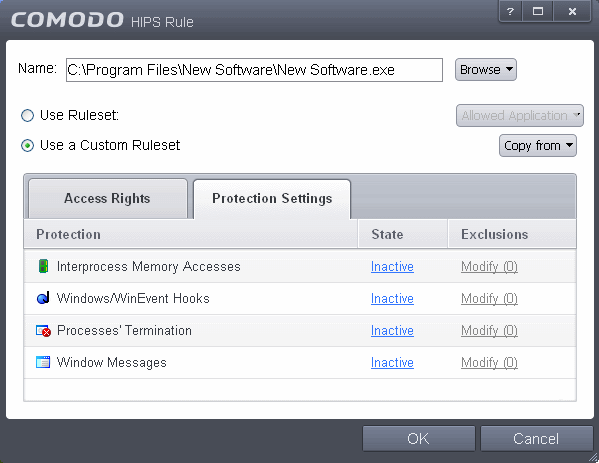
- Select 'Active' to enable monitoring and protect the application or file group against the process listed in the 'Protection Type' column. Select 'Inactive' to disable such protection.
Click here to view a list of definitions of the 'Protection Types' listed above and the implications of activating each setting.
Exceptions to your choice of 'Active' or 'Inactive' can be specified in the application's policy by clicking the 'Modify' link on the right.
-
Click 'OK' to confirm your settings.