CIS Premium – Installation
- Before beginning installation, please ensure you have removed any other antivirus and firewall products that are on your computer.
- Next, download the setup file from https://www.comodo.com/home/internet-security/free-internet-security.php.
- After
saving, run the setup file
 to start the installation
wizard.
to start the installation
wizard.
Step
1 - Choose the Interface Language and Installation Options

- Select the language - CIS is available in multiple languages. Choose the language in which you want to install Comodo Internet Security from the drop-down
- EULA - View the end user license agreement and privacy by clicking the links at the bottom of the screen:
After reading the agreements, click the 'Close' button to return to the installation configuration screen.
Options
- Click the options button if you want to configure install path, CIS components and other general settings
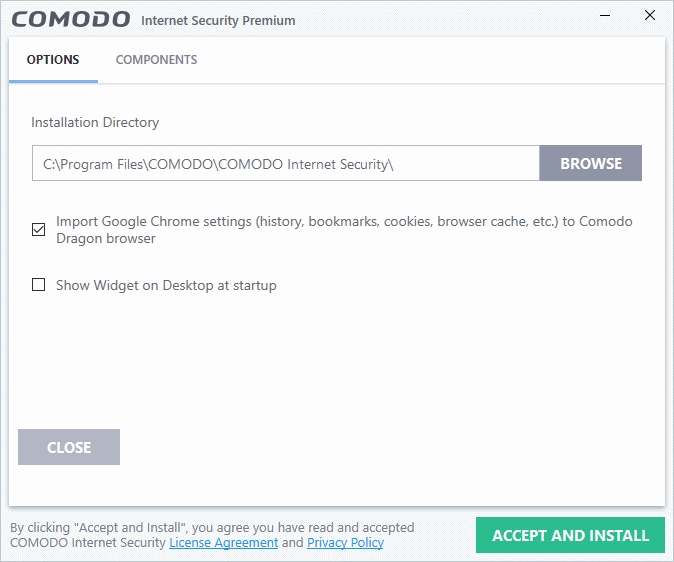
- Installation Directory – Click 'Browse' to change the CIS installation folder. The default path is C:/Program Files/COMODO/COMODO Internet Security.
- Import Google Chrome settings (history, bookmarks, cookies, browser cache, etc.) to Comodo Dragon browser – Comodo Dragon is a fast and versatile internet browser based on Chromium and infused with Comodo's unparalleled level of security. Dragon is installed with CIS by default.
- Select this option to automatically import your bookmarks, history and other data from Google Chrome browser to Comodo Dragon.
- Show Widget on Desktop at startup - The CIS widget is a handy control that provides at-a-glance information about your security status, speed of outgoing and incoming traffic, and the number of active processes.

- Select this option if you want the widget to be shown automatically on your desktop
- You can enable or disable the widget later by right-clicking on the CIS system icon after installation.
Components:
The components tab lets you select which features you want to install:
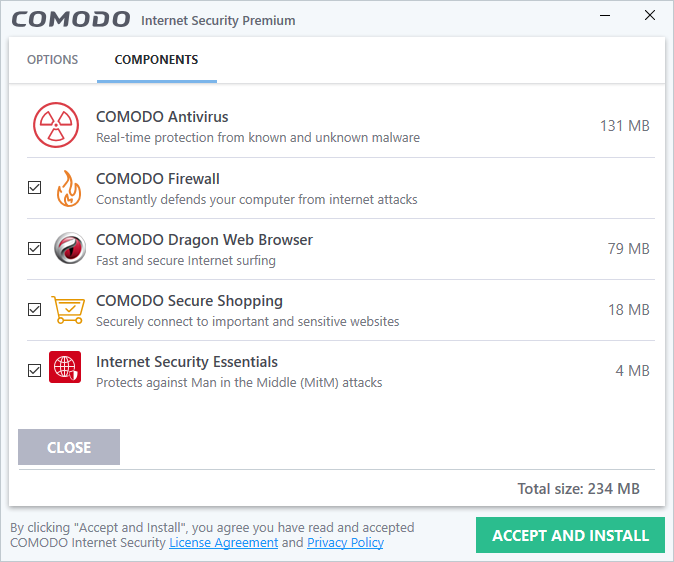
- COMODO Antivirus – Installs the antivirus scanner and the HIPS, containment and VirusScope modules. Deselect this option if you already have an antivirus product that you want to use instead.
