Protected Files and Folders
Protected Files and Folders setting allows you to protect specific files and folders against unauthorized modification especially by malicious programs such as virus, Trojans and spyware. It is also useful for safeguarding very valuable files (spreadsheets, databases, documents) by denying anyone and any program the ability to modify the file - avoiding the possibility of accidental or deliberate sabotage. If a file is 'Protected' it can still be accessed and read by users, but not altered. A good example of a file that ought to be protected is the your 'hosts' file. (c: windows system32 drivers etc hosts). Placing this in the 'Protected Files and Folders' area would allow web browsers to access and read from the file as per normal. However, should any process attempt to modify it then Comodo Internet Security blocks this attempt and produce a 'Protected File Access' pop-up alert.
To access Protected Files, navigate to: Defense+ Tasks > Computer Security Policy > Protected Files and Folders.
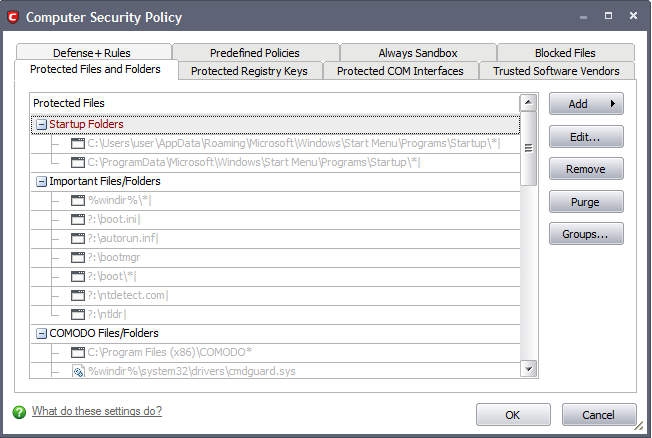
To manually add an individual file, file group or process
-
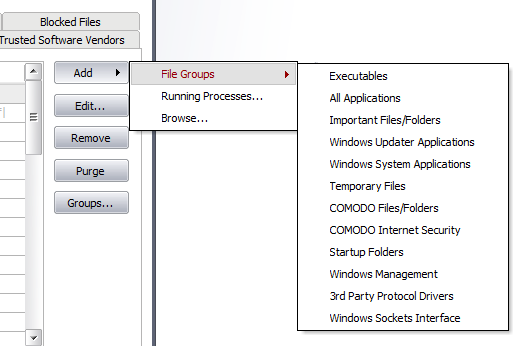
Click the 'Add' button. Click here for a description of the choices available when selecting a file.
Exceptions
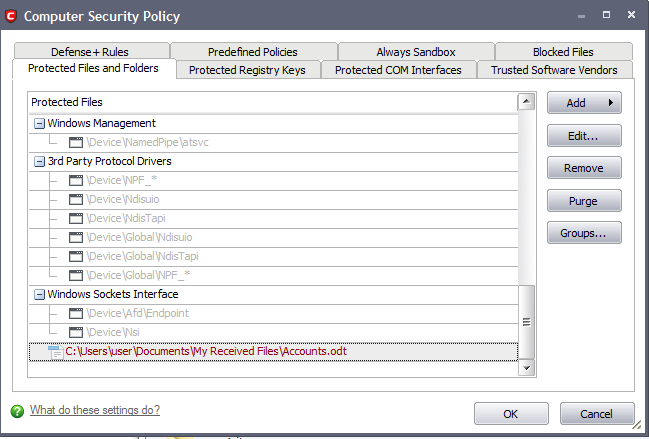
Users can choose to selectively allow another application (or file group) to modify a protected file by affording the appropriate Access Right in 'Computer Security Policy'. A simplistic example would be the imaginary file 'Accounts.ods'. You would want the Open Office Calc program to be able to modify this file as you are working on it, but you would not want it to be accessed by a potential malicious program. You would first add the spreadsheet to the 'Protected Files and Folders' area by clicking the 'Add' button then 'Browse...' to 'Accounts.ods'. Once added to 'Protected Files', you would go into 'Computer Security Policy' and create an exception for 'scalc' so that it alone could modify 'Accounts.ods'.
