Step 5 - Configure Firewall Policy
Firewall policies lets you manage traffic flowing through your network. Policies are constructed from a series of firewall rules which handle different types of traffic.
- Incoming traffic - Traffic from external network zones to hosts in internal networks.
- Outgoing traffic - Traffic from internal hosts to external networks
- Inter-zone traffic - Traffic between network zones connected to the firewall device.
- VPN traffic - Traffic from users connected to internal zones via virtual private network (VPN).
Each firewall rule contains three components:
- General Settings - Specify source and destination addresses and the service/protocol of packets to be intercepted by the rule. You can select firewall address objects/groups as 'source' and 'destination' addresses. See Create Firewall Address Objects for help to create firewall address objects.
- Web Protection - Enable or disable URL filtering, advanced threat protection (ATP) and SSL Interception.You can also choose pre-configured profiles. See Manage ATP Profile, Ceate URL Filter Profiles and Manage SSL Interception Profile for help to create these profiles.
-
Intrusion Prevention - Enable or disable Intrusion Prevention and Application Detection settings for the rule. See Manage Intrusion Prevention Profile for help to create this profile.
You can create different rules for different configurations for each of these components. The rules will be applied to the inbound and outbound packets in order.
- Before creating a firewall policy, you must first create firewall address objects, an advanced threat protection (ATP) profile, URL filters, and an intrusion prevention profile.
- Once done, these objects and profiles can be used in firewall, source network address translation (SNAT) and system access rules.
|
Tip: You can integrate the firewall with Active Directory to import users and user groups.
See the online help page https://help.comodo.com/topic-451-1-936-12832-Active-Directory-Integration.html for guidance on this. |
Create Firewall Address Objects
An address object is a reference to an IP, IP range or FQDN. Address objects can be used as source and destination addresses when creating firewall rules.
- Click 'Firewall' on the left and select 'Objects'
- Select the 'Firewall Addresses' tab
- Click the 'Add an address' link at the top
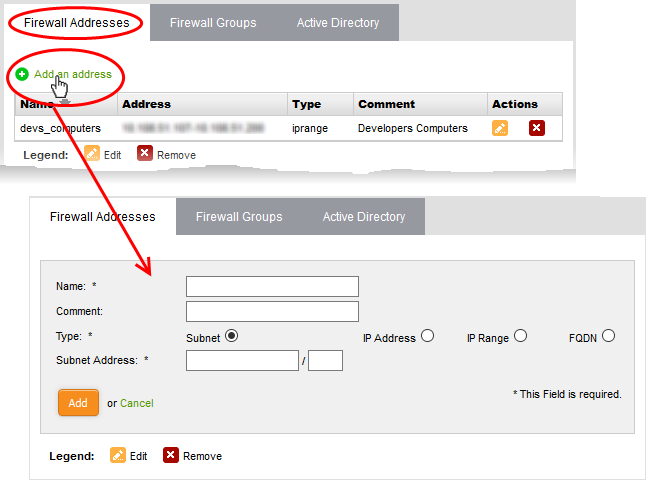
- Complete the parameters of the new object:
- Name - Specify a label for the object (15 characters max). Ideally this should help identify the host(s) included in the object.
- Comment - Enter a short description of the object.
- Type - The type of address object you wish to create. The options are:
- Subnet - The object will describe an entire sub-network of computers. Enter the subnet address in the 'Subnet Address' field.
- IP address - The object will refer to host at single IP address. Enter the IP address in the field provided.
- IP range - The object will refer to hosts at an entire range of IP addresses. Enter the IP range in the field provided.
- FQDN - The object will refer to a fully qualified domain name.
- Enter a domain name (without 'http://' or 'https://') in the FQDN Name field and click the 'Query' link.
- The firewall will perform a DNS query and add the resolved IP address in the box below
- To add more domains, enter the names one by one in the FQDN Name field and click the 'Query' link.
- Click 'Save'. The new address object will be added to the list.
- Repeat the process to add more address objects
Create Firewall Address Object Groups (Optional)
- A firewall object group is a collection of firewall address objects.
- An object group can be referenced as a source or destination in a firewall rule.
- Object groups make it easier to create rules for large networks by allowing you to reference a single item instead of multiple items.
Object groups can be edited at anytime to change their member objects. The change will affect all firewall rules which contain the object group.
- Click 'Firewall' on the left and select Objects'
- Select the 'Firewall Groups' tab
- Click 'Add a Group' at the top-left.