- COMODO Firewall - Installs Comodo Firewall and the HIPS, containment and VirusScope modules. Deselect this option if you already have a firewall that you want to use instead.
- COMODO Dragon Web Browser - Installs Dragon, a fast and versatile internet browser based on Chromium technology and infused with Comodo's unparalleled level of security. See Dragon Browser for more details.
- COMODO Secure Shopping - Installs Comodo Secure Shopping, a security hardened virtual environment which offers complete protection for online banking and shopping. See Comodo Secure Shopping for more details.
- Internet Security Essentials – Installs Internet Security Essentials, an application that protects you from the man-in-the-middle attacks while using the internet for services such as online banking and so on. See Comodo Internet Security Essentials for more details.
- Click 'Close' when you are satisfied with your settings.
- Click 'Accept and Install' in the 'Welcome' screen to begin installation.
Step 2 - Installation Progress
The selected components will be installed:
Step 3 - Finalization
The last step is to set some CIS options:
Change my DNS provider to COMODO Secure DNS
- This option changes your computer's DNS settings to point to Comodo Secure DNS servers. You can disable the service later at anytime and revert to your previous settings.
- Comodo Secure DNS resolves your DNS requests through Comodo's proprietary Directory Services Platform. Comodo's worldwide network of redundant DNS servers provide fast and secure internet browsing without any hardware or software installation.
- Comodo Secure DNS also protects you by blocking access to malicious sites by any program running on your computer.
- See Appendix 2 Comodo Secure DNS Service for more details on how to configure Comodo Secure DNS.
- The 'What is this' link has more information about Comodo Secure DNS.
Enable
'Cloud Based Behavior Analysis' of untrusted files
- CIS submits any file with an 'unknown' trust-rating to Comodo for behavior analysis. Unknown files are subjected to a range of static and dynamic tests to determine whether they behave in a malicious manner. The results will be sent back to your computer in around 15 minutes. Comodo recommends users leave this setting enabled.
Send
anonymous program usage statistics
- CIS
will send anonymous crash and usage data to Comodo. This
data helps us identify the areas of the program which need to be
improved. Your privacy is
protected because all data is anonymized and sent over a secure and
encrypted channel. Disable this option if you do not want to send
usage details. You can also change this setting in the Log
Settings interface at anytime
after installation.
Enhance my web browsing experience by setting Yahoo! as my home page, new tab and default search engine (all supported browsers).
This
means:
- When you enter a search item into the address bar of a supported browser, the search will be carried out by Yahoo
- A 'Search with Yahoo' menu entry will be added to the right-click menu of supported browsers.
- Yahoo will be set as the default search engine in the 'Search' box of supported browsers
- The instant 'search suggestions' that you see when you start typing a search item will be provided by Yahoo.
- Clear the checkbox if you do not want to set Yahoo! as your home page, new tab and default search engine.
Set Comodo Dragon as default browser
- Use
Comodo Dragon as the default to open web-pages
Click
'Finish' to complete the installation.
Once setup is complete,
the application runs a virus scan on your computer. The scan covers
critical areas of your computer, system memory, autorun entries,
hidden services and boot sectors. The virus database will be updated
automatically prior to the scan.
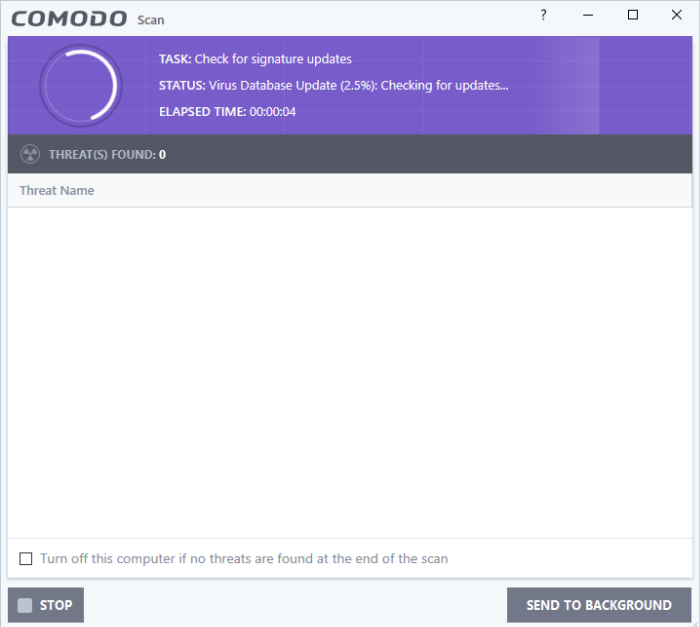
- Click 'Send to Background' to make the task consumer fewer resources. Background tasks can be viewed in the 'Task Manager' interface.
