Comodo Internet Security - Understanding Alerts
After first installing Comodo Internet Security, it is likely to see a number of pop-up alerts. This is perfectly normal and indicates that the security suite is learning the behavior of your applications and establishing which programs need privileges such as Internet access and file access rights. Each alert provides information and options that enable you to make an informed decision on whether you want to allow or block a request or activity. Alerts also to allow you to instruct Comodo Internet Security on how it should behave in future when it encounters activities of the same type.
Buffer Overflow Protection Feature - Buffer overflow attack occurs when a malicious program or script deliberately sends more data to its memory buffer than the buffer can handle. Defense+ provides alerts on attempt of most types of buffer overflow attacks and provides protection against data theft, computer crashes and system damage. For more details, please refer Defense+ Settings > Execution Control Settings > Detect Shell Code Injections.
Alerts Overview
Comodo Internet Security alerts come in four main varieties, namely:
-
Defense+ Alerts (including Elevated Privilege Alerts)
Broadly speaking, Antivirus alerts inform you when a virus or malware is executed into your system, Firewall alerts inform you about network connection attempts and Defense+ alerts tell you about the behavior of application on your system. In all the three cases, the alert can contain very important security warnings or may simply occur because you are running an application for the first time. Your reaction should depend on the information that is presented at the alert.
An example alert is shown below.
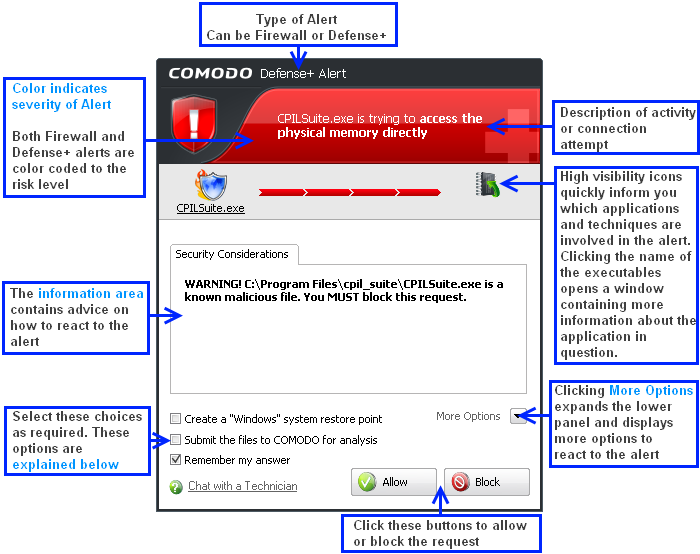
Severity Level
The upper strip of both Defense+ and Firewall alerts are color coded according to risk level. This provides a fast, at-a-glance, indicator of the severity of the alert. However, it cannot be stressed enough that you should still read the 'Security Considerations' section in order to reach an informed decision on allowing or blocking the activity.
|
Note: Antivirus alerts are not ranked in this way. They always appear with a red upper strip. |
-
Yellow Alerts - Low Severity - In most cases, you can safely approve these connection request or activity. The 'Remember my answer for this application' option is automatically pre-selected for safe requests.
-
Orange Alerts - Medium Severity - Carefully read the ‘Security Considerations section before making a decision. These alerts could be the result of a harmless process or activity by a trusted program or an indication of an attack by malware. If you know the application to be safe, then it is usually okay to allow the request. If you do not recognize the application performing the activity or connection request then you should block it.
-
Red Alerts - High Severity - These alerts indicate highly suspicious behavior that is consistent with the activity of a Trojan horse, virus or other malware program. Carefully read the information provided when deciding whether to allow it to proceed.
Security Considerations: The Security Considerations area contains a description of the nature of the alert. It tells you the name of the software/executable that caused the alert; the action that it is attempting to perform and how that action could potentially affect your system. You can also find helpful advice about how you should respond.
