Search and Filter Logs
You can run a simple filter of events by date, and use advanced filters to conduct more complex searches.
- Click 'Tasks' > 'Advanced Tasks' > 'View Logs'
OR
- Click ‘Logs’ in advanced view of the CIS home screen
- Select an event category from the drop-down at top-left
- Click 'Filter by Date and Time' to choose a specific period:
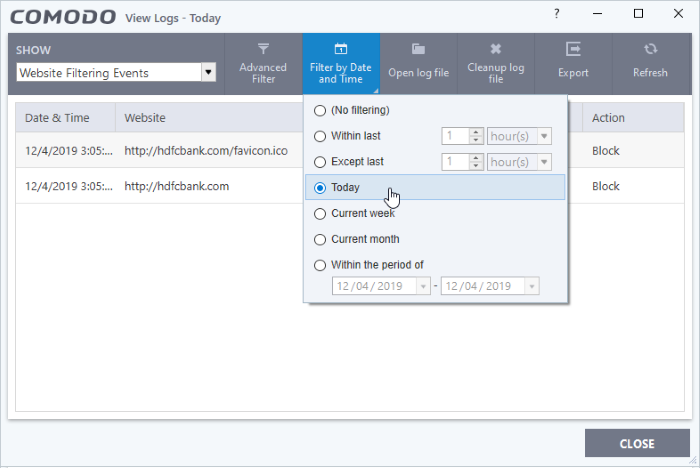
- No filtering - Show every event logged since CIS was installed. If you have cleared the logs since installation, this option shows all logs created since that clearance.
- Within last - Show all logs from a certain point in the past until the present time.
- Except last - Exclude all logs from a certain point in the past until the present time.
- Today - Show all events logged today, from 12:00 am to the current time.
- Current Week - Show all events logged from the previous Sunday to today.
- Current Month - Display all events logged from 1st of the current month to today.
- Within the period of - Show logs between a custom date range.
Advanced filters let you run complex queries based on a variety of criteria. Search parameters vary from module to module.
- Click 'Logs' in the CIS menu bar
- Select a module in the drop-down on the left
- Click ‘Advanced Filter’:
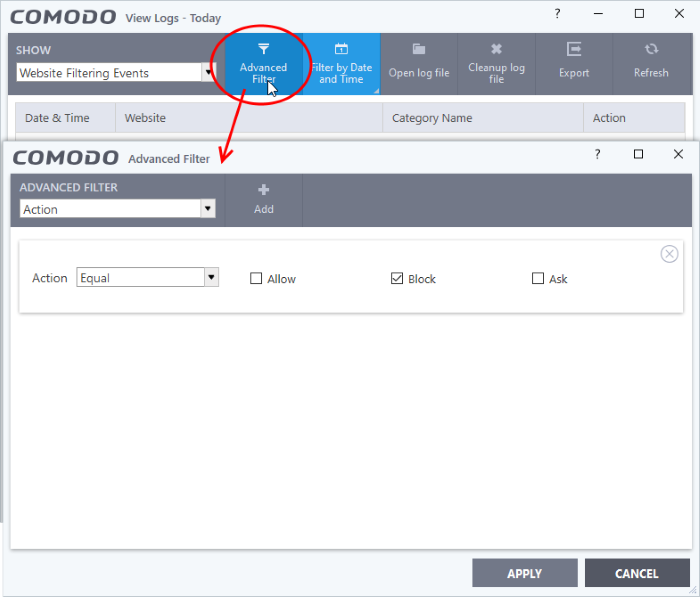
- Select a filter category at top-left then click ‘Add’
- Search parameters vary according to the filter category. You can include multiple filter categories to refine your search
Click the following links to view the options available with each module:
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Action |
Filter logs based on the action taken by CIS against the detected threat.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice. |
Select the filter parameter:
|
|
Location |
Filter the log entries related to events logged from a specific location.
