Enroll Additional Networks
The IP of the network from which you are connecting was added during initial setup (see Step 2). This network should already be active.
There are three ways you can enroll additional networks:
-
Use the setup wizard:
- Click 'Setup Wizard' at the top-right of the interface.
- Follow the steps to add your networks.
- See Step 2 for help with the wizard.
2. Manually add a network:
- You can add networks with static IP addresses by specifying their IP address in CIDR notation.
- You can add networks with dynamic IP addresses by installing our IP updater agent on the network.
- See Add Networks Manually for help with both these methods.
-
Deploy local resolvers to import a network:
- Install a local resolver (LR) as a virtual appliance on the network.
- Once deployed, the network is automatically imported to Secure Internet Gateway.
- See Import networks by deploying local resolvers for help to setup the local resolvers.
Networks you add manually have a 'pending' status until the IP/FQDN has been approved by Xcitium. Please contact your Xcitium account manager ordomesupport@Xcitium.comif you have questions on this.
Click the links below for help
Add Networks with Static IP Addresses
- Click 'Configure' > 'Objects' > 'Networks'
- Click 'Add New Network'
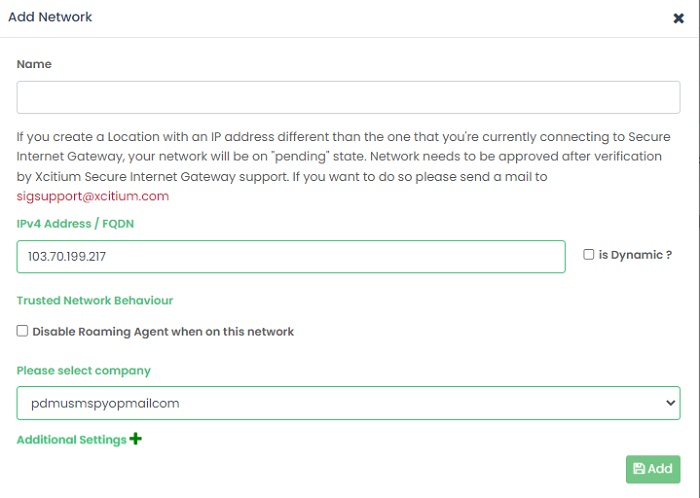
- Complete the new network form:
|
Field |
Description |
|---|---|
|
Name |
Create a label for the network. |
|
IP Address / FQDN |
Type the IP or fully qualified domain name of the network you want to add.
Any new network you add will have a ‘pending’ status until approved by Xcitium. Dynamic - Select if you want to add a network with dynamic IP addresses. See Add Networks with Dynamic IP addresses |
|
Trusted Network Behavior |
Disable Roaming Agent when on this network –Decide whether or not the network policy is applied to roaming devices when inside the network.
|
|
Please select company |
MSPs only
|
|
Remark |
Enter any notes, comments or advice about the network. |
|
Additional Settings - These settings only apply to roaming devices which have the XSIG agent installed.
|
|
|
Host File Configuration |
Enter the name and IP address of your host in the respective fields. Click the '+' button to add more host entries. |
- Click 'Add' when done.
The network is saved and shown in the list. Next:
Configure your network DNS to forward queries to XSIG DNS
You
need to change the
network's DNS to forward queries to XSIG DNS. This ensures all
endpoints are protected.