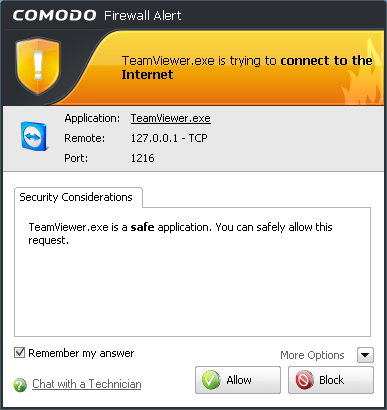
-
Remember my answer - Select this option if you want Firewall to implement the same decision for identical requests in future - meaning you are not prompted if same type of activity or connection attempt arises in future. The response you made this time is applied automatically to the all the similar activities or connection attempts.
More Options
Clicking the More Options in the Firewall alert expands the lower panel and displays more options for reacting to the alert.
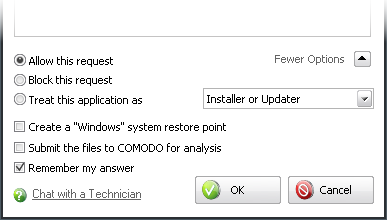
The first three options enable you to select your reaction to the activity or connection attempt requested.
-
Allow this request - Allows the requested activity or connection attempt.
-
Block this request - Denies the requested activity or connection attempt.
-
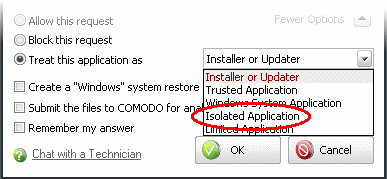
Treat this application as - Enables you to select a predefined security policy to be deployed on to the application in question. Select this option and select a predefined policy depending on the trustworthiness and type of the application.
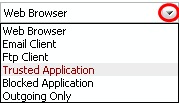
Refer to Predefined Firewall Policies and Predefined Computer Security Policies for more details.
-
Submit the files to COMODO for analysis - Select this option if you suspect that that the application that has raised this alert as a malware. Comodo Internet Security sends the application to Comodo automatically, irrespective of your Allow or Block response. Comodo analyzes the application and includes it in the safe list or black list accordingly.
-
Create a "Windows" system restore point - Selecting this option instructs your Windows Operating System to create a restore point. This enables you to safely rollback your system to the previous system state if you encounter problems because of allowing or blocking this request.
If you have Comodo Time Machine (CTM) installed then CIS creates a Time Machine restore point.
If you do not have Comodo Time Machine installed, then CIS creates a regular Windows System Restore point.
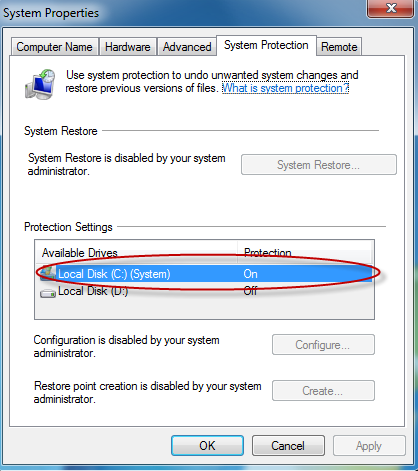
Note: This option is only available if Windows System Restore is enabled in your system. You can check whether system restore is enabled by visiting the Windows control panel:
To ensure that Windows system restore is enabled
-
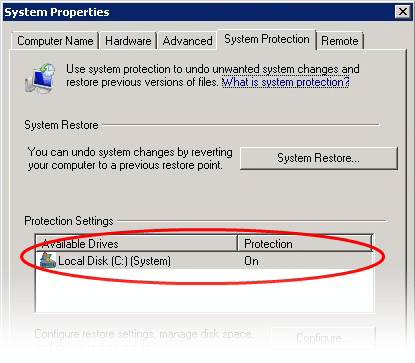
Click Start > Control Panel > System > System Protection
-
Make sure that the Protection status of the hard disk drive partition(s) is set to 'On' under 'Protection Settings'.
To ensure that Windows system restore is enabled
-
Click Start > Control Panel > System > System Protection
-
Make sure that the checkbox(es) beside the hard disk drive partition(s) under 'Automatic restore points > Create restore points automatically on the selected disks' are selected.
