Step 8 - Analyze Files by their Hash Values
- A hash search lets you locate files by their MD5 or SHA-1 hash value. Visibility, execution trend, file history and execution summary are listed for each file.
- Unlike the 'Event' and 'Computer' interfaces, you cannot simply search for a hash. You must either
- (i) Copy and paste a hash value from the dashboard, detection or event search interfaces, or
- (ii) Click a hash-value link in the dashboard or 'Computer Search' screens. This will auto-populate the search interface.
- Click 'Investigation' on the left then 'Hash Search' to open the interface
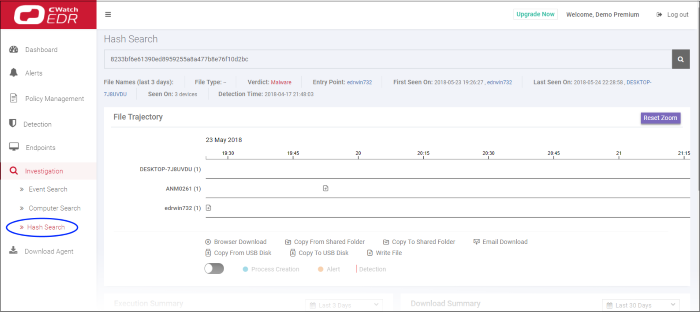
- By default, the screen will be blank
- Enter the hash value of the file you wish to analyze. Hash values of malware and safe files can be copied from various interfaces such as:
- 'Dashboard' > 'Malware & Suspicious Activity' tile > under 'Most Found Malware' and 'Last Found Malware'
- 'Detection' > in the 'Sha1' column
- 'Investigation' > 'Event Search' > in the 'Process Hash' column
- Click a hash value on any of the screens above to automatically populate the search box here.
- Use the time-range drop-down to show event information for a specific date range (applies to 'Execution Summary', 'Download Summary', 'Creation Summary' and 'Execution Trend' tiles)
Results are shown below the search box:
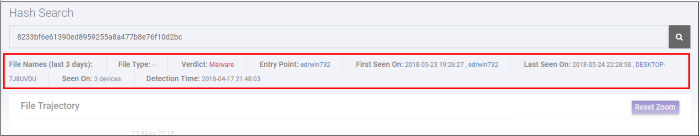
The results screen shows the following details about the file:
- File Trajectory - The movement of the file - where it was downloaded from, where it was copied to, and so on.
- Execution Summary - Devices on which the file was executed. Details include the file path and the number of times it was executed.
- Download Summary - Which endpoints the file was downloaded to ('Entry Point'), the URL it was downloaded from, and the number of times it was downloaded.
- Creation Summary - Endpoints on which the file created processes, and the file location.
- Execution Trend – The number of times the file was executed during the selected period. Zoom into specific hours by dragging any point on the graph.
See 'Hash Search' if you need more help with this.



