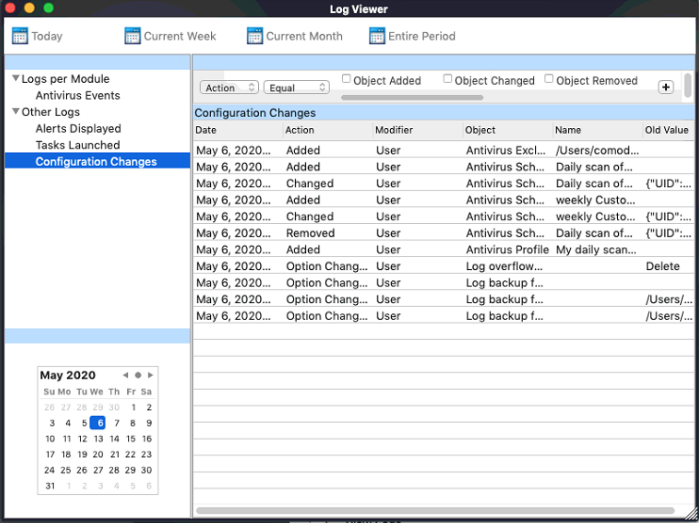
Filter 'Configuration Change' Logs
You can create custom views of logged events according to the following criteria:
- Action: Filter by the activity performed on the item in the 'Object' column. For example, 'Added', 'Changed'.
- Modifier: Filter by who, or what made the change.
- Name: Filter by the file/folder/path involved in the configuration change. For example, a particular folder/file was added to a scan profile.
- Object: The antivirus feature that was modified in the event. For example, AV profile, AV exclusion and so on.
Configure Event Filters
- Open Comodo Client Security
- Click 'More' > 'View Logs' > 'Other Logs' > 'Configuration Changes'
- Right-click inside the log viewer module and choose 'Advanced Filter'
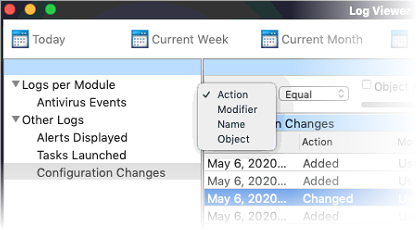
- Action: Filter events by updates to the configuration settings such as profile added and so on. You can filter by a specific type of action. For example, to only show events where an object was added.
- Select 'Equal' or 'Not Equal' option from the second drop-down.
- Equal – Show only events which feature the action you select. You can select multiple actions.
- Not Equal - Inverts your choice. For example, select 'Not Equal' + 'Object Added' to view every event except those that were objects were added.
- Select the specific actions you want to view from:
- Object Added – Events where an item was created
- Object Changed – Events where an item was modified. For example, an update to a scan profile.
- Object Removed - Events where an item was deleted
- Option Changed – Events where a setting was modified. For example, 'Show scan progress' was changed from enabled to disabled.
- String Added – Not used.
- String Removed– Not used.
- Modifier: Filter events by entity that updated the configuration.
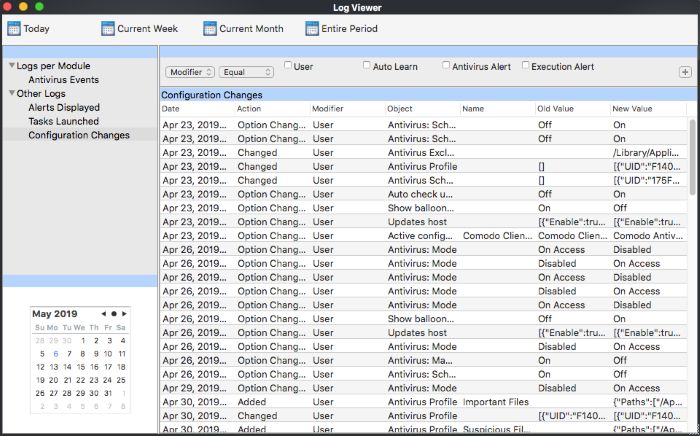
- Select 'Equal' or 'Not Equal' option from the second drop-down.
- Equal – Show only events which feature the action you select. You can select multiple actions.
- Not Equal - Inverts your choice. For example, select 'Not Equal' + 'User' to view every event except those that were modified by the user.