To ensure that Windows system restore is enabled
-
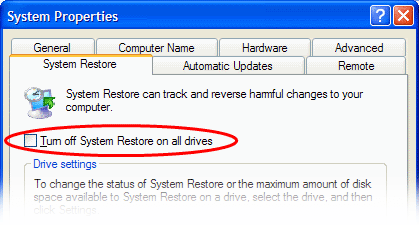
Click Start > Control Panel > System > System Restore tab
-
Make sure that the checkbox 'Turn off System Restore on all drives' is NOT selected.
If Comodo Time Machine (CTM) is installed in your system, the restore point is created by it irrespective of whether the Windows Restore Point is enabled in your system or not.
|
Background Note: Comodo Time Machine is a powerful system rollback utility that allows you to quickly restore your computer to an earlier point in time. The software is free of charge and allows you to quickly recover your computer to its last working state in the event of malware attacks or system crashes. Find out more and download the application from http://www.comodo.com/home/data-storage-encryption/data-recovery.php. |
Now that we've outlined the basic construction of an alert, lets look at how you should react to them:
Comodo Internet Security generates an Antivirus alert whenever a virus or malware tries to be copied or executed without your knowledge and displays the alert at the bottom right hand side of your computer screen. These alerts are a valuable source of real-time information that helps the user to immediately identify which particular files are infected or are causing problems and the choices for actions to be taken.
The alert contains the name of the virus detected and the location of the file or application infected by it.
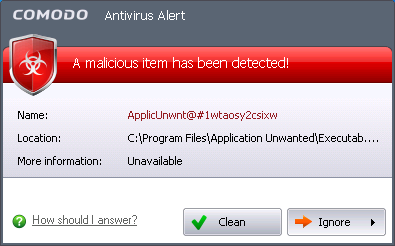
You can take one of the following steps to answer the Antivirus alert.
-
Disinfect the file if there exists a disinfection routine for the detected file or move the file or application to Quarantined Items for later analysis.
-
Ignore the alert only if you trust the application or the source of application by clicking 'Ignore'.
To disinfect the file or application
-
Click the 'Clean' button.
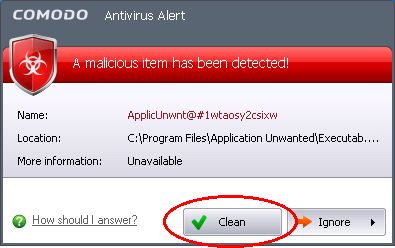
Comodo Internet Security will disinfect and clean the file or application. If the threat detected is new one and the disinfection routine does not exist, then CIS will move the file/application to Quarantined Items for later analysis. You can submit the file/application to Comodo for analysis from the Quarantine. Refer to Quarantined Items for more details.
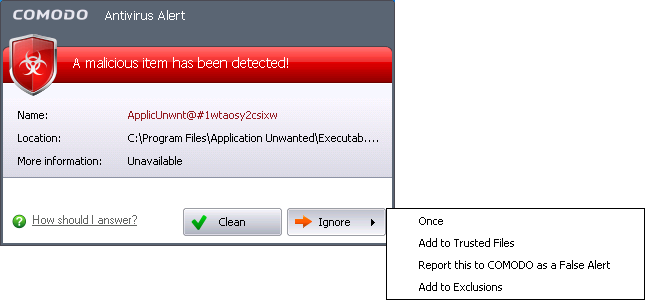
To ignore the alert if you trust the file/application
-
Click 'Ignore'. Selecting Ignore provides you with four options.
-
Once. If you click 'Once', the virus is ignored only at that time only. If the same application invokes again, an Antivirus alert is displayed.
-
Add to Trusted Files. If you click 'Add to Trusted Files', the virus is moved to Trusted Files area. The alert is not generated if the same application invokes again.
-
Report this to COMODO as a False Alert. If you are sure that the file is safe, select 'Report this to COMODO as a False Alert'. The Antivirus sends the file to Comodo for analysis. If the file is trustworthy, it is added to the Comodo safelist.
-
Add to Exclusions. If you click 'Add to Exclusions', the virus is moved to Exclusions list. The alert is not generated if the same application invokes again.