- Click 'Stop' If you do not want the scan to continue at this time.
- Results will appear at the end of the scan. The results show the number of objects scanned and any identified threats:
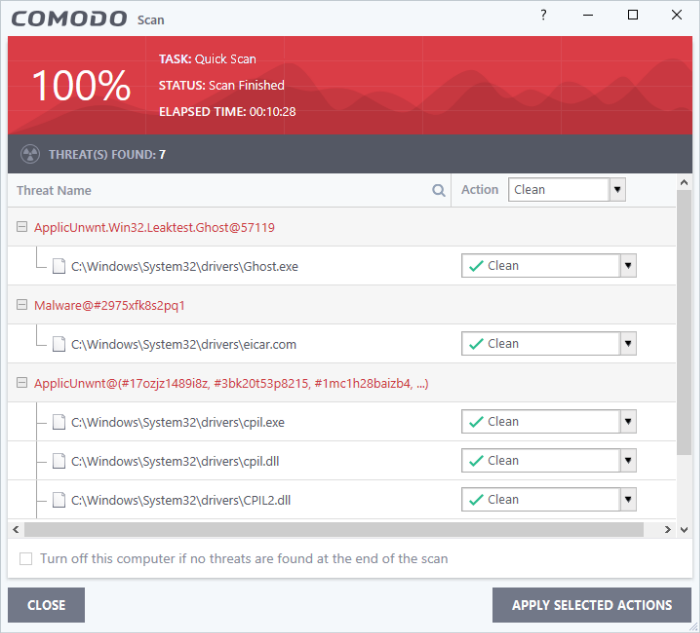
- Select 'Clean' from the drop-down at top-right and click 'Apply Selected Actions' to remove all threats from your computer. See 'Process Infected Files' if you need more help.
Step 4 - Select your location
Select your location so that the firewall can apply the correct settings for your connection. The top of the dialog shows whether you are using a wired or wireless connection.
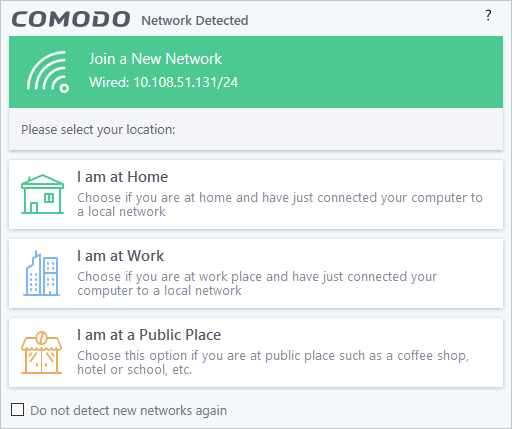
- Select 'Do not detect new networks again' if you are an experienced user that wishes to manually set-up their own trusted network. This can be done in 'Network Zones' and through the 'Stealth Ports Wizard'.
Step 5 - Restart Your System
Your computer needs to be restarted in order to finalize installation:
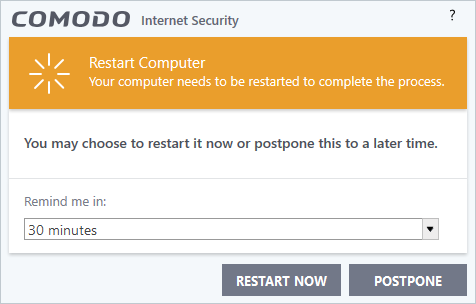
- If you want to restart your computer immediately, save all your work and click 'Restart Now'.
- If
you want to restart the computer at a later time, select a period
from the drop-down and click 'Postpone'.
Step 6 - After Restarting Your System
A welcome screen appears immediately after restart. This summarizes the components you have installed and offers advice on using the product. You also a purchase a Pro/Complete license key from this screen if required.
- Do not
show this window again – The welcome screen will not be shown
the next time you restart.



