Configure General SSL VPN Server Settings
This section allows you to:
- Enable/disable the SSL VPN server
- Configure the local network zone to which the connection should be bridged.
- Dynamically assign IP addresses to clients connecting to the server.
- Download
the SSL certificate that clients need to authenticate themselves to
DFW. See 'Configure
Clients to Connect to DFW' for help to to establish connections between individual clients and Dome Firewall.
To configure general settings for SSL VPN Server
- Click 'VPN' > 'SSLVPN Server' on the left hand-menu
- Click the 'Server Configuration' tab:
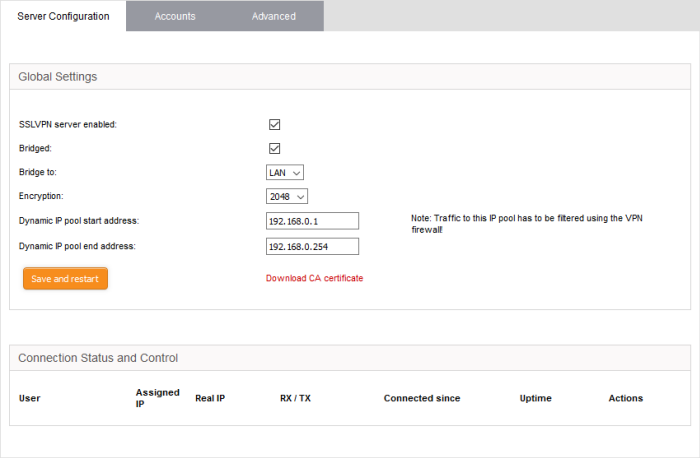
- SSLVPN server enabled - Enable or disable the SSL VPN server
- Bridged – Select whether or not the SSL VPN Server should be bridged to any of the internal network zones..
- If 'Bridged' mode is enabled, you have to specify the internal network zone to which the server is to be mapped. You can also specify the start and end addresses of the pool from which addresses should be assigned to clients.
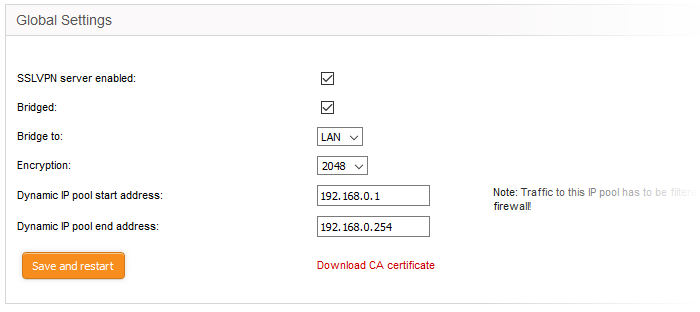
- Bridge to – The drop-down shows the internal network zones connected to the interfaces of the firewall. Choose the local network zone to which the server should be bridged.
- Dynamic IP pool start/end addresses - Enter the first and last addresses of the pool from which IP addresses are dynamically assigned to clients connecting to the server. These addresses should be from the subnet of the network zone to which the server is bridged. All traffic from these addresses will pass through the firewall, if enabled for the zone. See 'Manage Firewall Policy Rules' for more details.
- If 'Bridged' mode is disabled, specify the VPN subnet from which the IP addresses are to be assigned to the clients. Ensure that the VPN subnet is different from the subnets of the network zones configured in the firewall. In order for the clients assigned with IP addresses from this subnet to access the internal network zones, appropriate firewall rules are to be added to the policy. See 'Manage Firewall Policy Rules' for more details.
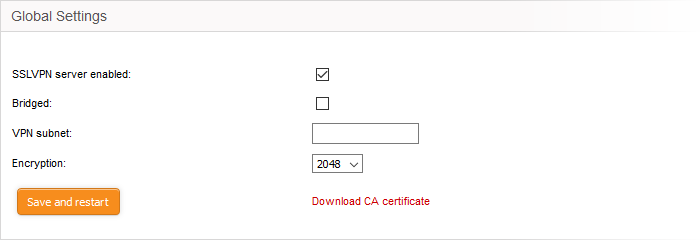
- VPN Subnet – Enter the subnet from which the IP addresses are to be dynamically assigned to the clients.
- Encryption – Select the encryption bit strength of the server certificate to be generated. The available options are 1024. 2048 and 4096 bits
- Click 'Save and Restart' to apply your changes.
- Click 'Download CA certificate' to download the server certificate for export to the clients. The certificate can also be downloaded from the 'Accounts' interface. For more details on certificate settings, see Configure Advanced SSL VPN Server Settings > Authentication Settings.
The lower pane of the interface displays a list of active SSL VPN connections to the server with their connection statistics. Admins can terminate unwanted VPN connections should they wish.
|
SSL VPN Server Connection status and control table - Column Descriptions |
|
|---|---|
|
Column |
Description |
|
User |
The name of the user who logged-in. |
|
Assigned IP |
The IP address dynamically assigned to the client from the server during the current session. |
|
Real IP |
The original externally facing IP address of the client. |
|
RX / TX |
Amount of data sent and received during the current session. |
|
Connected since |
The date and time that the session began. |
|
Uptime |
The length of time that the connection has been active. |
|
Actions |
Controls for terminating the session. |
See 'Configure Clients to Connect to DFW' (later in this section) for more details on how to connect individual clients to DFW.