Comodo Internet Security generates a Firewall alert on network connection attempts. The followings steps will help you answer a Firewall alert: :
-
Carefully read the 'Security Considerations' section. The Firewall can recognize thousands of safe applications. (For example, Internet Explorer and Outlook are safe applications). If the application is known to be safe - it is written directly in the security considerations section along with advice that it is safe to proceed. Similarly, if the application is unknown and cannot be recognized you are informed of this.
If it is one of your everyday applications that you want to grant Internet access to then you should select Allow This Request (it may be the case that the application has not yet been added to the safe application database yet).
If you don't recognize the application then we recommend you select Block This Request, but do not select the Remember My Answer option.
In all cases, clicking on the name of the application opens a properties window that can help you determine whether or not to proceed:
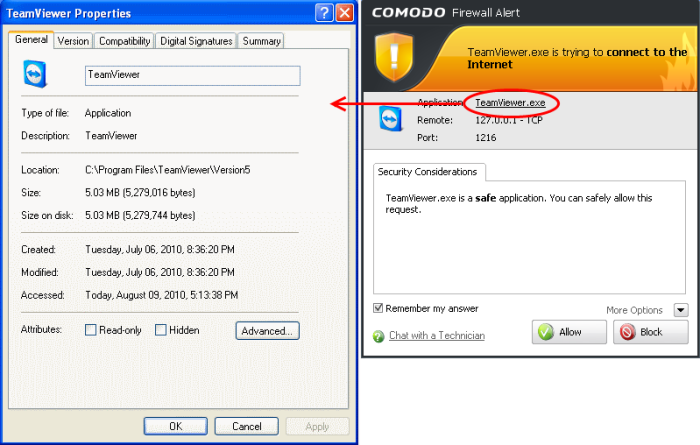
-
If you are sure that it is one of your everyday application, try to use the Treat This Application As option as much as possible. This deploys a predefined firewall policy on the target application. For example, you may choose to apply the policy Web Browser to the known and trusted applications 'Internet Explorer', 'FireFox' and 'Opera'. Each predefined policy has been specifically designed by Comodo to optimize the security level of a certain type of application.
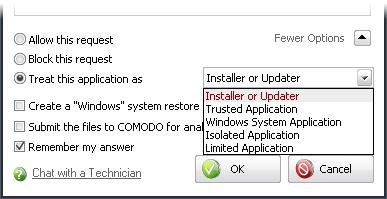
If you do not see the Treat this Application As option, you should click More Options. Remember to check the box Remember My Answer.
-
If the Firewall alert reports a behavior, consistent with that of a malware in the security considerations section, then you should block the request AND click Remember My Answer to make the setting permanent.
Comodo Internet Security generates a Defense+ Alert based on behavior of applications running in your system. Following are the steps to be followed to answer a Defense+ alert:
-
As with Firewall Alerts, carefully read the 'Security Considerations' section. Comodo Internet Security can recognize thousands of safe applications. If the application is known to be safe - it is written directly in the security considerations section along with advice that it is safe to proceed. Similarly, if the application is unknown and cannot be recognized you are informed of this.
If it is one of your everyday applications that you want to grant execution rights to then you should select Allow This Request.
If you don't recognize the application then we recommend you select Block This Request but do not select Remember My Answer check box.
-
Avoid using the Installer or Updater policy if you are not installing an application. This is because treating an application as an 'Installer or Updater' grants maximum possible privileges onto to an application - something that is not required by most 'already installed' applications. If you select 'Installer or Updater', you may consider using it temporarily with Remember My Answer left unchecked.
-
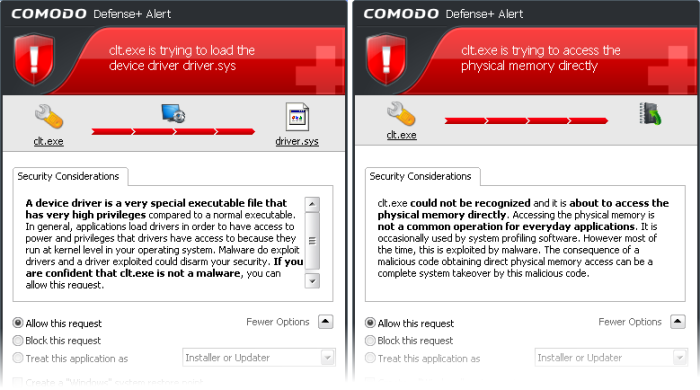
Pay special attention to Device Driver Installation and Physical Memory Access alerts. Again, not many legitimate applications would cause such an alert and this is usually a good indicator of malware/rootkit like behavior. Unless you know for a fact that the application performing the activity is legitimate, then Comodo recommends blocking these requests.