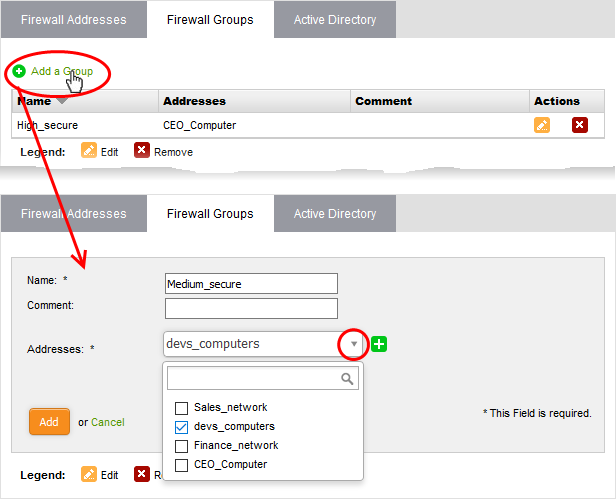
- Enter parameters for the new group as shown below:
- Name - Specify a label for the address group (15 characters max). Ideally this should help identify the address objects included in the group.
- Comment - Short description for the group.
- Addresses - Select the firewall address objects you want to include in the group.
- Start typing an object name to locate the object in the drop-down
- Use the check-boxes to select objects you wish to add to the group.
- Click 'Add'.
The group will be available for selection as a source or destination when creating a firewall rule.
- Repeat the process to add more address object groups
- The settings you save in the ATP profile will be applied to all rules in your policy that have 'Advanced Threat Protection' enabled.
- Advanced threat protection (ATP) safeguards networks against malware, hack attempts, data breaches and more.
- ATP intercepts files downloaded from websites or email attachments and uses a combination of antivirus scans, behavior analysis and blacklist checks to quickly block threats.
- Application containment protects your endpoints from unknown threats. Unknown threats are those that have not yet been identified as malware by the antivirus industry. If enabled, all files with an 'Unknown' trust rating will be run in an isolated sandbox on your endpoints. This prevents them from modifying other processes, stealing user data or otherwise infecting the local machine. Please note that containment for unknown applications is only applied to Windows endpoints.
ATP uses the following techniques to analyze the files:
- Comodo Antivirus – Always-on antivirus scanner which provides dependable protection against known malicious files.
- Comodo Valkyrie - A behavior analysis service which improves detection of zero-day threats by rigorously testing the run-time actions of unknown files.
To configure the ATP profile
- Click
'Services' on the left and select 'Advanced Threat Protection'.
- The interface lets you configure settings for application containment and antivirus.
- Select the 'Profiles' tab.
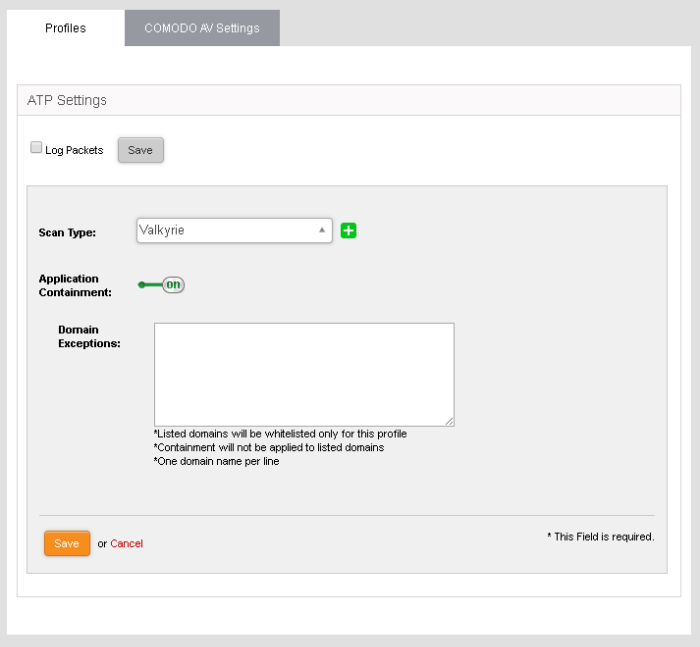
- Log Packets – The firewall will record events intercepted by the ATP module. You can view the logs in the 'Live Log Viewer' interface. See Step 6 - View Logs for more details.
- Scan Type - Select the threat verdict service you wish to use. Currently only 'Valkyrie' is available.
- Application Containment - Enable or disable automatic sandboxing of unknown files downloaded by users.
|
Note: Application containment is available only in the paid version of Dome Firewall. |
- Domain Exceptions - Domains you wish to exclude from application containment.
- Click 'Save'.
- Click the 'Comodo AV Settings' tab.