- First Add Acconts.odt to Protected Files and Folders
2. Then go to Defense+Rules tab and add it to the list of applications and click 'Edit'.
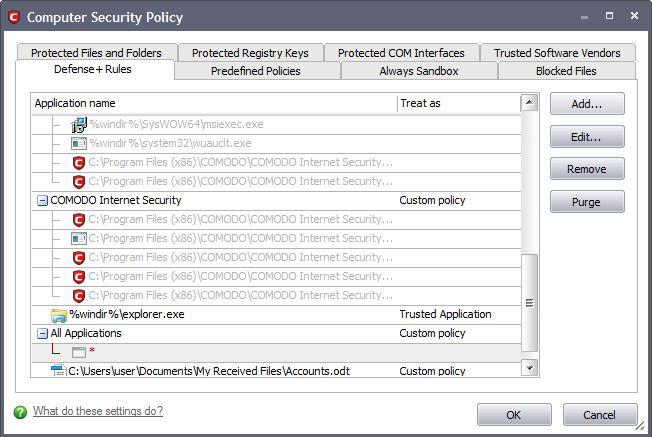
3. Click the 'Customize' link.
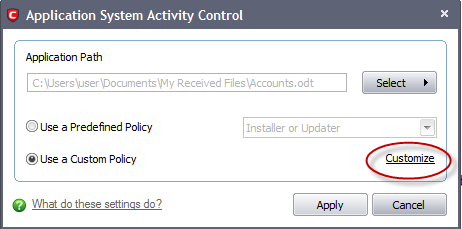
4. Under the 'Access Right' tab, click the link Modify beside the entry Protected Files/Folders.
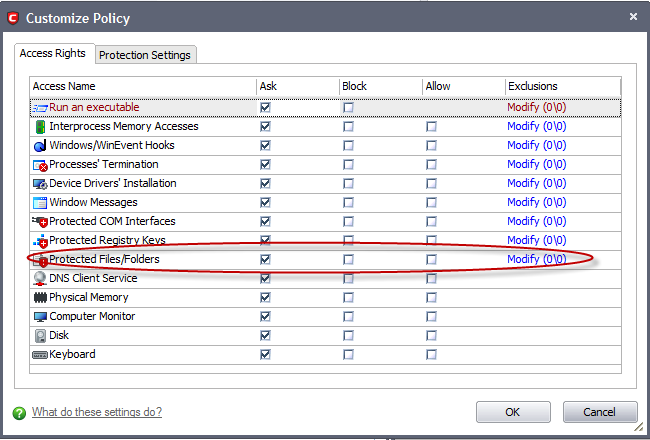
5. Under the 'Allowed Files/Folders' tab click 'Add' then 'Browse...'. Add Accounts.odt and exceptions to the 'Ask' or 'Block' rule in the 'Access Rights'.

Another example of where protected files should be given selective access is the Windows system directory at 'c:windowssystem32'. Files in this folder should be off-limits to modification by anything except certain, Trusted, applications like Windows Updater Applications. In this case, you would add the directory c:windowssystem32* to the 'Protected Files and Folders' area (* = all files in this directory). Next go to 'Computer Security Policy', locate the file group 'Windows Updater Applications' in the list and follow the same process outlined above to create an exception for that group of executables.
The 'Groups...' button allows the user to access the 'File Groups' interface.
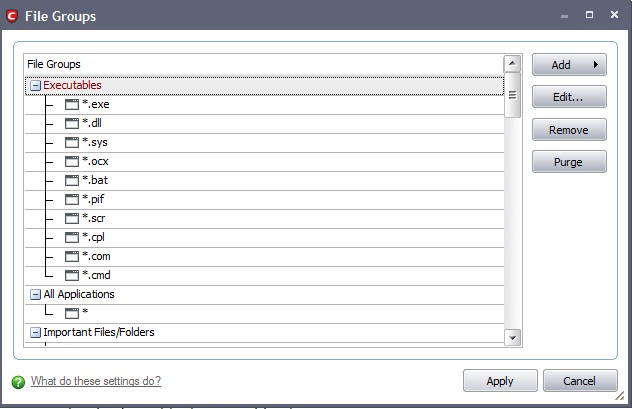
File groups are handy, predefined groupings of one or more file types. Creating a file group allows you to quickly deploy a Defense+ Rule across multiple file types and applications.
This interface allows you to
-
Create a new File Group by clicking the 'Add' button.
-
Edit the names of an Existing File Group or File by right-clicking and selecting the 'Edit' button.
-
Add a file to an existing file group by selecting the File Group name from the list then clicking Add > Select From >....'
-
Re-assign files to another file group by dragging and dropping.
|
Note: This area is for the creation and modification of file groups only. You cannot modify the security policy of any applications or files from here. To do that, you should use the Defense+ Rules interface or the Predefined Policies Interface. |
Comodo Internet Security User Guide | © 2012 Comodo Security Solutions Inc. | All rights reserved



