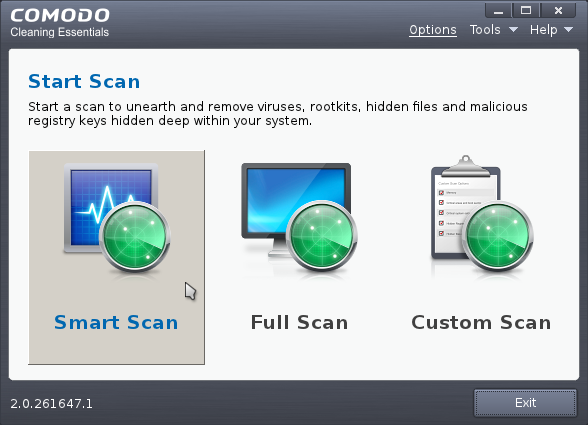
Smart Scan
Smart Scan in Comodo Cleaning Essentials allows you to run a quick scan on the critical areas in your system which are highly prone to infection from viruses, rootkits and other malware. Smart scan feature scans and cleans the system memory, autorun entries, hidden services, boot sectors and other critical areas like crucial registry keys in Windows registry, system files and system configuration. These areas are responsible for the stability of your computer and keeping them clean and sanitized is essential to keep you healthy and running.
Scanning the critical areas of your system can be executed instantly. Hidden services are executed by malicious attempts like a spyware through key logger, rootkits, buffer overflow or Denial of Service (DoS) attacks. These attacks will be running silently in the computer and enable hackers to steal your identity and confidential information like your credit card details.
On completion of scanning, you can:
- Clean the detected threats or move them to Quarantine and later remove them;
- Exclude an application you consider as safe from the threat list;
- Report the threat as a False Positive to Comodo.
1. Click the 'Smart Scan' from the CCE main interface.
The application will check whether any updates are available for the virus database before commencing the scan. If available, it will first update the local virus database.
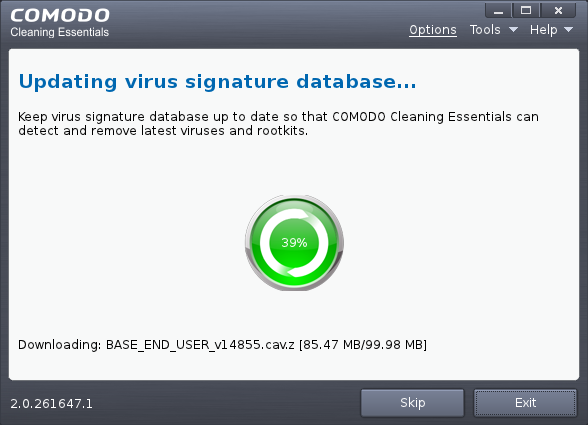
It is advised that you always let the application to update the database as scanning with your virus database up-to-date detects even the zero-hour threats. However, if you do not want the database update at this moment, you can skip this step by clicking 'Skip'.
The application will start scanning the critical areas of your system and the progress will be displayed.
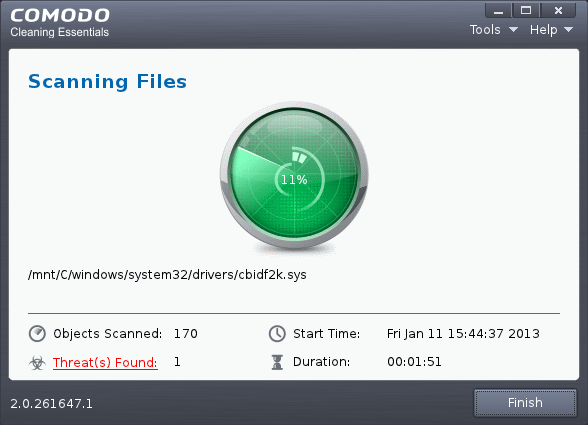
During the course of scanning, if you want to see details on the threats detected so far, click Threats Found link. A results window with the threats identified thus far will be displayed.
On completion of scanning, The 'Scan Finished' dialog will be displayed.