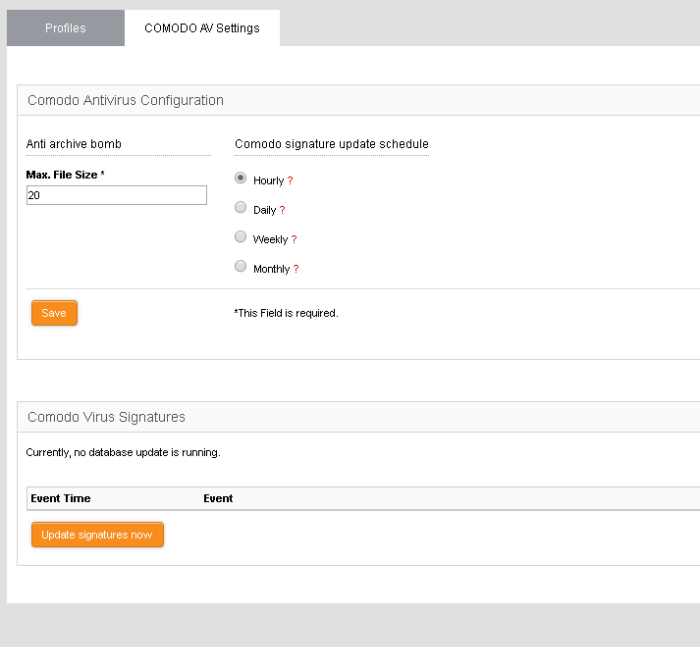
Comodo Antivirus Configuration
- Anti-archive bomb - Max File Size - (MB) Archive files larger than the size specified will not be scanned. Example archives are .zip and .rar files.
|
Note on archive bombs: One of the techniques used by attackers to disable an antivirus system is an 'Archive Bomb'. Similar to a Denial of Service (DoS) attack, an archive bomb is designed to overload the AV system by presenting it with more process requests than it can handle. Large files containing redundant data are compressed repeatedly and nested inside a very complicated archive structure inside the zip. When an antivirus application tries to extract those archives while scanning, it consumes an inordinate amount of system resources and often halts other operations. It is advised to configure the antivirus in a computer to skip scanning files larger than a set threshold. |
- Comodo Signature update schedule - Select how often the AV engine should check for and run signature updates. A more frequent schedule improves protection levels.
A URL filter profile lets you control which sites can be accessed by users on your network. There are two types of filters:
- Content categories - Filter pages according to the type of content on the site. For example, 'Chat', 'Entertainment', 'Sports' etc.
- URL Whitelist/Blacklist - Filter pages by blocking or allowing specific URLs. For example, you may want to blacklist 'www.facebook.com', but whitelist 'www.linkedin.com').
A profile can feature a combination of categories and white/blacklists. Profiles can be added to firewall rules created for an organization or device.
To create a URL filtere profile
- Click 'Proxy' on the left then choose 'HTTP/HTTPS'.
- Click the 'URL Filter' tab.
- Click the 'Add a New URL Filter Profile' link at the top.
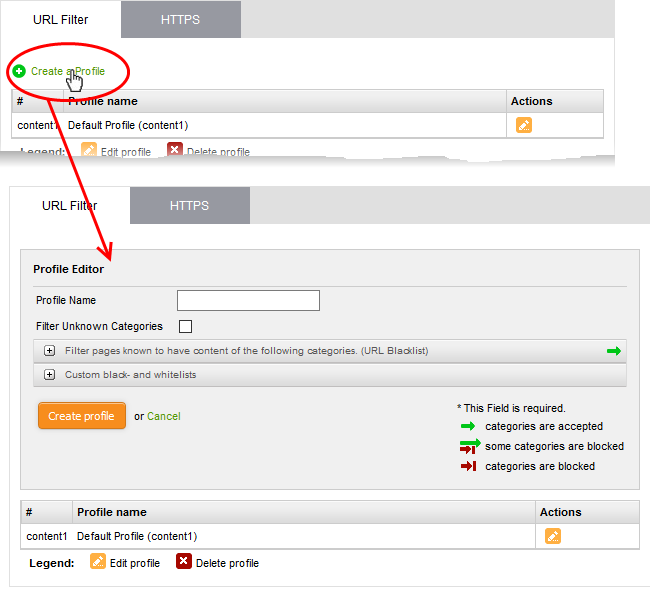
- Profile Name - Create a label for the profile. Ideally, the label should help identify the purpose or target of the profile.
