Manage VPN Firewall Rules
- Click 'Firewall' > 'VPN traffic' in the left-hand menu to open the VPN firewall policy interface
- Dome
Firewall supports two types of VPN traffic – SSL VPN and L2TP /
IPSec
- SSL VPN – You need to configure SSL VPN server, add client accounts and install OpenVPN clients on endpoints. See 'SSL VPN Server' and its subsections for more details
- L2TP / IPSec – You need to configureL2TP server, IPSec connection type and add IPSec / L2TP users
- After configuring them, SSL VPN server, SSL VPN user accounts and IPSec connections will become available as firewall objects. These objects can be used to populate 'source' and 'destination' fields in various interfaces.
- Note – Create rules for network FW traffic in 'Firewall' > 'Policy' for easy management of internal and external networks FW rules. See 'Manage Firewall Policy Rules' for more details.
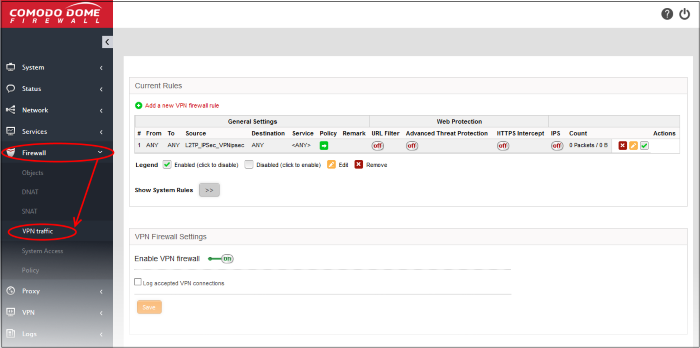
- Current Rules - Current Rules - Lists all currently active rules and allows you to add and edit rules. See Manage VPN Traffic Rules for more details on viewing and managing the rules.
- VPN Firewall Settings - Enable or disable the firewall. Choose whether you want to log all VPN connections which get allowed by the firewall policy. See Configure the VPN Firewall Settings for more details.
|
|
VPN Firewall Rules Table |
|
|---|---|---|
|
Category |
Column |
Description |
|
General Settings |
# |
Serial number of the rule. |
|
From |
Incoming interface. The entity which is the source of the traffic covered by this rule. This can be an interface device, VPN tunnel or network zone. |
|
|
To |
Outgoing interface. The entity which is the destination of the traffic covered by this rule. This can be an interface device, VPN tunnel or network zone. |
|
|
Source |
Source address. The firewall object or object group from which the traffic originates.
The objects contain the source addresses. These may be in the form of an IP address, IP address range, the subnet of the hosts, SSL VPN, SSL VPN users, or IPSec connection type. |
|
|
Destination |
Destination address. The firewall object or object group to which the traffic is sent. The objects contain the destination addresses. These may be in the form of an IP address, IP address range, the subnet of the hosts, SSL VPN, SSL VPN users, or IPSec connection type. |
|
|
Service |
Protocol and port that used by traffic affected by this rule. |
|
|
Policy |
The action taken on data packets intercepted by the rule:
|
|
|
Remark |
A short description of the rule. |
|
|
Web Protection |
URL Filter |
Whether or not the 'Web Filter' security profile is enabled for the rule. You will see the name of the profile if it is enabled. |
|
Advanced Threat Protection |
Whether or not the 'Advanced Threat Protection' component is enabled for the rule. |
|
|
HTTPS Intercept |
Whether or not the 'HTTPS Intercept Web Filter security profile' is enabled for the rule. If enabled you will see the name of the profile. |
|
|
|
IPS |
Whether or not the 'Intrusion Protection System (IPS)' security profile is enabled for the rule. |
|
Count |
Indicates the number of packets and size of data intercepted by the rule. |
|
|
Actions |
Controls for managing the rule.
|
|
- Clicking the right arrow button beside 'Show system rules' displays a list of firewall rules auto generated by DFW. These rules cannot be modified or removed.
Create Firewall rules for VPN Traffic
- Creating a VPN FW rule is similar to creating network FW rule as explained in 'Manage Firewall Policy Rules'. Click here to find out how how to add a FW rule.
- In the source and destination address fields, select SSL VPN, SSL VPN user or the IPSec connection type ('Net-to-Net' and 'L2TP Host-to-Net') to create rules for VPN traffic.
Configure
VPN Firewall Settings
The lower pane lets you enable/disable the VPN firewall policy, and to log all connections which get allowed by the policy.
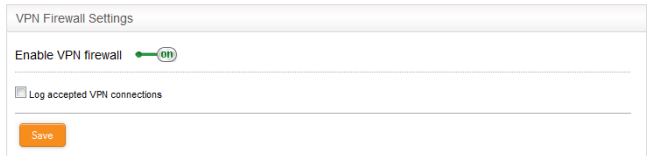
- Click 'Save' for your settings to take effect
Logged items include date, time,
type of event, subject id, component name and event outcome.




 - Enable or disable the rule.
- Enable or disable the rule. - Modify the rule. The 'Edit' interface is
similar to Add Rule interface. See
- Modify the rule. The 'Edit' interface is
similar to Add Rule interface. See  - Removes the rule.
- Removes the rule.