Change your DNS addresses to the following:
- Preferred DNS server - 8.26.56.10
- Alternate DNS server - 8.20.247.10
|
General Notes:
|
Add Networks with Dynamic IP Address(es)
Step 1 - Install the IP update agent on an endpoint in the network
- Click 'Configure' > 'Objects' > 'Networks'
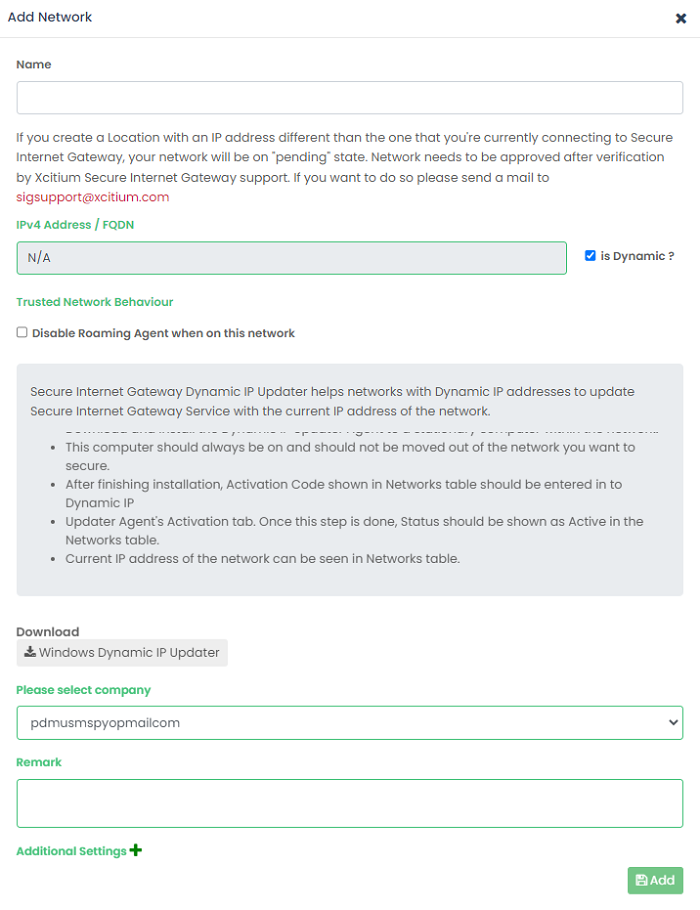
- Click 'Add New Network':
|
Field |
Description |
|---|---|
|
Name |
Create a label for the network |
|
IP Address / FQDN / Dynamic |
Enable 'Is Dynamic?' to enroll a network with dynamic IP addresses. A message box opens with help to enroll the network.
|
|
Trusted Network Behavior |
Disable Roaming Agent when on this network - Decide whether or not the network policy is applied to roaming devices when inside the network.
|
|
Please select company |
MSPs only.
|
|
Remark |
Enter any notes, comments or advice about the network. |
|
Additional Settings - These settings only apply to roaming devices which have the XSIG agent installed.
|
|
|
Host File Configuration |
Enter the name and IP address of your host in the respective fields. Click the '+' button to add more host entries. |
- Click 'Add' once you have completed the form.
The network is added to XSIG with a status of ‘Pending'. An activation code is also created for the network:
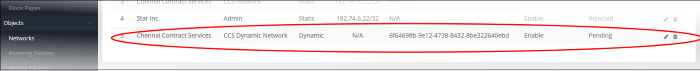
- Copy the agent setup files to an endpoint in the target network
- Install the agent on the target endpoint.
|
Note: Choose an endpoint which is always powered on and connected to the network. This lets the agent monitor IP address changes and send updates to Secure Internet Gateway. |
After installing the agent, you need to enter the network’s activation code to enable protection:
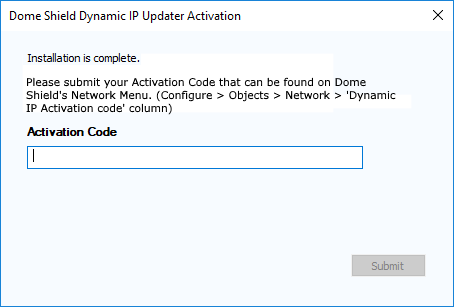
- Click 'Configure' > 'Objects' > 'Networks' to get the code:
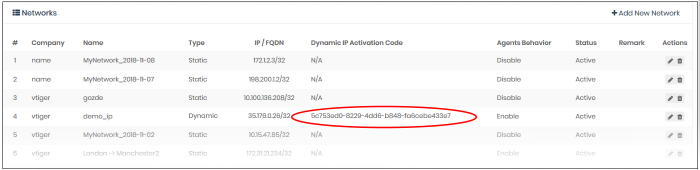
-
Paste the code and click submit
The network is now activated.
Note – No security policy is applied to new networks by default – you need to create/apply your own policy. See Step 5 - Create and Apply Security Policies for help with this.
Import networks by deploying local resolvers
- The local resolver virtual machine (VM) is an alternative way to import networks. The feature is only available with Platinum licenses.
- The resolver is deployed as a VM on your network and will forward public DNS queries to XSIG DNS servers.
- The network is automatically imported to XSIG after you deploy the resolver.
- The resolver method offers some key advantages over 'direct' enrollment:
- The resolver records the IP address of the client from which the DNS request originated. These addresses are included in Secure Internet Gateway logs and reports, giving you insight into the browsing patterns of endpoint users.
- You can apply different policies to internal IP addresses and sub-nets, giving you granular control over the network.
- You do not need to install agents on endpoints. You just need to change the DNS settings on the endpoint to point to the resolver's IP address.
- Local resolver VMs require minimal hardware (only one CPU and 1GB of RAM) to process millions of DNS queries.
Follow the steps below to install the LR VA and import a network:
Step 1 - Download the Setup File
- Login to Secure Internet Gateway
- Click 'Configure' > 'Objects' > 'Sites & Virtual Appliances'
- Click 'Download Component' at the top-right
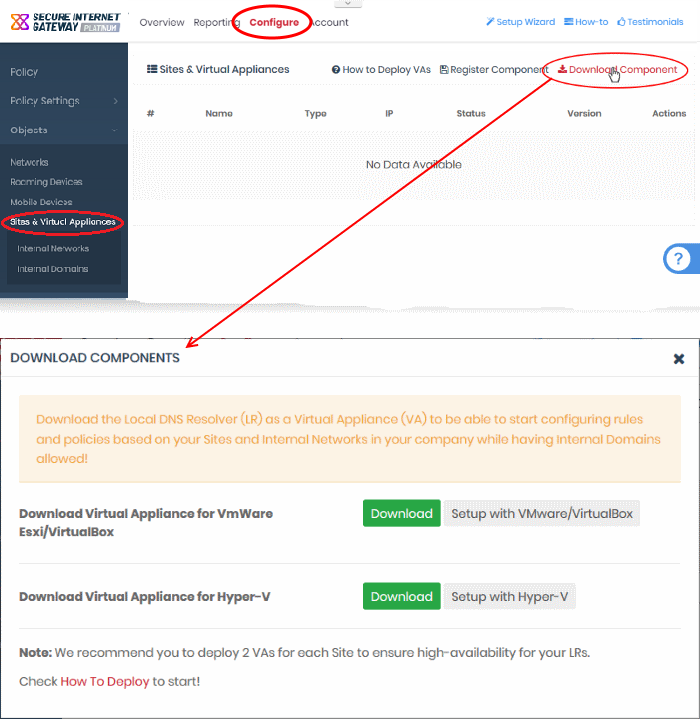
The appliance can be setup on virtual machines like VMWare, VirtualBox and Hyper - V.
- Click the 'Download' button beside the VM application you want to use
- The setup package contains an OVA or HYPER-V file depending on the VM you chose. The package also contains a text file with login credentials to access the appliance
Step 2 - Setup the Master Virtual appliance
- Copy the package to the hosts on which you want to setup the appliance.
- Extract the package.
- Install the virtual appliance.
The XSIG interface contains tutorials to help you install the VA on VMWare, VirtualBox and Hyper-V.
- Click Configure > Objects > Sites & Virtual Appliances
- Click 'How to Deploy VAs'
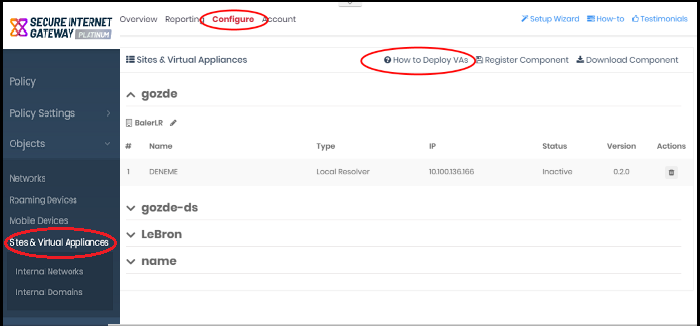
The instructions page explains how to install the VA on VMWare, VirtualBox and Hyper-V:
- Start up the VA once installation is complete.
- Login to the appliance with the username and password in credentials.txt. This file is in the VA package you downloaded.
- Run the 'sudo su' command and enter the root password contained in the 'credentials.txt'. This gives you root access.