- Filter Unknown Categories - Enable if you want the proxy to block all websites that do not fall into one of the provided categories. Click the link below this setting to view and configure categories:
- 'Filter pages known to have content of the following categories.' - Configure which categories of websites you want to block or allow:
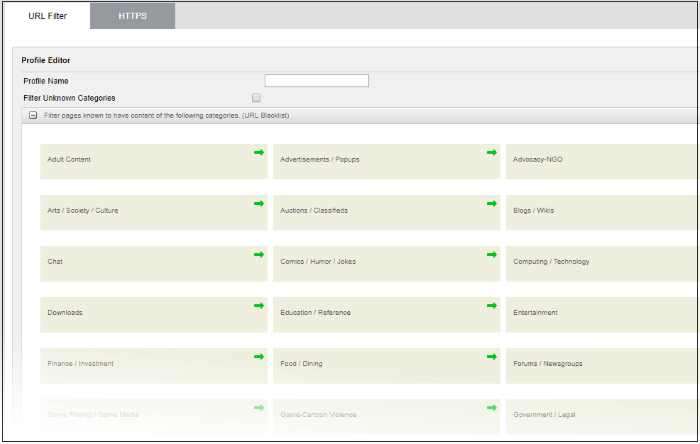
- Click the arrow in a tile to enable or disable a particular category:
|
- |
Access is allowed to websites is this category. |
|
|
- |
Access is blocked to websites is this category. |
- 'Custom black-and whitelists' – configure specific websites to which you want to allow or block access:
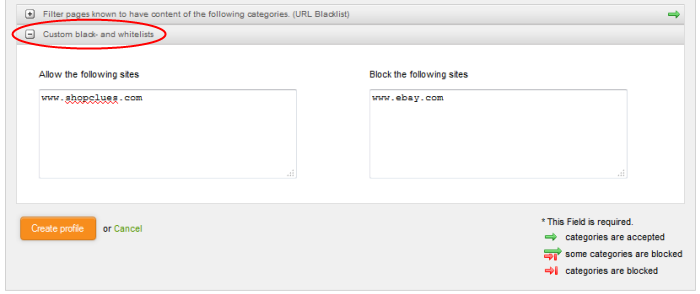
- Add URLs to the 'Allow...' or 'Block...' boxes as required.
|
Note:
|
- Click 'Create profile' to save the profile.
- You
can find the profile in the 'URL Filter' drop-down under 'Web
Protection' in the add/edit firewall rule interface.
- Repeat the process to add more URL filter profiles.
Manage SSL Interception Profile
-
Dome Firewall also offers a HTTPS Proxy service. The service receives requests for encrypted webpages, retrieves and caches the requested resources, applies any access control policies and forwards them to the requesting hosts.
-
You need to install the Dome intermediate certificate on endpoints in order to (i) analyze SSL encrypted traffic (ii) let the client authenticate itself to the proxy. See Certificate Settings for more details.
To configure the service
- Click 'Proxy' on the left then select 'HTTP/HTTPS'
- Select the 'HTTPS' tab.
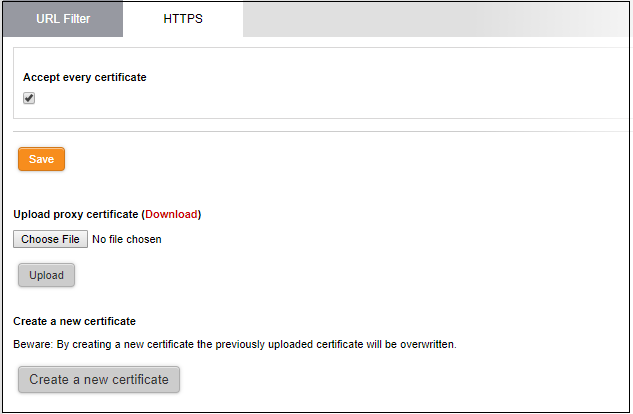
- Accept every certificate - If enabled, the firewall will not check the validity of certificates on remote server. This means the firewall will accept self-signed, expired and otherwise invalid certificates. If disabled, the firewall will only accept valid, fully trusted SSL certificates.
- Click 'Save'.
The intermediate certificate can be deployed to the HTTPS proxy service in two ways:
In either case, the same certificate needs to be imported into the browsers of the host computers in the network infrastructure that need access to the HTTPS proxy service.
If you already have an intermediate cert, you can upload it to the firewall appliance and install it on client computers.
|
Prerequisite: Ensure that the intermediate certificate is locally stored in the computer from which you are accessing the administrative console of the Dome Firewall virtual appliance. |
To upload an existing certificate
- Click the 'Browse' button under the 'Upload proxy certificate' option, navigate to the location where the certificate is stored and click 'Open'.
- Click 'Upload'
The certificate will be uploaded to
the virtual appliance and deployed.
The Dome Firewall is capable of creating a new self signed intermediate certificate with one year validity and use it for authentication. Once a new certificate is created, the existing certificate, if any, will be replaced by the new certificate. Hence the administrator should download the certificate and install it on to the host computers in the network infrastructure that need to authenticate them to the HTTPS proxy service.
To create a certificate
- Click the 'Create a new certificate' button. A confirmation dialog will be displayed.
- Click 'OK'
A new certificate will be created and deployed in the DFW virtual appliance.
- To download the certificate for transferring to the clients in the network, click the 'Download' link within the parenthesis beside 'Upload proxy certificate'. Transfer the certificate onto the computers in the network and install it on their Intermediate Certificate Store.
The settings you save
from this interface will be applied to all rules in your firewall
policy that have 'SSL Interception' enabled.
Manage Intrusion Prevention Profile
- Comodo Dome Firewall uses 'Snort', a state-of-the-art network intrusion prevention and detection system (IDS/IPS) directly built-in to its IP tables. Snort employs signature, protocol, and anomaly-based inspection of incoming traffic to detect and block intrusion attempts.
- Snort uses IPS 'rulesets'. Each ruleset contains a number of ips and application rules to identify applications that generate traffic on your network.
- Application identification rulesets intercept traffic from web based applications and allow or block data packets from them.
- All rule sets are constantly updated to confront emerging network intrusion techniques.
- The settings you save in the default profile will be applied to all rules in your firewall policy that have the 'default' intrusion prevention profile enabled.
Configure Rules Update Schedule
- Click 'Services' on the left then select 'Intrusion Prevention'
- Select the 'IPS Settings' tab
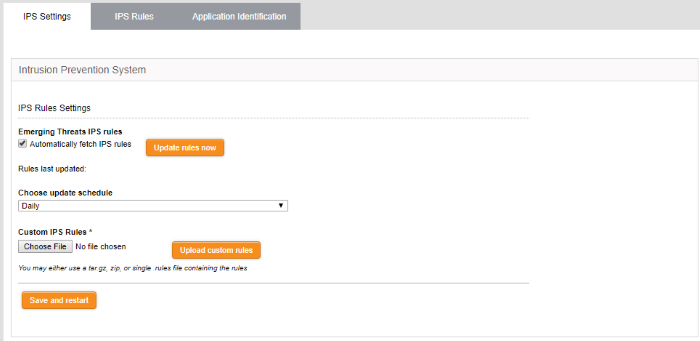
- Automatically fetch IPS rules - If enabled, Dome Firewall will download and install ruleset updates at the schedule you choose.
- Choose update schedule - Select the interval for automatic updates.
- Click 'Save and Restart'
Your settings will be
saved.
You can enable/disable IPS rulesets
and configure them to allow or block data packets as required.
To configure IPS Rulesets
- Click Services on the left then select 'Intrusion Prevention'
- Select the 'IPS Rules' tab
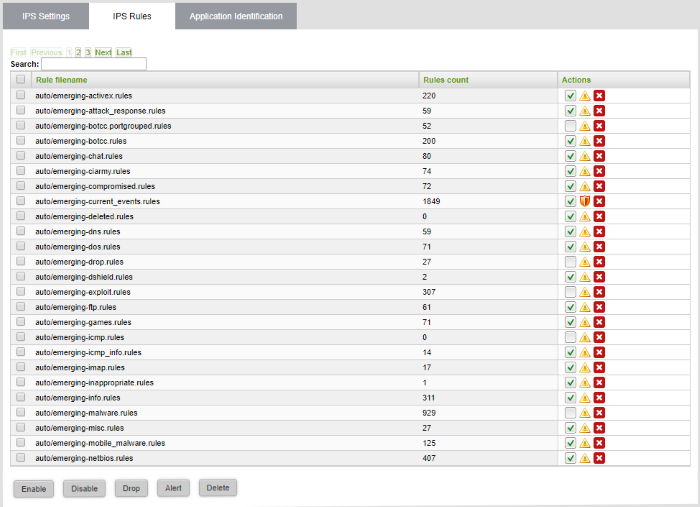
The 'IPS Rule List' interface lets you enable or disable rules individually or collectively
- To
disable a single active ruleset, click the
 icon beside the ruleset
in the 'Actions' column
icon beside the ruleset
in the 'Actions' column
- To
enable a single inactive ruleset, click the
 icon beside the ruleset
in the 'Actions' column
icon beside the ruleset
in the 'Actions' column
A ruleset can be applied in two ways:
-
Alert Policy - IPS generates an alert when a data packet matching a rule in the ruleset is encountered and passes the packet. The policy is indicated by an alert icon
 .
