Threats Report
The 'Threats Report' interface provides a comprehensive report of threats that were encountered by the secure applications. The details include the name of the endpoint and its ID assigned by the management console, the details of secure applications, when the CSB was installed and more. The report for the threat categories generated here for the computer groups depends on the settings configured in the log filter section of the computer group properties dialog. The available threat categories are:
- Fake Certificate
- Remote Detected
- Malware Terminated
|
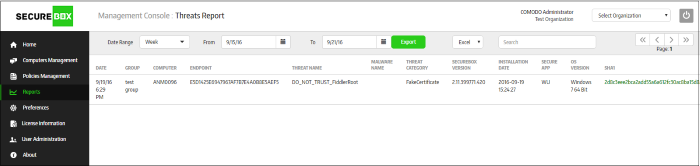
Threat Report – Table of Column Description |
|
|---|---|
|
Column |
Description |
|
Date |
The date and time of threat recorded on the endpoint |
|
Group |
The computer group to which the endpoint belongs. Refer to the section 'Managing Endpoint Groups' for more details. |
|
Computer |
The name of the endpoint that was detected by CSB on enrollment. Refer to the section 'Enrolling Endpoints for Management' for more details. |
|
Endpoint |
The ID for the endpoint assigned by CSB on enrollment. |
|
Threat Name |
The application name which is detected as a threat, for example, AKLT.exe, Windows Remote Desktop and so on. |
|
Malware Name |
The malware name, which is the result of FLS scan. But not every threat log has the Malware name, for example, remote detect is a threat log but it has no malware name. |
|
Threat Category |
The category of the threat that was recorded on the enrolled endpoints:
For configuring the threat email notifications, the name of the threat category should be provided in the 'Category' row in the 'Preferences' interface > 'Threat Notifications' > 'Add New' button. Refer to the section 'Configuring the Management Console' for more details. |
|
SecureBox Version |
The details of the CSB version that is installed on the endpoints. |
|
Installation Date |
The date and time when the CSB was installed on the endpoints |
|
Secure App |
The name of the secure application for which the threat was recorded. |
|
OS Version |
The details of the endpoint's operating system |
| SHA 1 |
The SHA1 value of the secure application. |
Sorting, filtering and searching options
Sorting the entries
Clicking any column heading sorts the entries based on the ascending/descending order of the entries as per the information displayed in the respective column.
Using the filter option
The threat report can be filtered
using the date range and can be further filtered by providing the
'From' and 'To' dates. Please note the availability of past reports (up to one year) depends on the settings configured in 'Report Settings' from the 'Preferences' screen.
- Click the 'Date Range' drop-down box.
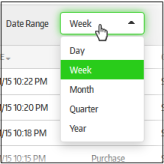
By default, 'Week' will be selected for the date range and the dates in the 'From' and 'To' will be for the last 7 days and the results displayed.
-
To refine the search further, provide the 'From' and 'To' dates by clicking on the combo boxes and selecting the dates from the calendar.
To export the report
CMC allows administrators to save the generated threat report to your system.
- Click the 'Export' button (currently only .xls format is supported)
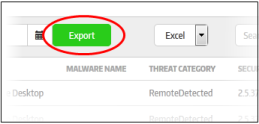
You can choose to save the file or open with any spreadsheet application.
- Click 'OK'
The file will be saved in your default download location.
Using the search option
- Enter the search details of items under any of the columns in the box fully or partially.
The search will begin automatically and results displayed.