-
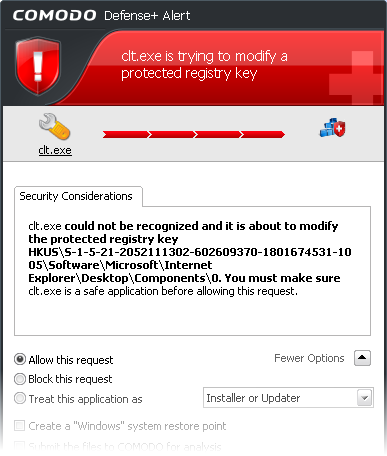
Protected Registry Key Alerts usually occur when you install a new application. If you haven't been installing a new program and do not recognize the application requesting the access , then a 'Protected Registry Key Alert' should be a cause for concern.
-
Run with elevated Privileges. CIS will display this kind of alert when the installer of an unknown application requires administrator, or elevated, privileges to run. An installer that is allowed to run with elevated privileges is permitted to make changes to important areas of your computer such as the registry.
If you have good reason to trust the publisher of the software then you can click the 'Allow' button. This will grant the elevated privilege request and allow the installer to run.
If you are unsure of the safety of the software, then Comodo recommends that you run it in the sandbox by clicking the 'Sandbox' button.
If this alert is unexpected then you should abort the installation by clicking the 'Block' button (for example, you have not proactively started to install an application and the executable does not belong to an updater program that you recognize).
If you select 'Always trust the publisher of this file' then CIS will treat all files from this installer as safe and no future alerts will be generated when you run executables by this publisher.
In all cases, please remember to select 'Submit this file to Comodo for analysis' so that our researchers can establish whether the application is safe or not. If it is found to be safe, we shall add it to the global safelist (whitelist). If it is found to be malicious we will add it to our global list of malware signatures (blacklist). Comodo will then distribute the updated lists to all users of CIS.
You will see this type of alert if:
-
The sandbox is enabled
and
-
'Automatically detect and run installers outside the sandbox' is enabled. These settings can be modified in Defense+ Tasks > Defense+ Settings > Sandbox Settings.
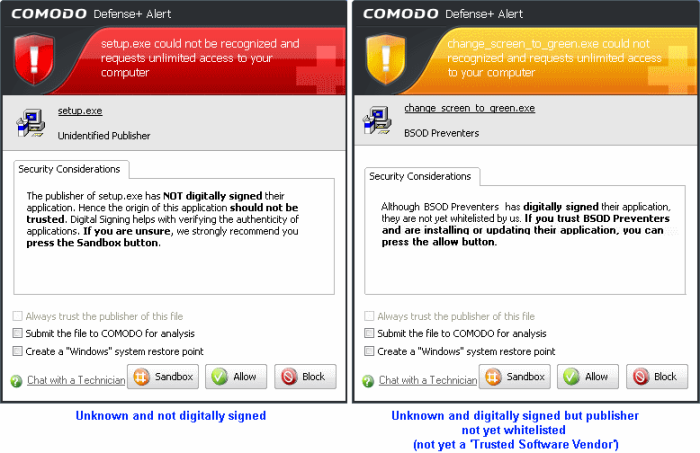
There are two versions of this alert - one for unknown installers that are not digitally signed and the second for unknown installers that are digitally signed but the publisher of the software has not yet been white-listed (they are not yet a 'Trusted Software Vendor').
-
Unknown and unsigned installers should be either sandboxed or blocked.
-
Unknown but signed installers can be allowed to run if you trust the publisher, or may be sandboxed if you would like to evaluate the behavior of the application.
-
In both instances, select 'Submit the file to Comodo for analysis' so that we can effectively categorize the file and add it to to our global white-list or blacklist.