. -
Drop Policy - IPS blocks the data packet matching a rule in the ruleset without generating an alert. The policy is indicated by a shield icon
 .
.
Administrators can change the policy of a ruleset by clicking the shield/alert icon as appropriate.
- To change a ruleset policy from 'Alert' to 'Drop', click the 'Alert' icon in the row of the ruleset under the 'Actions' column
- To change a ruleset policy from 'Drop' to 'Alert', click the 'Shield' icon in the row of the ruleset under the 'Actions' column
Configure Application Identification Rulesets
- The intrusion prevention system uses application identification rulesets to intercept traffic from web based applications and allow or block data packets from them.
- You can enable/disable application identification rulesets and configure them to allow or block data packets as required.
To configure Application Identification Rulesets
- Click 'Services' on the left then select 'Intrusion Prevention'
- Select the 'Application Identification' tab
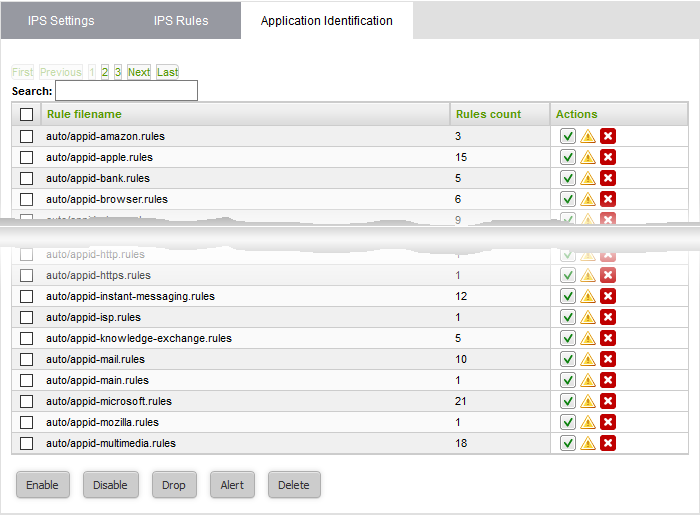
The 'AppId Rule List' interface lets you enable or disable rules individually or collectively
- To
disable a single active ruleset, click the
 icon beside the ruleset
in the 'Actions' column
icon beside the ruleset
in the 'Actions' column
- To
enable a single inactive ruleset, click the
 icon beside the ruleset
in the 'Actions' column
icon beside the ruleset
in the 'Actions' column
A ruleset can be applied in two ways:
- Alert
Policy - IPS generates an alert when a data packet from
applications is identified by a rule in the ruleset is encountered
and passes the packet. The policy is indicated by an alert icon
 .
.
- Drop
Policy - IPS blocks the data packet matching a rule in the
ruleset without generating an alert. The policy is indicated by a
shield icon
 .
.
The administrator can toggle the application policy for individual rulesets or for group of rulesets.
- To change a ruleset policy from 'Alert' to 'Drop', click the 'Alert' icon in the row of the ruleset under the 'Actions' column.
- To change a ruleset policy from 'Drop' to 'Alert', click the 'Shield' icon in the row of the ruleset under the 'Actions' column.
The firewall policy consists of a series of firewall rules that are imposed on different types of traffic.
- Click 'Firewall' on the left then choose 'Policy'
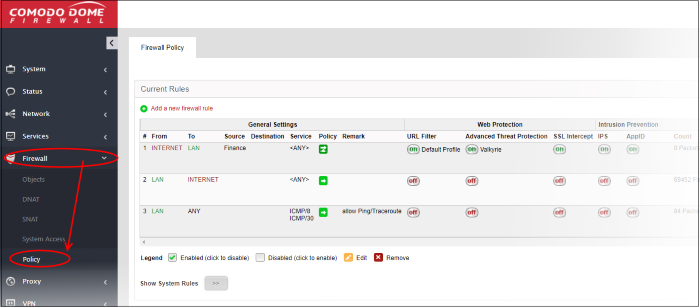
The interface contains two panes:
- Current Rules - The upper, 'Current Rules', pane lists all active rules and allows you to add and edit rules.
- Policy Firewall Settings - The lower ' Policy Firewall Settings' pane displays the current enabled/status of the policy firewall. You can change the status and configure the policy firewall log.
To add a new firewall rule
- Click the 'Add a new firewall rule' link at the top left. The 'Policy Firewall Rule Editor' will open.
