Step 6 - Configure Secure Email Gateway Security Components
The 'Modules' section lets you configure Secure Email Gateway security components.
- Click 'Modules' on the left
- Help for each module is listed under the
following screenshot:
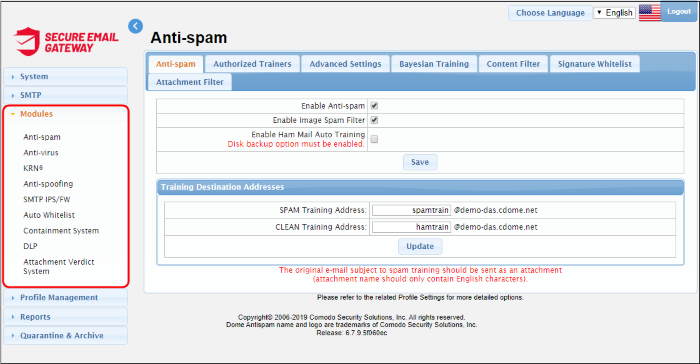
- Anti-spam General Settings - Enable/disable anti-spam and image filters. Ham mail = legitimate mail. Upload ham training materials help teach the antispam system to identify legitimate mail – useful if you are getting too many false-positives. The anti-spam module must be enabled in order to activate the anti-spam parameters specified in profile settings.
- Authorized Trainers - Define the sources from which spam training emails can be sent. Submitting sample spam emails allows the system to learn, adapt and protect against new spam types.
- Advanced Settings - The languages you select here will be analyzed for spam using the Bayesian spam classifier.
- Bayesian Training - The Bayesian engine analyzes emails for patterns which may indicate that the mail is spam. You can upload sample spam and HAM (legitimate) emails in order to 'train' the engine to provide more accurate verdicts.
- Content Filter – Add words that when detected in message body will be marked as spam
- Signature Whitelist – A list of digital signatures that came attached to white-listed emails. You can manually whitelist mails from the 'Mail Logs' interface.
- Attachment Filter – Define how many archive levels should be checked by Secure Email Gateway. For example, a zip file may contain another zip file inside it. A depth of '2' means Secure Email Gateway will check inside both files.
See 'Anti-Spam' in the main user guide for more information.
Configure antivirus settings and select the program that should be used for AV scans.
- General Settings – Enable / disable anti-virus and select the virus scanner.
- Advanced Settings – Define scanner settings such as size of mails that should be scanned, file types that should be scanned and so on.
See 'AntiVirus'
for more information.
Korumail Reputation Network is a system which assigns a trust rating to IP addresses. It not only includes traditional features such as real-time IP blacklists but also has ‘whitelist’ and ‘greylisting ignore’ features.
- Servers - A newly added KRN server will be in enabled status by default. Click the 'Yes' or 'No' link under the 'Enabled' column to switch between enabled and disabled statuses.
- Settings – Enable / disable Reputation Network blacklist, whitelist and whitelist triplet scan.
See 'Reputation
Network (KRN)' if you need more help with this.
Email spoofing is a technique used to forge email headers so that the message appears to originate from a source other than the true sender. You can configure the settings to check whether an email is being sent from an authorized server.
- Select 'Enable Anti-spoofing' check box
- Select the managed domain from the 'Choose Domain' drop-down and enter the IP addresses.
See 'Anti-Spoofing'
if you need more help with this.
Configure the intrusion prevention system (IPS) and firewall (FW) to protect against denial of service (DoS) and SYN attacks.
- General – Enable / disable SMTP IPS/FW module and configure the security profile.
- Whitelist – Add trusted networks so they will not be filtered by the SMTP IPS module.
- Blocked – Add IP addresses so that mails from these sources never reach the SMTP level for processing.
- Rate Control - The 'Rate Control' feature protects your company from spammers that send huge amount of emails to the server in a small amount of time. Configure the rate control settings in order to automatically add IP addresses to blacklist if the set threshold is exceeded.
See 'Rate
Control' if you need more help with this.
Configure this setting to automatically trust emails sent between specific senders and recipients.
- The threshold means how many emails must be exchanged before the remote sender is added to the whitelist. The threshold must be achieved within the 'Maximum Day Count' underneath this setting.
See 'Auto
Whitelist' if you need more help with this.
- Protects users from zero-day malware by opening any untrusted attachments in a secure, virtual environment known as the container.
- Items in the container are not allowed to access other processes or user data and will write to a virtual hard-drive and registry.
- Secure Email Gateway checks the trust rating of all attachments. PDF and .exe attachments with a trust rating of 'Unknown' are removed and replaced with a link.
- The link allows recipients to download a special version of the file wrapped in Comodo's containment technology. The file will be open in a virtual container on the endpoint
- Data loss prevention helps stops sensitive information from leaving your organization via email. You configure it by specifying keywords that should be monitored.
- If triggered, you can configure actions such as quarantine or block the mail.
- You specify the keywords themselves in the SEG profile.
- DLP – Enable / disable DLP, Incoming Profiles and Outgoing Profiles.
See 'Data
Leak Prevention' if you need more help with this.
Configure to submit email attachments (executable and pdf files) that are rated as 'Unknown' to Valkyrie, a file analysis and verdicting system.
- General Settings – Enable / disable attachment verdict system. Provide your SEG license key. The host name is by default set to Valkyrie.
See 'Attachment Verdict System' if you need more help with this.