Also see:
-
'Answering a Sandbox Alert' to see how CIS handles unknown applications that are not detected as being an installer or updater program.
-
'Unknown Files: The Sand-boxing Processes' - to understand the decision making process behind why CIS chooses to sandbox certain applications.
-
'Trusted Software Vendors' - for an explanation of digitally signed files and 'Trusted Software Vendors'.
-
Protected File Alerts usually occur when you try to download or copy files or when you update an already installed application.
Were you installing new software or trying to download an application from the Internet? If you are downloading a file from the 'net, try to use Allow without Remembering option to cut down on the creation of unnecessary rules within the firewall.
If an application is trying to create an executable file in the Windows directory (or any of its sub-directories) then pay special attention. The Windows directory is a favorite target of malware applications. If you are not installing any new applications or updating Windows then make sure you recognize the application in question. If you don't, then select Block This Request without selecting Remember My Answer option.
If an application is trying to create a new file with a random filename e.g., "hughbasd.dll" then it is probably a virus and you should block it permanently by selecting Treat As Isolated Application (fourth down in the graphic below).
-
A Buffer overflow Alert is generated when an application tries to send more data to its memory buffer than that the buffer can handle. This may be a possible hacking attempt.
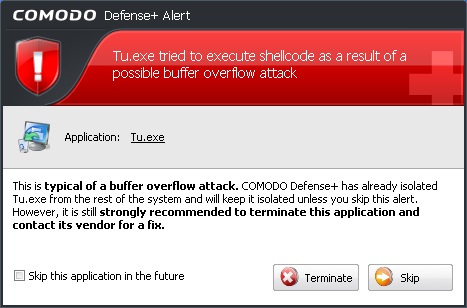
If you click Terminate, the application is denied access to execute.
If you click Skip, the application is excluded from monitoring for the moment and is allowed access. But on the next attempt of attack the alert is generated again.
If you select 'Skip this application in the future', and click Skip, the application is excluded from monitoring permanently and allowed access all the times. Do this only of the application is from a trusted vendor.
-
If a Defense+ alert reports a malware behavior in the security considerations area then you should Block the request permanently by selecting Remember My Answer option. As this is probably a virus, you should also submit the application in question, to Comodo for analysis.
-
Unrecognized applications are not always bad. Your best loved applications may very well be safe but not yet included in the Comodo certified application database. If the security considerations section says “If xxx is one of your everyday applications, you can allow this request”, you may allow the request permanently if you are sure it is not a virus. You may report it to Comodo for further analysis and inclusion in the certified application database.
-
If Defense+ is in Clean PC Mode, you probably are seeing the alerts for any new applications introduced to the system - but not for the ones you have already installed. You may review the 'Unrecognized Files' section for your newly installed applications and remove them from the list for them to be considered as clean.
-
Avoid using Trusted Application or Windows System Application policies for you email clients, web browsers, IM or P2P applications. These applications do not need such powerful access rights.
By default, CIS will display an alert whenever it runs an unknown application in the sandbox:
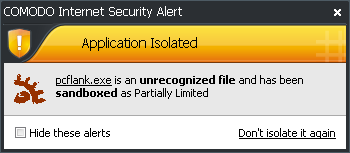
The alert will show the name of the executable that has been isolated in the sandbox. The application will be automatically added to Unrecognized Files list.
-
Clicking the name of the application will open the Unrecognized Files interface, that displays a list of the unrecognized files including the currently sandboxed application.
-
Clicking Don't isolate it again removes the application from the Unrecognized Files list and adds it to the Trusted Files list, enabling the application to run outside the sandbox. Choose this option if you are absolutely sure that the executable is safe.
Users are also reminded that they should submit such unknown applications to Comodo via the 'Unrecognized Files' interface. This will allow Comodo to analyze the executable and, if it is found to be safe, to add it to the global safe list. This will ensure that unknown but ultimately safe applications are quickly white-listed for all users.
Also see:
-
'Run with elevated Privileges' alerts.
-
'Unknown Files: The Sand-boxing and Scanning Processes' - to understand the decision making process behind why CIS chooses to sandbox certain applications.
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved