Introduction to Comodo Forensic Analysis
It is estimated that traditional antivirus software can only catch 40% of all malware in the world today. The other 60% are 'unknown'. An advanced persistent threat (APT) is an 'Unknown' piece of malware that is so well disguised it can be months before a traditional antivirus catches up to it. These malicious files reside on the victim's computer during this whole time, executing their payloads all the while.
Comodo
Forensic Analysis (CFA) is a lightweight scanner which identifies
unknown, and potentially malicious files, residing on your network.
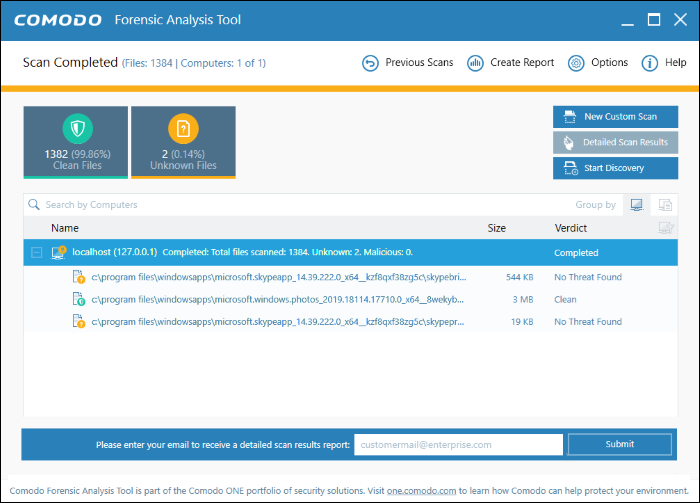
After scanning your systems, it will classify all audited files as
'Safe', 'Malicious' or 'Unknown'. While 'Safe' files are OK and
'Malicious' files should be deleted immediately, it is in the
category of 'Unknown' that most zero-day threats are to be found. The
CFA scanner automatically uploads these files to our Valkyrie servers
where they will undergo a battery of run-time tests designed to
reveal whether or not they are harmful. You can view a report of these tests in the CFA interface. You can also opt to have detailed scan reports sent to your email. The CFA interface displays results of both files analyzed by Forensic Analysis and Valkyrie analysis.
Features
- No installation required, just run the portable application on any computer in the network
- Scan local machines or specify target endpoints by Active Directory, Work Group or network address. The scan discovers all computers available in a given network
- Unknown files are automatically uploaded to Comodo Valkyrie and tested for malicious behavior
- Comprehensive reports provide granular details about the trust level of files on your endpoints
This guide takes you through the use of Comodo Forensic Analysis and is broken down into the following sections:



