Connect your Network(s) to Comodo SWG
- After setting up traffic forwarding, the next step is to add a 'Trusted Network'. Comodo SWG will not function correctly until you have done so.
- The default security and URL filtering policies are applied to all endpoints in trusted networks.
- You can also create network-specific policies.
This step explains how to add and manage networks in the 'Locations (Trusted Networks)' interface.
- Policies are prioritized top-to-bottom according to the list in 'Configuration' > 'Policy'.
- In the event of a conflict between policies over a security setting, the setting in the policy nearer the top of the list will prevail.
- You can change the priority of a policy by clicking 'Edit' > 'Policy Order' in the 'Configuration' > 'Policy' interface.
- Click 'Configuration' > 'Configuration' > 'Locations' to open the trusted networks interface:
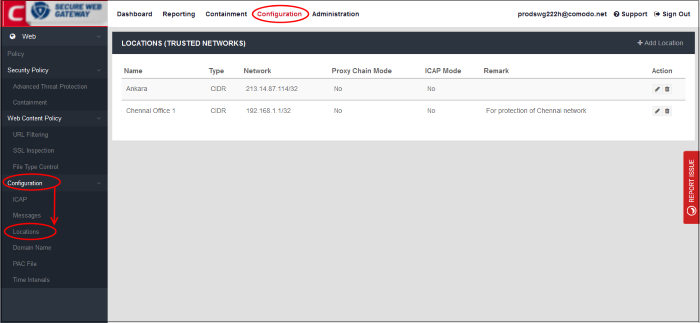
Add your location
- Click 'Add Location' at the top right of the interface
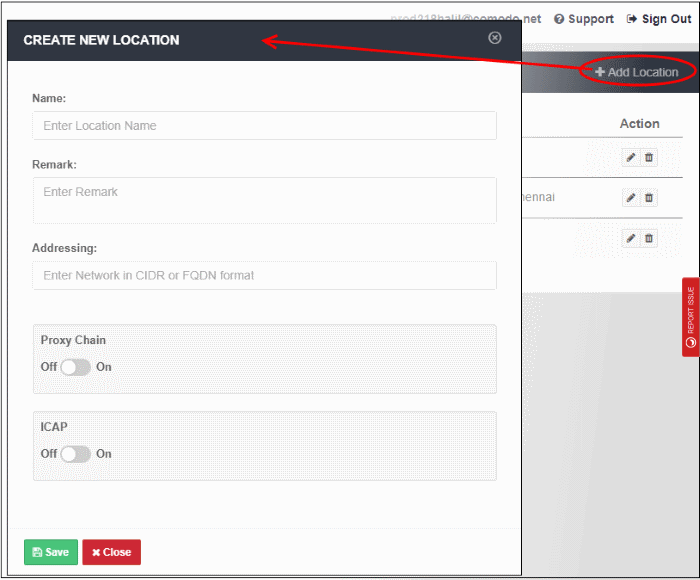
- Name - Enter an appropriate label for the location.
- Remark - Enter comments, if any, about the location.
- Addressing – The public IP or fully qualified domain name (FQDN) of the network that you have added. See Connect your Network to Comodo Secure Web Gateway if you need help with this.
- End user authentication and traffic forwarding - The method used for traffic forwarding and user authentication.
- Available options are 'Proxy Chain' and 'ICAP'. Select the appropriate method for your network.
- If you don't enable either then SWG agent authentication and traffic forwarding will be used.
- Note - If you enable user authentication then you must add and configure users in the 'User Management' interface.
- If you don't enable user authentication, then you cannot deploy user-based policies. Instead, network based rules or default rules will be applied to all users in the network.
- See steps 'Add Users' and 'Configure User Authentication Settings'.
- Click 'Save' to apply your changes
The location will be added and shown in the list. The default policy will be automatically applied to newly added network.