- Select the specific actions you want to view from:
- User – Events that were modified by the user
- Auto Learn - Not used
- Antivirus Alert - Not used
- Execution Alert - Execution alert is reserved for future version of CCSM
- Name: Filter events by files/folders/path of files that was involved in the configuration change. For example, a particular folder/file was added to a scan profile. You need to enter the label in the field provided:
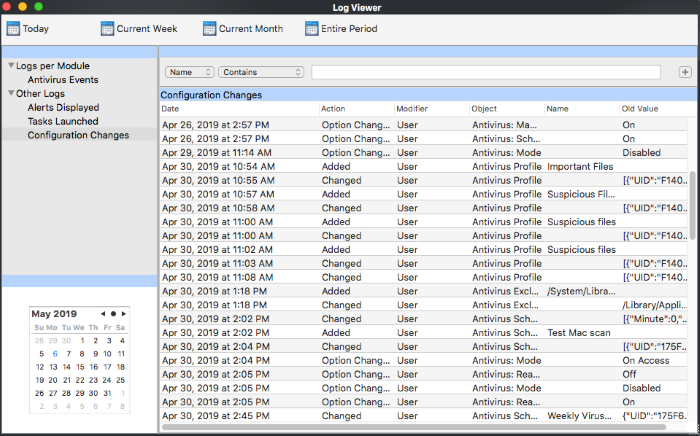
- Select 'Contains' or 'Does Not Contain' from the second drop-down:
- Contains – Show only those events which concern items that you specify. You can add multiple names.
- Does Not Contain – Show events which did not concern names that you specify.
- Object: Filter events by the item that was changed. Examples include AV profile, AV schedule, AV alert timeout, and more.
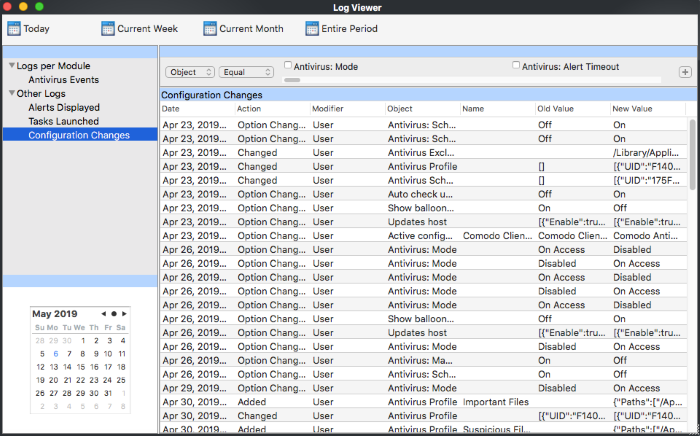
- Select 'Equal' or 'Not Equal' from the second drop-down.
- Equal – Show only events which feature the action you select. You can select multiple actions.
- Not Equal - Inverts your choice. For example, select 'Not Equal' + 'Antivirus: Alert Timeout' to view every event except those of changes to AV alert timeout settings.
- Select the specific actions you want to view from:
- Antivirus: Mode
- Antivirus: Alert Timeout
- Antivirus: Real-Time Show Alerts
- Antivirus: Real-Time Scan Memory
- Antivirus: Real-Time Auto Update
- Antivirus: Real-Time Auto Quarantine
- Antivirus: Real-Time Size Limit
- Antivirus: Real-Time Time Limit
- Antivirus: Manual Scan Archives
- Antivirus: Manual Scan Memory
- Antivirus: Manual Auto Update
- Antivirus: Manual Size Limit
- Antivirus: Scheduled Scan Archives
- Antivirus: Scheduled Scan Memory
- Antivirus: Scheduled Scan Auto Update
- Antivirus: Scheduled Auto Quarantine
- Antivirus: Scheduled Size Limit
- Antivirus Profile
- Antivirus Schedule
- Antivirus Exclusion
- Antivirus: Disable Logging
- Active configuration index
- Password protection
- Antivirus: Suppress Alert when password protected
- Show balloon messages
- Auto check updates
- GUI language
- Password
- Updates host
- Log file size limit
- Log overflow handling
- Log backup folder
- Antivirus: Write to syslog server
- Syslog server host
- Syslog server port



