How to Use Comodo Forensic Analysis
- Comodo Forensic Analysis (CFA) lets you scan domains, workgroups and IP ranges to discover the trust level of every file on a network.
- The tool classifies files as 'safe' (whitelisted/ no threat), 'malicious' (blacklisted / malware) or 'unknown' (neither blacklisted nor whitelisted).
- Unknown files are automatically submitted to Comodo Valkyrie for static and dynamic tests. The results of the Valkyrie tests are reported back to the CFA software for administrator review.
Step 1 - Download, install and discover computers
- Please download the utility from: https://enterprise.comodo.com/freeforensicanalysis/
CFA does not require
installation and can be started by simply opening
'ForensicAnalysisTool.exe'. You need to agree to the terms and
conditions before using the application: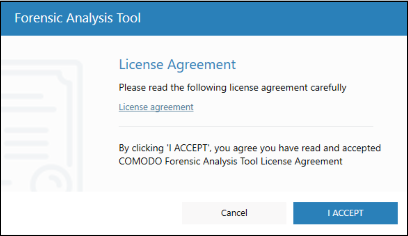
Step 2 - Specify
targets and run a scan
- On startup, Comodo Forensic Analysis runs a scan to discover all endpoints on the local network.
- Local discovery is designed for users who want to scan their immediate environment. At the end of discovery, you can select local endpoints then click 'Scan Now'.
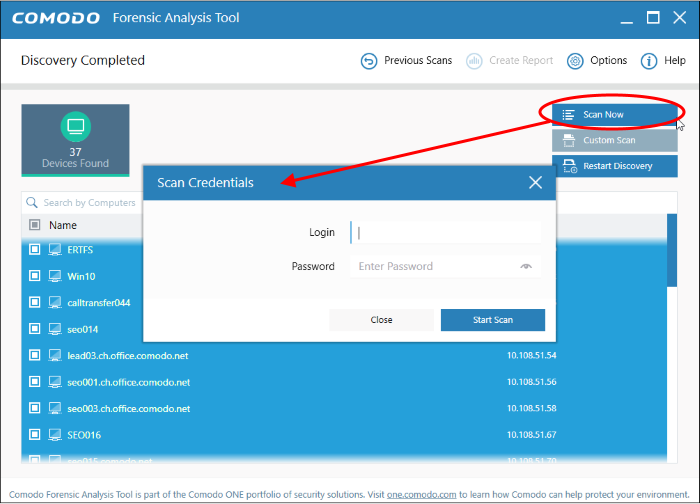
- Enter an admin username and password for the endpoints you wish to scan
- Choose a scan type:
- Quick Scan: Scans critical and commonly infected areas of target endpoints
- Full Scan: Scans all files and folders on target endpoints.
If you have additional endpoints that you wish to scan that were not found during discovery, then you can add these by creating a custom scan:
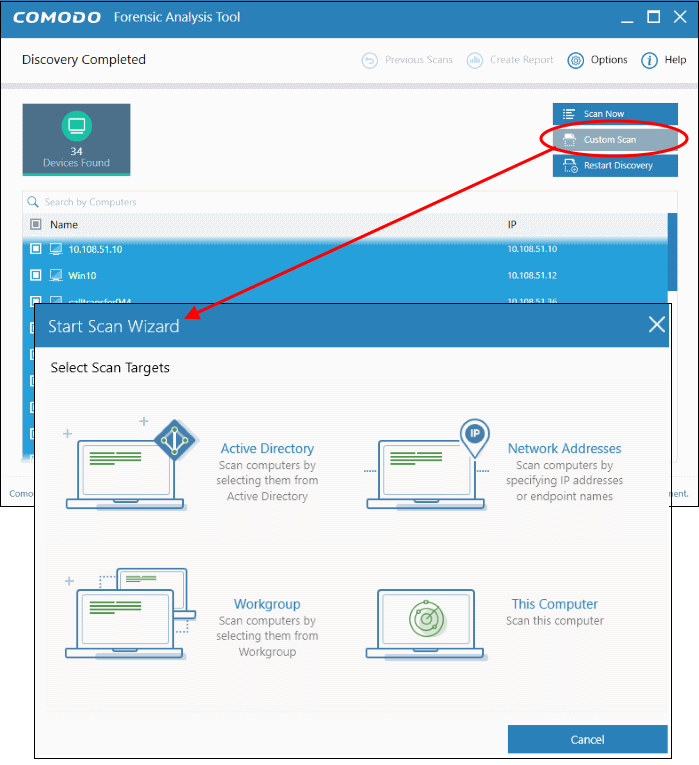
You can use any of the following methods to add endpoints to a custom scan:
- Active Directory - Scan computers which belong to an Active Directory domain
- Workgroup - Scan computers that belong to a local work group
- Network Address - Specify target endpoints by host name, IP address, or IP range
- This Computer- Run a scan on your local device
- Click 'Scan Now' to begin your scan.