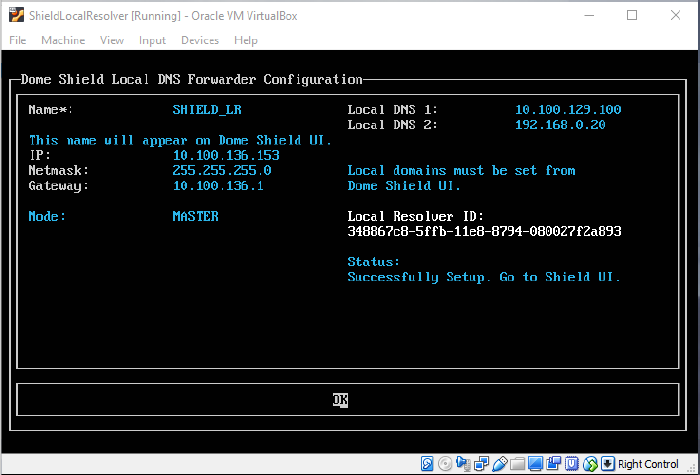
Run 'lr-gui' command as shown below to open the resolver configuration screen:
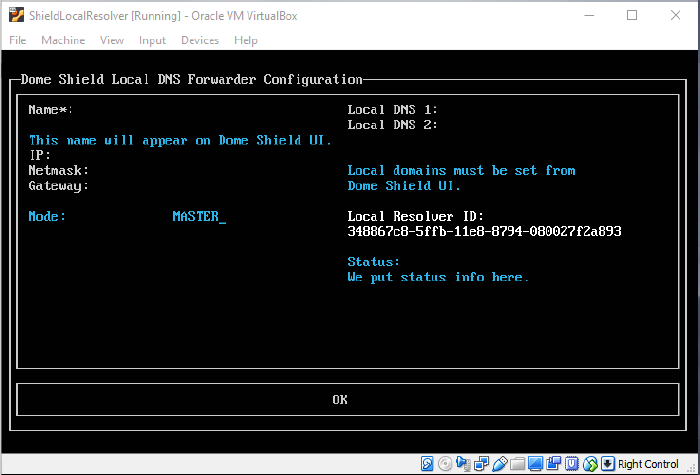
- Complete
all fields in the forwarder configuration screen.
- Make sure to copy the ‘Local Resolver ID’ string. You need this to register the device later.
|
Field |
Description |
|---|---|
|
Name |
Type a label to identify the master VA. This name will identify the VA in XSIG after registration. |
|
IP |
Assign an IP address to the local resolver. |
|
Netmask |
Enter the LR netmask. |
|
Gateway |
Enter the IP address of the network gateway. |
|
Mode |
Select 'Master' if this is the first resolver on the network. |
|
Local DNS 1 and Local DNS 2 |
Enter the IP addresses of the primary and secondary DNS servers in the network. |
|
Local Resolver ID |
Note this ID string. You need this to register the resolver in the next step. |
|
Status |
Progress of the VA setup process. |
- Select OK then press 'Enter' when finished. Your configuration is saved.
The next step is to register the LR in Secure Internet Gateway.
Step 3 - Register the Master VA
- Login to Secure Internet Gateway
- Click 'Configure' > 'Objects' > 'Sites & Virtual Appliances'
- Click 'Register Component'
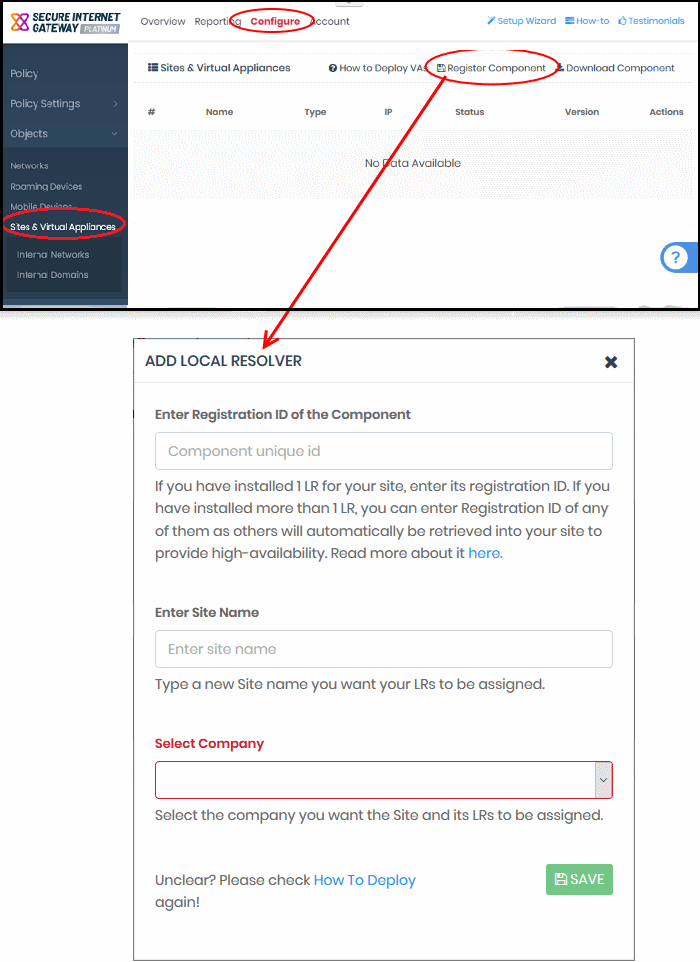
|
Form Element |
Description |
|---|---|
|
Enter Registration ID of the Component |
Paste the local resolver
ID
from the previous step. |
|
Enter Site Name |
Create a label for the network you are about to import. The name is used to identify the network in the XSIG interface. |
|
Select Company |
MSPs only.
|
- Click 'Save' to register the local resolver and import the network
- Apply a policy to the entire network site, or
- Define individual endpoints or sub-nets as objects and apply policies to them. See 'Add Internal Network Objects', next, for help with this.
