Step 5 – Configure VPN Policy
VPN firewall rules allow you to set traffic limits for users and hosts who are connected through SSL VPN and IPsec tunnels. The added firewall objects, explained in step 3, will be available for selection while creating a VPN rule.
To create a new firewall rule
- Open the 'VPN Policy' interface by clicking 'Firewall' > 'Policy' from the left hand side navigation and selecting the 'VPN Policy' tab.
- Click the 'Add a new VPN firewall rule' link at the top left. The 'VPN firewall rule editor' will open.
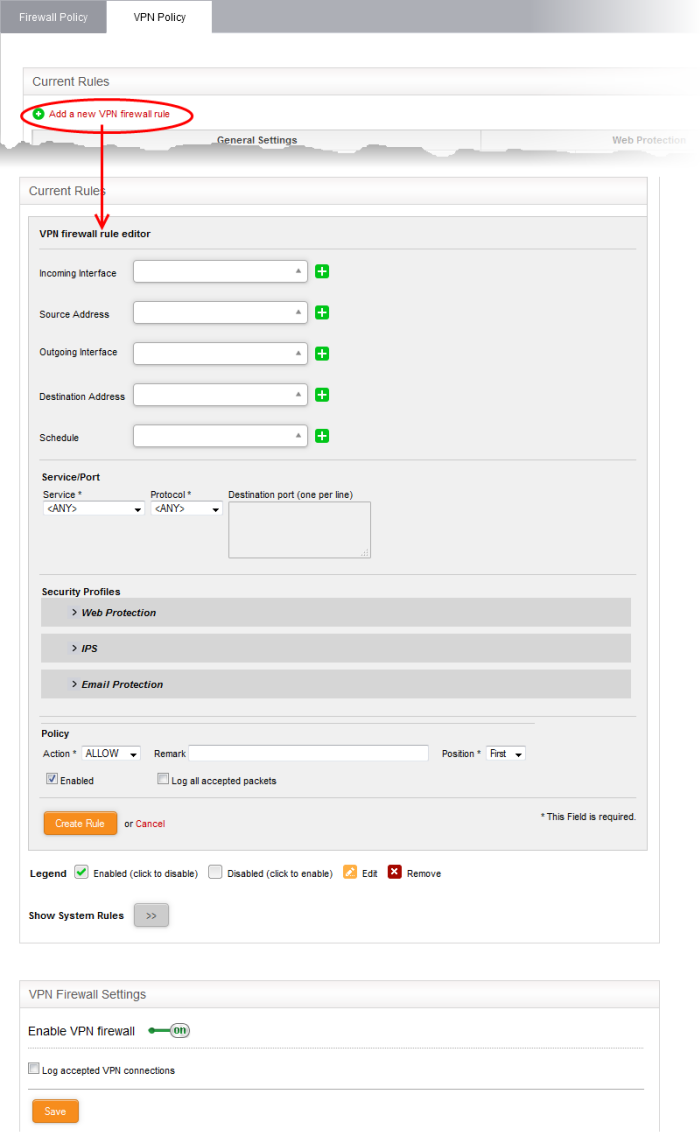
The 'VPN Firewall Rule Editor' interface is divided into three areas for specifying the different components of the rule:
|
- |
Choose the source and destination of the traffic and set a schedule for the rule to be active |
|
|
- |
Specify the service pertaining to the traffic to be intercepted by the rule |
|
|
- |
Configure to allow or block the traffic intercepted by the rule |
- Incoming Interface - Choose the interface device, VPN tunnel or the physical port at which the traffic is received, from the drop-down.
- Source Address - Choose the firewall object or the object group that covers the IP address, IP address range, the subnet or the VPN user(s), at which the traffic to be intercepted by the rule, is received.
If a firewall object covering the IP address/IP Address range or the subnet to be specified has not been created under the Firewall Objects interface previously, you can create a new object from this interface too by clicking 'Create' from the drop-down.
- Outgoing Interface - Choose the interface device or the physical port to which the traffic is directed, from the drop-down.
- Destination Address - Choose the Firewall Object or Object Group containing the IP address, IP Address Range or the subnet of the host(s) to which the traffic is directed, from the drop-down.
If a firewall object covering the IP address/IP Address range or the subnet to be specified has not been created under the Firewall Objects interface previously, you an create a new object from this interface too by clicking 'Create' from the drop-down.
- Schedule - The Schedule Objects added to the Firewall Objects > Schedule interface will be available in the drop-down. Choose the schedule object(s) that cover the time period(s) for which the rule needs to be active from the drop-down.
If the schedule object covering the required time period P to be specified has not been created under the Firewall Objects > Schedule previously, you can create a new object from this interface too by clicking 'Create' from the drop-down.
Service/Port - Select the type or the service hosted by the source, the protocol and the port used by the service.
- Service - Choose the type of service from the drop-down
- Protocol - Choose the protocol used by the service
- Destination port - Specify the destination port(s) of the service one by one, in the 'Destination Port' text box.
|
Tip:
The appliance is loaded with predefined combinations of
service/protocol/port, like HTTP/TCP/80, |
- Action - Specify whether the packets matching the rule should be allowed or denied from the Policy drop-down. The options available are:
- Allow - The data packets will be allowed without filtering
- Deny - The packets will be dropped
- Reject - The packets will be rejected, and error packets will be sent in response
- Remark - Enter a short description for the rule. The description will appear in the Remark column of the Rules table.
- Position - Set the priority for the rule in the list of rules in the respective rules interface. The rules in the iptables are processed in the order they appear on the list.
- Enabled - Leave this checkbox selected if you want the rule to be activated upon creation.
- Log all accepted packets - Select this checkbox if you want
the packets allowed by the rule are to be logged.
- Click 'Create Rule'. A confirmation dialog will appear.
Configuring
the VPN Firewall Settings
The lower 'VPN Firewall Settings' pane allows the administrator to enable/disable the VPN firewall rule and to opt for logging the packets that pass the rule.
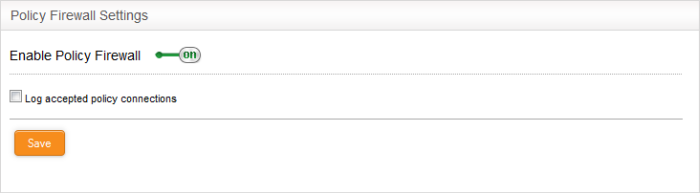
- Use the 'Enable VPN firewall' toggle switch to switch the state of the VPN firewall
- Select the 'Log accepted VPN connections'
checkbox to log the packets that has passed the VPN Policy
- Click 'Save' for your settings to take effect
See 'Manage
VPN Firewall Rules ' for more details.



