Step 7 - Investigate Events on Computers
The 'Computer Search' screen shows events recorded on all endpoints added to EDR. Details include event trends, network connection events, malware detection events and so on.
- Click 'Investigation' on the left then 'Computer Search' to open the interface
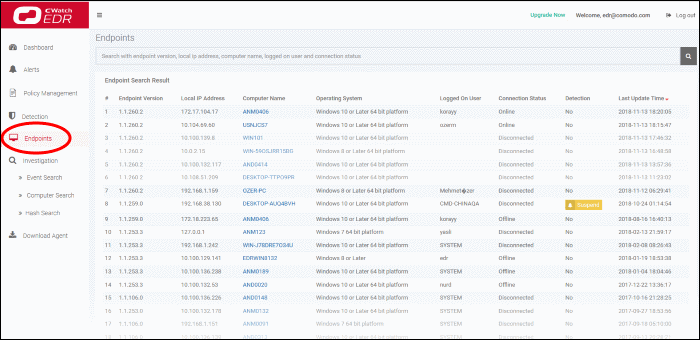
By default, the screen will be empty with the
search range set for the past 3 days.
- Click inside the search field above the data tiles, then:
- Select an endpoint from the list from the list to view data about the device.
- You can search for specific endpoints if required
- Use the time-range drop-down to show event info for specific dates (applies to Network Connections, Admin Privilege Usage, Malware Detections and Event Trend tiles).
- Click 'Apply'.
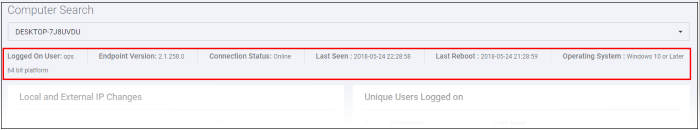
Information about the selected endpoint is shown directly below the search box:
The six tiles in the main section contain data about events on the endpoint:
- Local and External IP Changes- Changes to the endpoint's local IP and external IP.
- Event Trend - Number of events on the endpoint for the selected time-period. You can zoom the timeline by clicking and dragging on the graph. Place your mouse cursor on a point in the line to see events for a specific day.
- Unique Users Logged on - Most recent login times of every user that has logged onto the endpoint.
- Admin Privilege Usage - Events that required admin privileges.
- Network Connections - Network connection events for the selected time-period.
- Malware Detections - Threat detection events on the endpoint. Click a hash signature to view full details in the 'Hash Search' interface.
See 'Computer
Search' topic if you need more help with this.