Step 3 - View scan results and reports
Unknown files are automatically submitted to Valkyrie for analysis after the scan finishes. Click 'Detailed Scan Results' to view the results of the analysis:
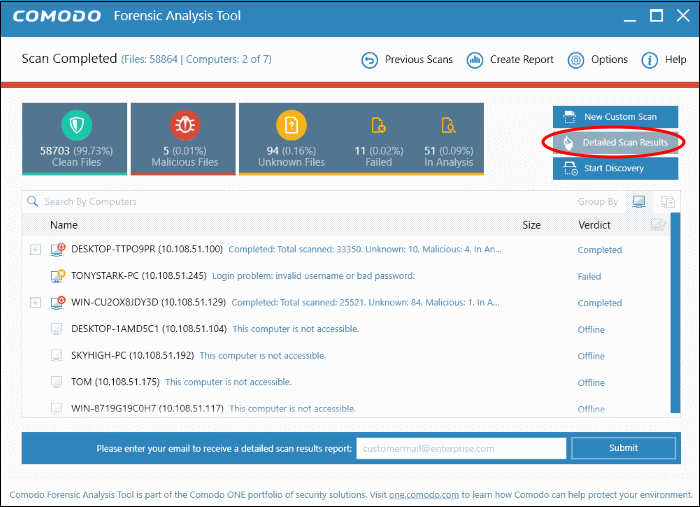
- Click 'Detailed Scan Results' to view all scan results analyzed by Valkyrie. Valkyrie is an automated, cloud-based behavior analysis system which subjects unknown files to a battery of static and dynamic tests to try and discover malicious or anomalous behavior.
- After the scan completes, you can enter your email id and click 'Submit' to get a detailed scan result report.
- You can view a more detailed version of these results by creating an account at the Valkyrie website. To do so, click 'Please click here to see the detailed results' and select 'Create an Account' at https://valkyrie.comodo.com/login
- You also can view detailed scan results in the 'Reports' tab:
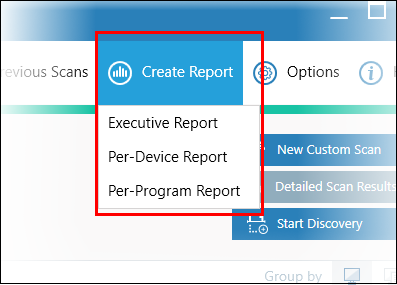
- Executive report - An overall report which shows the scope of the scan, the number of devices scanned, the number of unknown programs found and more.
- Per device report - Groups results by computer. Expand any row to see the unknown, safe and malicious files found on that specific machine.
- Per program report - Groups results by file to show the footprint of a specific file on your network. Expand any row to see the names and addresses of all devices on which the file was found.
For more details about reports, see https://help.comodo.com/topic-442-1-890-11317-Reports.html.