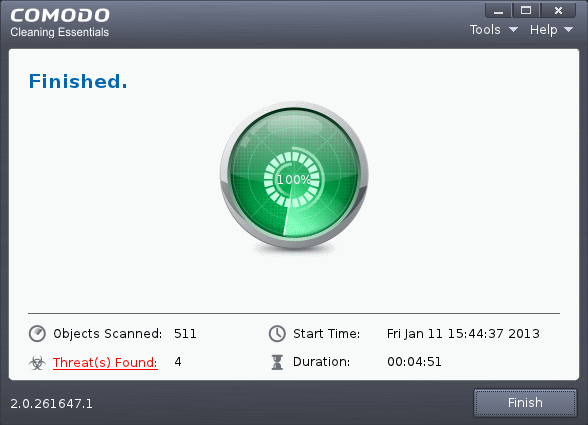
2. Click 'Next' to view the results.

- If malicious executables or abnormal system settings are discovered on your system, the 'Results' window displays the list of those items (Viruses, Malware and so on).
|
Note: You can sort the scan results by alphabetical order by clicking the 'Threat Name' column header. Similarly you can sort the scan results based on the risk level by clicking the 'Risk' column header. |
The 'Results' window allows you to quarantine and later remove, ignore the threat if it is a safe file or to submit it as a false positive to Comodo if you are sure about the authenticity of the file. The default operation is 'Clean', that means Comodo Cleaning Essential will clean the threat if a disinfection routine is available for it, else, will move it to quarantine. For abnormal system settings, you have the option to either repair the setting or ignore.
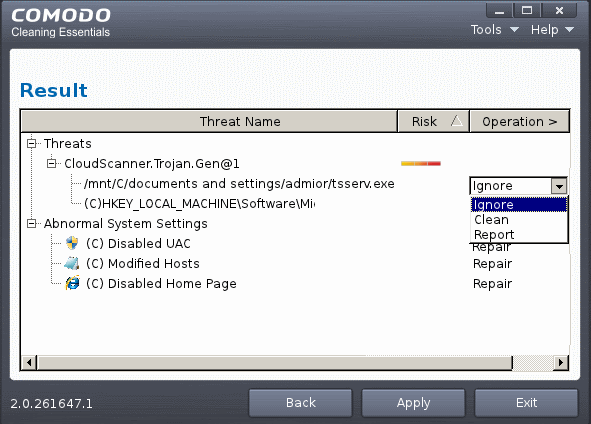
- To clean a threat, click on the entry under the Operations column and select 'Clean'. The file will be disinfected or moved to quarantine upon applying the operation. You can later remove the file from your system from the 'Quarantined Items' interface. Refer to Managing Quarantined Items for more details.
- To ignore a threat if you consider the file is safe, click on the entry under the Operations column and select 'Ignore'.
- To report threat as a false-positive result, click on the entry under the Operations column and select 'Report'. The file will be sent to Comodo. Experts in Comodo will analyze the file and add it to whitelist, if found safe.
- To repair or ignore an abnormal system settings, click on the entry under the Operations column and select the required action.
- To apply a common operation to all the entries in the list, click on the Operations column header and select the required action.
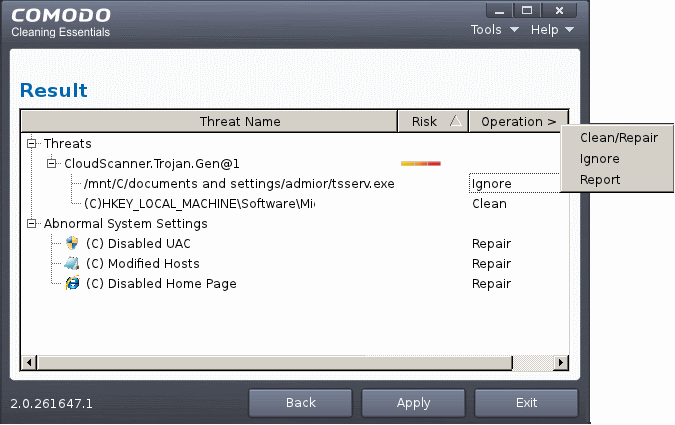
3. Click 'Apply' to apply the selected operations to the threats. The selected operations will be applied and the results will be displayed.