|
For example, if you select 'Contains' option from the drop-down and enter the phrase 'C:/Program Files/' in the text field, then all events containing the entry 'C:/Program Files/' in the 'Location' field are displayed. |
|
Malware Name |
Filter the log entries related to specific malware. |
For example, if you choose 'Contains' from the drop-down and type 'siins' in the text field, then all events with 'siins' in the 'Malware Name' field are shown. |
|
Status |
Filter the log entries based on the success or failure of the action taken against the threat by CIS. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
|
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Action |
Filter logs based on the action taken by CIS against the detected threat.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
|
|
Location |
Filter the log entries related to events logged from a specific location. Select 'Contains' or 'Does Not Contain' option from the drop-down field |
For example, if you select 'Contains' option from the drop-down and enter the phrase 'C:/Program Files/' in the text field, then all events containing the entry 'C:/Program Files/' in the 'Location' field are displayed. |
|
Malware Name |
Filter the log entries related to specific malware. |
For example, if you choose 'Contains' from the drop-down and type 'siins' in the text field, then all events with 'siins' in the 'Malware Name' field are shown. |
|
Status |
Filter the log entries based on the success or
failure of the action taken against the threat by CIS.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
|
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Action |
Filter logs based on events according to the response (or action taken) by the firewall
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
|
|
Application |
Filter logs based on events propagated by a specific application |
For example, if you choose 'Contains' from and enter the phrase 'cuckoo' in the text field, then all FW events containing the entry 'cuckoo' in the 'Application' column are displayed |
|
Destination IP |
Filter logs based on events with a specific target IP address
|
For example, if you choose 'Contains' option from the drop-down, select IPv4 and enter 192.168.111.11 in the text field, then all events containing the entry '192.168.111.11' in the 'Destination IP' column will be displayed. |
|
Destination Port |
Filter logs based on events that involved a specific target port number. Select any one of the option the drop-down:
|
For example, if you choose 'Equal' option from the drop-down and enter 8080 in the text field, then all events containing the entry '8080' in the 'Destination Port' column will be displayed. |
|
Direction |
Filter logs based on events of inbound or outbound nature
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
For example, if you choose 'Equal' option from the drop-down and select the 'In' checkbox, then all inbound connection attempts will be displayed. |
|
Protocol |
Filter logs based on events that involved a specific protocol.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the filter parameter:
For example, if you choose 'Equal' option from the drop-down and select the 'TCP' checkbox, then all connection attempts involving TCP protocol will be displayed. |
|
Source IP |
Filter logs based on events that originated from a specific IP address
|
For example, if you choose 'Contains' then select IPv4 and enter 192.168.111.22 in the text field, then all events containing the entry '192.168.111.11' in the 'Source IP' column will be displayed. |
|
Source Port |
Filter logs based on events that involved a specific source port number Select any one of the option the drop-down:
|
For example, if you choose 'Equal' and enter 8080 in the text field, then all events containing the entry '8080' in the 'Source Port' column will be displayed. |
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Application |
Filter logs based on events propagated by a specific application. |
For example, if you choose 'Contains' from the drop-down and enter the phrase 'cuckoo' in the text field, then all events containing the entry 'cuckoo' in the 'Application' column are displayed. |
|
Action |
Filter logs based on events according to the response (or action taken) by HIPS
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the filter parameter:
For example, if you choose 'Equal' and select 'Create process', only events involving the creation of a process by applications are displayed. |
|
Target |
Filter logs based on events that involved a specified target application. |
For example, if you choose 'Contains' and enter the phrase 'svchost.exe' in the text field, then all events containing the entry 'svchost.exe' in the 'Target' column will be displayed. |
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Application |
Show events propagated by a specific application. |
For example, if you choose 'Contains' and enter the phrase 'pcflank' in the text field, then all events containing the entry 'pcflank' in the 'Application' column are displayed. |
|
Rating |
Show events
which concern files that have a specific trust-rating. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice.
|
Select the filter parameter:
For example, if you choose 'Equal' and select the 'Unrecognized' file rating, only the containment events involving applications that are categorized as 'Unrecognized' are displayed. |
|
Action |
Show events where a specific action was applied to the file by CIS.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the restriction level(s) applied by the container to the applications, either automatically of or chosen by the user from the alert.
For example, if you choose 'Equal' from the drop-down and select 'Run Virtually', only the events of applications that are run inside the container are displayed. |
|
Contained by |
Show events where the file was isolated by a specific module or user.
Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
Select the source(s) by which the applications were contained.
For example, if you choose 'Contains' and select the 'User' checkbox, then only events involving applications that were manually run inside the container are displayed. |
|
Parent Process |
Show files contained based on its source process. |
For example, if you choose 'Contains' and enter the phrase 'RuntimeBroker.exe' in the text field, then all events containing the entry 'RuntimeBroker.exe' in the 'Parent Process' column are displayed. |
|
Parent Process ID |
Show events created by a source process ID. Select 'Contains' or 'Does Not Contain' from the drop-down menu. |
For example, if you choose 'Contains' and enter the ID '2612' in the text field, then all events containing the entry '2612' in the 'Parent Process ID' column will be displayed. |
|
Parent Process Hash |
Show events where items was
contained based on its source process(es) specified by hash
value(s) of executable file(s) associated with the source
process(es). Select 'Contains' or 'Does Not Contain' from the drop-down menu. |
|
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Website |
Show only events that involved a specific website. Select 'Contains' or 'Does Not Contain' from the drop-down menu. |
For example, if you choose 'Contains' option from the drop-down and enter the phrase 'facebook.com' in the text field, then all events that involve the website 'facebook.com' in the 'Website' column are displayed. |
|
Category Name |
Show events that involved websites which are covered by a website filtering category. |
For example, if you choose 'Contains' and enter the phrase 'Malware Sites' in the text field, then all events involving websites in the 'Malware Sites' category are displayed. |
|
Action |
Show only events that involved a specific response by CIS.
Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the action(s) to filter the logs involving those action(s).
For example, if you choose 'Equal' and 'Block', then only events where websites blocked are displayed. |
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Name |
Filter the entries based on the type of the device. |
For example, if you choose 'Contains' and type 'USB Input Device' in the text field, you will see logs related to USB input devices like keyboards, mice and finger print scanners. |
|
Identifier |
Filter entries based on the device ID of the external device. |
For example if you have chosen 'Contains' and entered 'USBVID_0627&PID_0001', in the text field only those log entries related to external devices whose device ID contains the string are displayed. |
|
Class |
Filter the entries based on the GUID of the device |
For example, if you select 'Contains' option from the drop-down field and enter '4D36E967', then all events containing the entry '4D36E967' in the 'Class' field are displayed.. |
|
State |
Filter events based on whether the device connection attempt was allowed or blocked. |
Select the parameter to refine your search.
|
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Type |
Filter entries based on the class of autorun. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the parameter(s)
|
|
Location |
Filter entries based on application path. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
For example if you have chosen 'Contains' and entered 'C:/Program Files (x86)/Cuckoo Files/Cuckoo.exe in the text field, then only log entries with the same value in the 'Path' column are displayed. |
|
Modifier |
Filter logs by the file or user that launched the event. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice. |
For example if you choose 'Contains' and enter 'C:/Users/tester/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/UnknownAppUI3.exe' in the text field, then only log entries with the same value in the 'Path' column will be displayed. |
|
Action |
Filter the events based on CIS response to the detected threat. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice. |
|
|
Detected By |
Filter the entries based on the CIS component that discovered the threat. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the specific filter parameter to refine your search.
|
|
Status |
Filter the entries based on the success or failure of the action taken against the threat by CIS. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice |
Select the specific filter parameter to refine your search.
|
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Advice |
Filter entries by the security recommendation in the alert. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' will invert your selected choice. |
For example, choose 'Contains' and enter the phrase 'you can safely allow this request' in the text field. |
|
Answer |
Filter the events based on what action the user selected at the alert. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the parameter to refine your search.
For example, if you choose 'Equal' from the drop-down and select the 'Add to exclusions' checkbox, only the alerts where you answered 'Ignore' > 'Ignore and Add to exclusions' are displayed. |
|
Answered |
Filter logs based on the date the user answered the alerts. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
For example, if you select 'Equal' and select '07/31/2017', only alerts answered on 07/31/2017 are displayed. |
|
Description |
Filter the entries based on the
description of the attempt displayed in the alert. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
For example, if you select 'Contains' from the drop-down and enter 'connect to the internet', only the log entries of firewall alerts that contain the phrase 'connect to the internet' in the description are displayed. |
|
Option |
Filter the log entries where the user selected an additional options like 'Remember my answer', 'Submit as False Positive' from the alert. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the specific filter parameters to refine your search.
