Step 4 - View Events Details on Endpoints
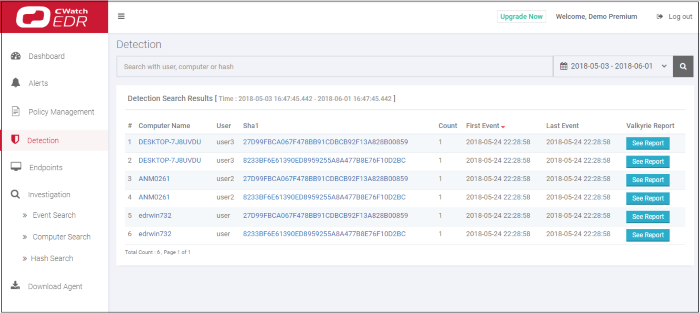
The 'Detection' screen shows detailed information about malicious events on your endpoints.
- Click
'Detection' on the left to open the 'Detection' interface
|
Detection Search Results - Table of Column Descriptions |
|
|---|---|
|
Column Header |
Description |
|
Computer Name |
The name of the endpoint. Click the computer name to view its full details. See 'Computer Search' for details. |
|
User |
The user who is logged in to the endpoint. |
|
Sha 1 |
Hash value of the detected malware. Click the hash value to view its full details. See 'Hash Search' for details. |
|
Count |
Number of times the malicious event was detected on the endpoint. |
|
First Event |
Date and time the event was first detected on the endpoint. |
|
Last Event |
Date and time the event was most recently detected on the endpoint. |
|
Valkyrie Report |
Unknown and suspicious files are analyzed by Comodo's Valkyrie, an advanced file analysis and file verdict system. Click 'See Report' to view the file analysis. See https://help.comodo.com/topic-397-1-773-9563-Introduction-to-Comodo-Valkyrie.html for more information about Valkyrie. |
- The 'Search' box above the table lets you filter the list:
- Type full or partial search terms in the search box and press enter.
- Matching results will be automatically displayed.
- Clear the search terms and click 'Search' again to reset the list.
- Click any column header to sort items in ascending/descending/alphabetical order.
- Use the time-range drop-down to show event information for a specific date or date range.
See 'Viewing Event Details on Endpoints' topic if you need more help with this.