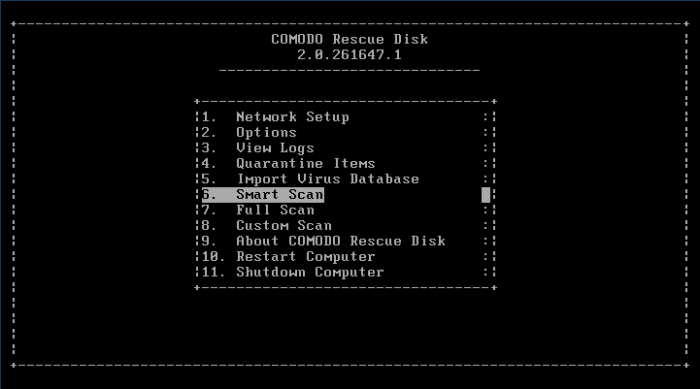
If you have opted to use the text mode, scroll to 'Smart Scan' by using the down or up arrow and click the 'Enter' button.
The application will check whether any updates are available for the virus database before commencing the scan. If available, it will first update the local virus database.
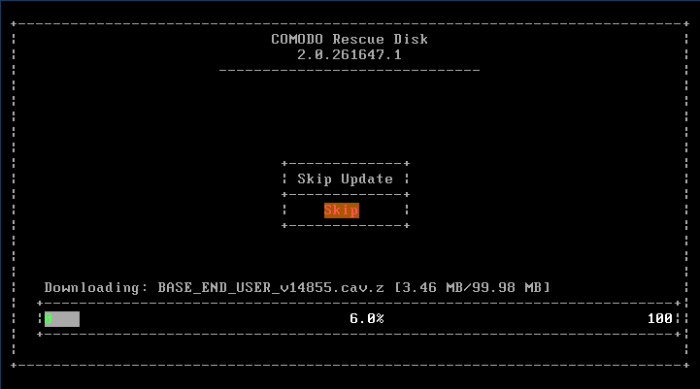
It is advised that you always let the application to update the database as scanning with your virus database up-to-date detects even the zero-hour threats. However, if you do not want the database update at this moment, you can skip this step by clicking 'Enter' button.
The application will start scanning the critical areas of your system and the progress will be displayed.
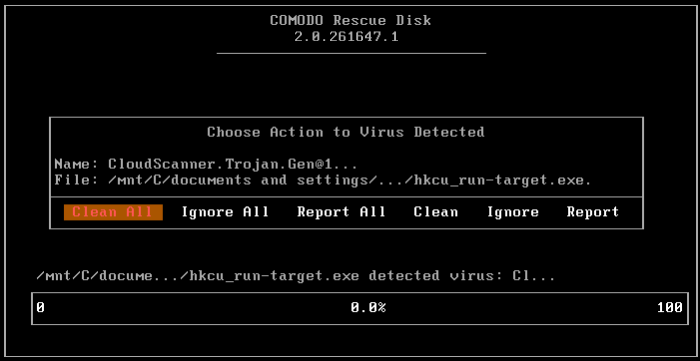
For each and every malware detected by CCE, a 'Choose Action to Virus Detected' screen will be displayed.
The 'Results' screen allows you to quarantine and later remove, ignore the threat if it is a safe file or to submit it as a false positive to Comodo if you are sure about the authenticity of the file. The default operation is 'Clean All', that means CCE will clean the threat if a disinfection routine is available for it, else, will move it to quarantine. For abnormal system settings, you have the option to either repair the setting or ignore.
- To clean a threat, select 'Clean' using the left or right arrows and press the 'Enter' key. The file will be disinfected or moved to quarantine upon applying the operation. You can later remove the file from your system from the 'Quarantined Items' interface. Refer to Managing Quarantined Items for more details.
- To ignore a threat if you consider the file is safe, select 'Ignore' using the left or right arrows and press the 'Enter' button.
- To report threat as a false-positive result, select 'Report' using the left or right arrows and press the 'Enter' key. The file will be sent to Comodo. Experts in Comodo will analyze the file and add it to whitelist, if found safe.