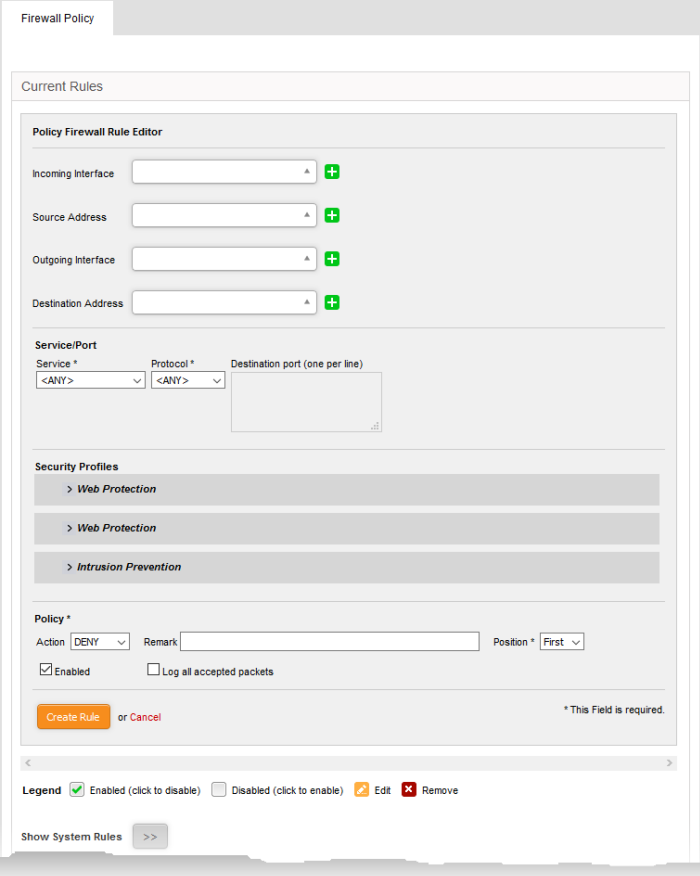
General Settings:
- Incoming Interface - Choose the interface through which traffic is received. The drop-down shows the common and custom interfaces connected to the firewall.
- You can select more than one interface for the rule
- Use the 'Search' box to search for a specific interface
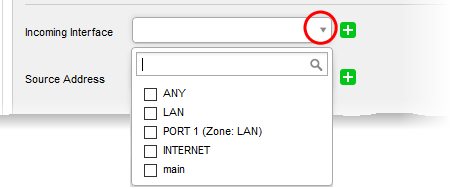
- Source Address - Choose the firewall address object or group that covers the IP address(es), subnet. Or domain from which traffic originates.
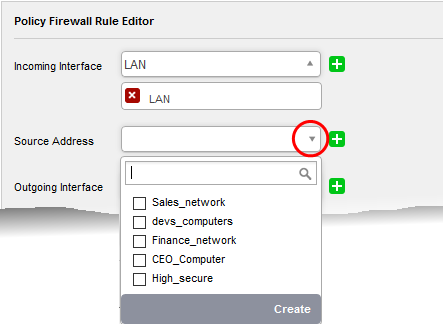
|
Tip: If a firewall object covering the IP address/IP Address range or the subnet to be specified has not been created under the Firewall Objects interface previously, you an create a new object from this drop-down.
The pane for creating a new object will appear.
The process is similar to creating a new address object from the 'Firewall' > 'Objects' > 'Firewall Address' interface. See the explanation under 'Create Firewall Address Objects' for guidance. |
- Outgoing Interface - Choose the interface through which the traffic is sent.
- Destination Address - Choose the firewall address object or group to which traffic is sent.
- Service - Choose the type of service hosted by the source from the drop-down.
- Protocol - Choose the protocol used by the service.
- Destination port - Specify the destination port number(s) used by the service, one by one.
|
Tip:
The virtual appliance is loaded with predefined combinations of
service/protocol/port, like HTTP/TCP/80, |
- Click 'Web Protection' to open the security features for web protection:
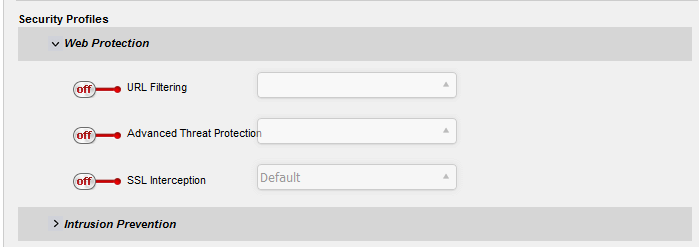
- URL Filtering - Enable or disable URL filtering profiles on traffic intercepted by the rule.