Add Internal Network Objects (optional)
- Login to Secure Internet Gateway
- Click 'Configure' > 'Objects' > 'Internal Networks'
- Click 'Add New Internal Network'
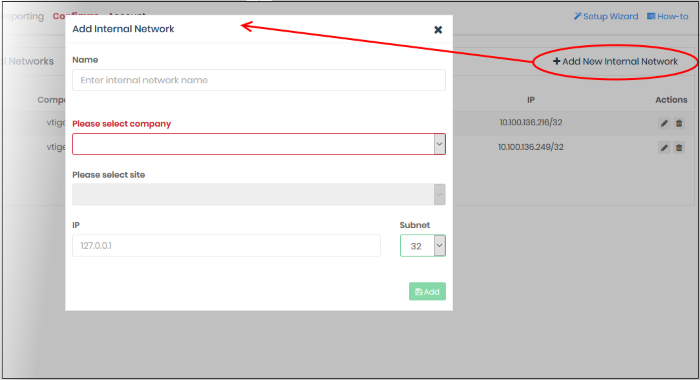
|
Field |
Description |
|---|---|
|
Name |
Create a label for the internal object. This name appears in the ‘Object’ drop-down for the site when you create a policy. |
|
Please select company |
MSP customer sonly.
|
|
Please select site |
Choose the site to which the internal network belongs. |
|
IP |
IP address of the internal network in CIDR notation.
|
- Click 'Add'.
- The internal network object is added to the list. It will be available in the 'Object' drop-down as a target when creating a new policy.
- Repeat the process to define more internal network objects.
Step 4 - Setup the Slave VA (Optional)
- For high availability, we recommend you deploy two local resolvers (LR's) for each network you import. The resolvers can be configured in a master-slave relationship. If the master fails, the slave will continue to forward queries to Secure Internet Gateway DNS.
- You need to install another local resolver VA on a different server/host on the network. The process is similar to setting up the master LR.
- Start the VA and open the configuration screen as explained above. Setup the VA as slave resolver.
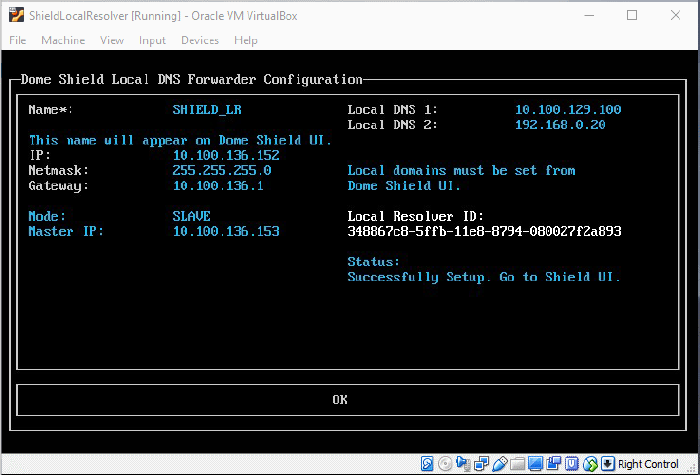
|
Field |
Description |
|---|---|
|
Name |
Type a label to identify the slave VA. This name will identify the VA in XSIG after registration |
|
IP |
Assign an IP address to the local resolver. |
|
Netmask |
Enter the LR netmask. |
|
Gateway |
Enter the IP address of the network gateway. |
|
Mode |
Select 'Slave'. |
|
Master IP |
Appears after choosing 'Slave' as the mode. Enter the IP address of the master local resolver. |
|
Local DNS 1 and Local DNS 2 |
Enter the IP addresses of the network's primary and secondary DNS servers. |
|
Local Resolver ID |
Note this ID string. You need this to register the resolver in XSIG. See Step 3 - Register the Master VA for more help. |
|
Status |
Progress of the VA setup process. |
- Complete all required fields, select OK, then press 'Enter'. The resolver is registered as 'Slave' to the 'Master'.
Step 5 - Configure DNS Settings on endpoints to point to the Local Resolvers
Open the DNS configuration screen on your endpoints and use the following settings:
- Preferred DNS server - IP address assigned to the master LR VA
- Alternate DNS server - IP address assigned to the slave LR VA



