Connect your Roaming Device(s) to Comodo SWG
Comodo SWG can protect roaming users who are outside a fixed network. This is especially useful for users on the move like field sales teams. It is also useful for remote workers who access the internet from outside your network.
- You must install the roaming agent on a device to connect it to SWG protection. This is because the device will use dynamic IP addresses.
- Once installed, any policies defined for 'Roaming users' will be applied to the device. If none are defined then the default 'Global Policy' is applied.
- Click 'Administration' > 'Traffic Forwarding' > 'SWG Agent Configuration' to download and configure the agent:
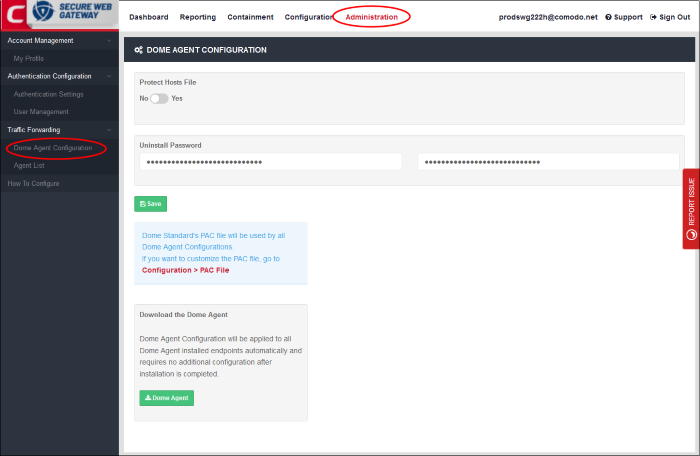
- Protect Hosts File - Determines whether a user can access non-public, internal domains.
- For example, if you have added an internal domain to the 'Hosts' file, then 'Comodo SWG' proxy cannot resolve it since it is not available publicly.
- The default setting is 'No'. If you select 'Yes', the internal domain will be accessible to the user. A direct connection is established between the internal domain and the remote device.
- Note – you can achieve the same result by configuring the PAC file or the proxy setting on the device's internet browser.
- Uninstall Password - The password required to uninstall the SWG agent from the roaming device.
- Configure PAC file - A proxy auto-config (PAC) file determines which proxy servers a browser or client should use to access a given URL. You can customize the PAC file according to your requirement. See 'Configure PAC File' for more details.
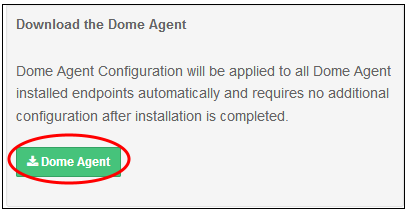
Download the 'SWG Agent'
- Click 'SWG Agent' button:
Click 'Save File' in the download dialog:
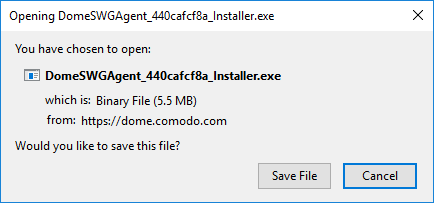
- Copy the agent to all roaming devices you want to protect.
Install the agent
- Run the agent setup file

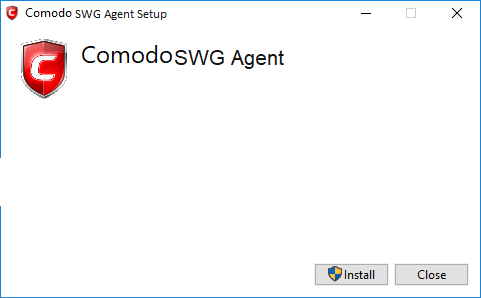
- Click 'Install'
- Click 'Close' after the agent installation is complete.
- Click 'Administration' > 'Traffic Forwarding' > 'Agent List' to view computers that have the agent installed. See 'View Enrolled Roaming Devices' if you need help with this interface.
- Note - If the devices are connected to networks that have been added to Locations then the location based rules will apply to them. Rules at the top of the list take precedence.
- You must have added users before you can apply policies to them. See steps 'Add Users' and 'Apply Policies'.