- Move the switch to ON to enable URL filtering
Select the profile which specifies the sites you wish to block or allow from the drop-down:
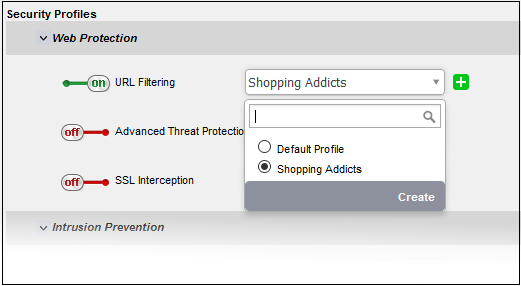
- URL filtering profiles can be created for organizations/device in the 'URL Filter' interface (click 'URL filter' on the left). See Create URL Filter Profiles for more details.
- Advanced Threat Protection - Enable or disable advanced threat protection (ATP) settings on traffic intercepted by the rule. You can choose the ATP profile you want to apply from the drop-down menu.
- Move the switch to ON to enable ATP.
- Select the ATP profile from the drop-down.
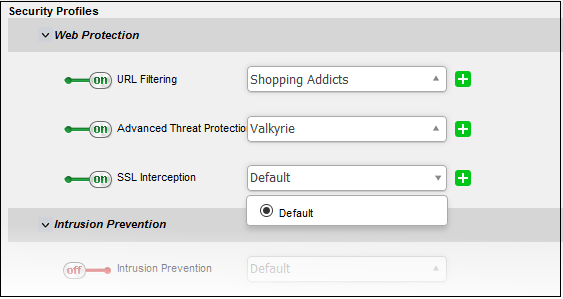
- The default ATP profile can be managed from the 'Advanced Threat Protection' interface. See Manage ATP Profile for guidance on this.
- SSL Interception - Enable or disable analysis of encrypted traffic which is intercepted by the rule.
- Move the switch to ON to enable SSL interception.
- Select the default profile from the drop-down.
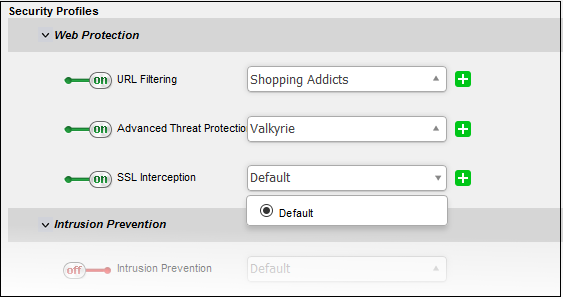
- The default 'SSL Interception' profile can be managed from the 'Proxy' > 'HTTP/HTTPS' > 'HTTPS' interface. See Manage SSL Interception Profile for guidance on this.
Intrusion Prevention Settings:
- Click 'Intrusion Prevention' to configure these settings:
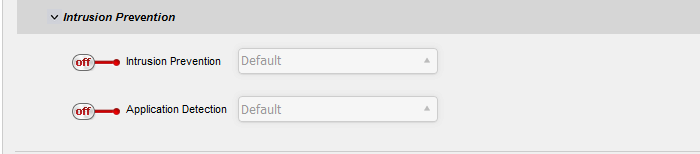
- Intrusion Prevention - Enable/disable Snort intrusion detection technology on traffic intercepted by the rule.
- Move the switch to ON to enable intrusion prevention.
- Select the default profile from the drop-down.
Selecting 'Default' will apply the rule settings configured in the 'Intrusion Prevention' default profile. See 'Manage Intrusion Prevention Profile' for more details.
- Application Detection - Enable or disable application identification rules on traffic intercepted by the rule. Application ID rules allow you to track the activities of applications on your network, allowing you to attribute IPS events to applications.
- Move the switch to ON to enable application detection.
- Select the default profile from the drop-down.
Selecting 'Default' will apply the settings configured in the 'Intrusion Prevention' default profile. See 'Configure Application Identification Rulesets' for more details.
Policy Settings
- Action - Specify whether packets matching the rule should be allowed or denied. The available options are:
- Accept - The data packets are permitted without filtering
- Drop - The packets will be denied.
- Reject - The packets will be refused and a error packet sent in response
- Remark - Enter a short description of the rule. This description appears in the 'Remark' column of the rules table.
- Position - Set the priority of the rule. Higher position rules take precedence in the event of a conflict over settings. The rules in iptables are processed in the order they appear on the list.
- Enabled - Enable or disable the firewall rule.
- Log all accepted packets - Enable to create a record of all packets allowed by the rule. You can view the logs from the respective firewall admin console. See Step 6 - View Logs for more details.
- Click 'Create Rule'.
- The new firewall rule will be added and applied.
- Repeat the process to add more rules.