For example, if you choose 'Equal' from the drop-down and select 'Remember' from the checkbox options, only the log entries of alerts for which 'Remember my answer' option was selected are displayed. |
|
Treat as |
Filter events where the user chose specific actions on the alert. For example, 'treat as a safe application', 'treat as an installer' and so on. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
For example, if you have chosen 'Contains' from the drop-down and entered 'Installer' in the text field, only the log entries containing the phrase 'Installer' in the 'Treat As' column are displayed. |
|
Alert Type |
Filter the log entries based on the CIS component that triggered the alert. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the specific filter parameters to refine your search.
For example, if you select 'Equal' from the drop-down and select 'Antivirus Alert' checkbox, only the log of antivirus alerts are displayed. |
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Code |
Filter the entries based on specified error code. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
For example, if you have select 'Equal' and entered '0x80004004' in the text field, then only entries containing the value '0x80004004' in the 'Code' column are displayed. |
|
Completed |
Filter events based on tasks successfully finished on the specified date. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
For example, if you choose 'Equal' and select '08/01/2019', only the logs of tasks completed on 08/01/2019' are displayed. |
|
Parameter |
Filter the entries based on the
specified parameter. A 'parameter' is a sub-type of the main task
type. For example, 'Quick Scan' and 'Rating Scan' are both
parameters of the main task type 'Antivirus Scan'. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
For example, if you choose 'Contains' option from the drop-down and enter the phrase 'Quick Scan' in the text field, then only the entries of 'Antivirus Scan Tasks' with the scan parameter 'Quick Scan' are displayed. |
|
Type |
Filter the entries based on the CIS tasks category. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the specific filter parameters to refine your search.
|
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Location |
Filter the entries based on the file path whose trust rating was changed. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
For example if you have chosen 'Contains' and entered 'C:/Program Files (x86)/Cuckoo Files/Cuckoo.exe in the text field, then only log entries with the same value in the 'Path' column are displayed. |
|
Modifier |
Filter events based on who changed the file rating. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the filter parameter to refine your search
For example, if you select 'Equal' from the drop-down and select 'User' checkbox, only logs of changes done by the users are displayed. |
|
Action |
Filter the entries based on the file activity. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the filter parameter to refine your search
For example, if you select 'Equal' from the drop-down and select 'Removed' checkbox, only the logs of files that were removed from the file list are displayed. |
|
Rating Source |
Filter the entries by who provided the file rating Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
Ratings can be provided by:
|
|
Old Rating |
Filter the entries by who provided the file rating Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
Select the filter parameter to refine your search
For example, if you select 'Contains' from the drop-down and select 'Unrecognized' checkbox, only the logs of files that are rated as 'Unrecognized' in the 'Old Rating' column are displayed. |
|
New Rating |
Filter logs by the trust rating of files after the change Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
Select the filter parameter to refine your search
For example, if you select 'Contains' from the drop-down and select 'Malicious' checkbox, only the logs of files that are rated as 'Malicious' in the 'New Rating' column are displayed. |
|
File Hash |
Filter logs by hash value Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice |
|
Vendor List Changes
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Vendor |
Filter logs by the software publisher name whose trust rating was changed. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
Type the name of the vendor in full or part in the text field. For example if you choose 'Contains' and enter ‘Digital’ in the text field, only those log entries related to the vendors who has contain ‘Digital’ as a part in their name are displayed. |
|
Modifier |
Filter logs by who changed the vendor rating. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' will invert your choice. |
Select the filter parameter to refine your search
For example, if you select 'Equal' from the drop-down and select 'User' checkbox, only logs of changes done by the users are displayed. |
|
Action |
Filter logs by the type of change made to the vendor list. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice |
Possible actions:
For example, if you select 'Equal' from the drop-down and select 'Removed' checkbox, only the logs of vendors that were removed from the vendor list are displayed. |
|
Property |
Filter logs by the entity that provided the vendor rating. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
Entities that can provide trust ratings:
For example, if you select 'Equal' from the drop-down and select 'User Rating' checkbox, only the logs of vendors that were rated by users are displayed. |
|
Old Rating |
Filter logs by the trust rating of the vendor before the change Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
Select the filter parameter to refine your search
For example, if you select 'Contains' from the drop-down and select 'Unrecognized' checkbox, only the logs of vendors that are rated as 'Unrecognized' in the 'Old Rating' column are displayed. |
|
New Rating |
Filter logs by the vendor’s trust rating after the change. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
Possible new trust ratings are:
For example, if you select 'Contains' from the drop-down and select 'Malicious' checkbox, only the logs of vendors that are rated as 'Malicious' in the 'New Rating' column are displayed. |
Trusted
Certificate Authorities
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Vendor |
Filter logs by the software publisher name whose trust rating was changed. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice. |
Type the name of the vendor in full or part in the text field. For example if you choose 'Contains' and enter ‘Digital’ in the text field, only those log entries related to the vendors who has contain ‘Digital’ as a part in their name are displayed. |
|
Modifier |
Filter logs by who changed the trusted certificate authorities rating Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Select the filter parameter to refine your search.
