Introduction to Comodo SecureBox
Comodo SecureBox protects applications by isolating them inside a heavily-protected, fully functioning container within an endpoint operating system. Unlike a traditional sandbox which is used to house potentially hostile files, SecureBox protects the application itself and treats all outside processes as hostile. By isolating critical applications from other running processes, Comodo SecureBox prevents data exfiltration, remote takeover, keylogging, SSL sniffing, memory scraping and zero-day malware.
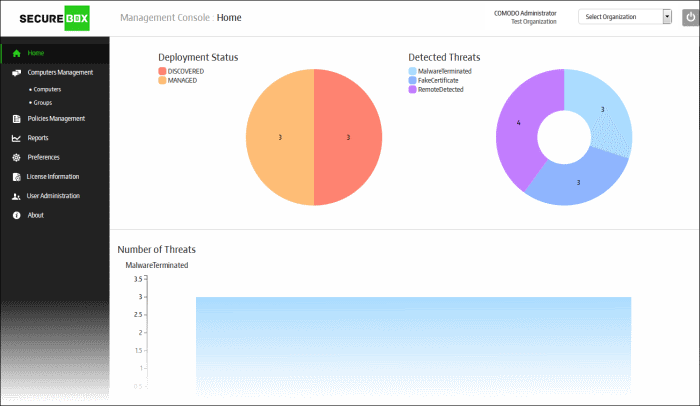
The Management Console allows administrators to control and monitor large-scale deployments of SecureBox on enterprise networks. It features a highly informative graphical dashboard, a detailed reporting sub-system, instant threat and activity notifications and the ability to define granular security policies for different endpoint groups. Security policies are constructed by adding one or more of the following types of secure app:
- 'URL Mode' app - Opens specified websites inside the secure box environment
- 'App Mode' app - Opens specified applications inside the secure box environment
- 'Folder Mode' app - Opens specified folders and files inside the secure box environment
The console is available in both SaaS and on-premises deployment models while endpoints can easily be imported via active directory or work-group.
SecureBox will allow you to create a threat-resistant tunnel to specific websites or portals, protect client applications from outside interference during run-time and to shield entire data repositories from attack.
Features
- Capable of securing applications in URL, application and folder modes
- Root certificate checking
- Website certificate checking
- Protects against the following:
- SSL connections sniffing
- DLL injection
- Keyboard sniffing
- Copy/paste operation
- Access by other processes
- Virus damage
- Remote control
- Unauthorized data access (data isolation)
- Unauthorized application running (application filtering)
- Unauthorized URL access (URL filtering)
Guide Structure
This guide is intended to take you through the configuration and use of Comodo Secure Box and is broken down into the following main sections.



