Manage Advanced Threat Protection Profiles
- Click 'Advanced Threat Protection' on the left to open this interface.
- Advanced Threat Protection (ATP) safeguards networks against malware, hack attempts, data breaches and other attacks.
- ATP scans internet downloads and email attachments with a combination of antivirus scans, behavior analysis and blacklist checks.
- This interface lets you configure ATP profiles for organizations and devices.
- You can then select these profiles when creating firewall rules for organizations and devices.
ATP uses the following techniques to analyze files:
- Comodo Antivirus - Continuously updated antivirus scanner which provides dependable protection against known malicious files.
- Comodo Valkyrie - A cloud based behavior analysis service which improves detection of zero-day threats by rigorously testing the run-time actions of unknown files.
The antivirus and Valkyrie tests provide a trust verdict for each file. There are three possible verdicts:
- Safe – Trusted files. These are allowed to run on the endpoint.
- Threats – Malicious files. These are automatically blocked and a warning shown on the endpoint.
- Unknown - Files that could not be identified as safe or threatening are classified as 'Unknown'. Users are not allowed to download these files directly. Instead, they are are wrapped in Comodo's containment technology and forwarded to the endpoint. When executed, the file runs in a secure virtual environment and is not allowed to access other processes or user data.
The ATP Profile
- Click 'Advanced Threat Protection' on the left to open the interface.
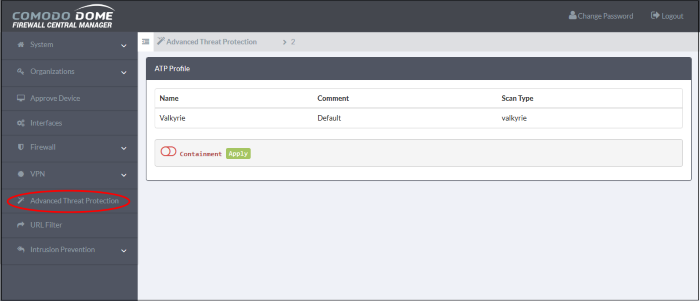
The ATP profile defines types of scan applied to files downloaded by end-users. You can also choose whether or not to apply containment to unknown files.
By default, a profile with Valkyrie analysis is available. You can configure whether or not auto-containment is also enabled on the profile.
To configure an ATP profile for an organization or device
- Click 'Advanced Threat Protection' on the left.
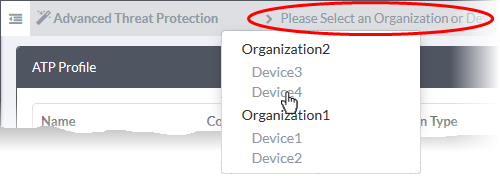
- Select a target organization/device by clicking the link in the gray bar.
- Organization – applies the profile to all devices in the organization
- Device – applies the profile to an individual device
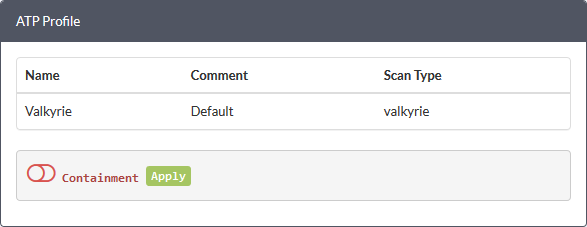
- Use the switch beside 'Containment' to enable or disable the auto-containment of unknown files at the endpoints.
- Click 'Apply'
The profile can be applied for web protection settings when configuring firewall policies. See the explanation of Web Protection in the section Configure Firewall Policy Rules for more details.