For example, if you select 'Equal' from the drop-down and select 'User' checkbox, only logs of changes done by the users are displayed. |
|
Action |
Filter logs by the type of change made to the trusted certificate authorities list. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Possible actions:
For example, if you select 'Equal' from the drop-down and select 'Removed' checkbox, only the logs of trusted certificate authorities that were removed from the vendor list are displayed. |
|
Property |
Filter logs by the entity that provided the trusted certificate authorities rating Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice. |
Entities that can provide trust ratings:
For example, if you select 'Equal' from the drop-down and select 'User Rating' checkbox, only the logs of trusted certificate authorities that were rated by users are displayed. |
|
Old Rating |
Filter logs by the trust rating of the trusted certificate authorities before the change. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your choice. |
Select the filter parameter to refine your search.
For example, if you select 'Contains' from the drop-down and select 'Unrecognized' checkbox, only the logs of trusted certificate authorities that are rated as 'Unrecognized' in the 'Old Rating' column are displayed. |
|
New Rating |
Filter logs by the trusted certificate authorities's trust rating after the change. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain’ inverts your choice. |
Possible new trust ratings are:
For example, if you select 'Contains' from the drop-down and select 'Malicious' checkbox, only the logs of trusted certificate authorities that are rated as 'Malicious' in the 'New Rating' column are displayed. |
Configuration Changes
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Action |
Filter logs by the type of change that was made. For example, rule modified, file exclusion created. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Options are:
|
|
Modifier |
Filter events based on who changed the configuration such as the user, administrator and response given to an alert. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
The possible modifiers are:
For example, if you select 'Equal' from the drop-down and select 'User' checkbox, only logs of changes done by the users are displayed. |
|
Name |
Filter the entries based on object label that was affected by the configuration change, for example, Shared Spaces, Windows Management and so on. Select 'Contains' or 'Does Not Contain' option from the drop down menu. 'Does Not Contain' inverts your selected choice. |
Enter the object name as filter criteria in the text box. For example, if you choose 'Contains' then enter the phrase 'surfer.exe' in the text field, then you will only see logs with surfer.exe in the name column. |
|
Component |
Filter logs by the object modified by the action. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice |
Select the affected object. It is not possible to list all possible objects in this table. Please consult the list in the search interface. |
|
Filter Category |
Description |
Parameters |
|---|---|---|
|
Website |
Show only events that involved a specific website. Select 'Contains' or 'Does Not Contain' from the drop-down menu. |
For example, if you choose 'Contains' option from the drop-down and enter the phrase 'sc.com' in the text field, then all events that involve the website 'sc.com' in the 'Website' column are displayed. |
|
Action |
Filter
logs by
the type of secure shopping event activity. Select 'Equal' or 'Not Equal' from the drop down. 'Not Equal' inverts your choice. |
Possible activities:
For example, if you select 'Equal' from the drop-down and select 'Visit with Secure Browser' checkbox, only the session initiated events are displayed in the ‘Action’ column. |



