Configure Destination Network Address Translation Rules
- Destination Network Address Translation (DNAT) is used to provide access to internal applications/devices from outside of the network.
- For example, you can provide access to web, ftp, mail and other services that are located inside the network.
- The common use of DNAT is to redirect traffic sent to a public-facing IP to an internal IP / port.
- DNAT rules can be added for a device / organization
- Note - Existing FW DNAT rules will not be imported with the device. We recommend you remove these from the device before importing then configure them again from central manager.
To create and manage DNAT rules:
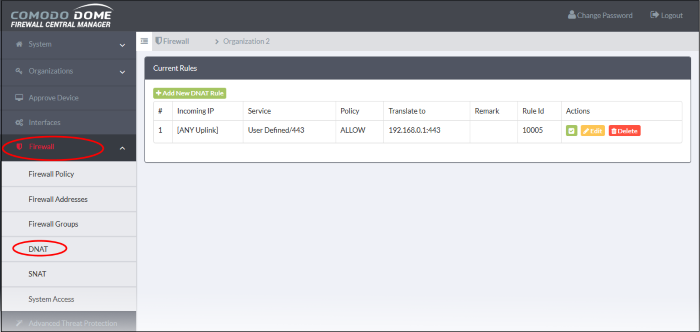
- Click 'Firewall' > 'DNAT' in the left-hand menu.
|
DNAT Table - Column Descriptions |
|
|---|---|
|
Column |
Description |
|
# |
Serial number of the rule |
|
Incoming IP |
The address that receives the traffic. This can be an internal network zone or an external network. |
|
Service |
The protocol and destination port used by the traffic. |
|
Policy |
Whether traffic matching the rule should be allowed, denied or rejected. |
|
Translate to |
The internal IP and port that the traffic should be forwarded to. |
|
Remark |
Comments about the DNAT rule. |
|
Rule ID |
ID number of the rule. Translation is applied by the first rule which meets the conditions of the traffic, regardless of any matching rules that follow. |
|
Actions |
Displays control buttons for managing the rule.
|
To create a DNAT rule
- Click 'Firewall' > 'DNAT' on the left
- Select the organization to which the device belongs or, alternatively, select an individual device.
- Click the 'Add New DNAT Rule' link at the top left.
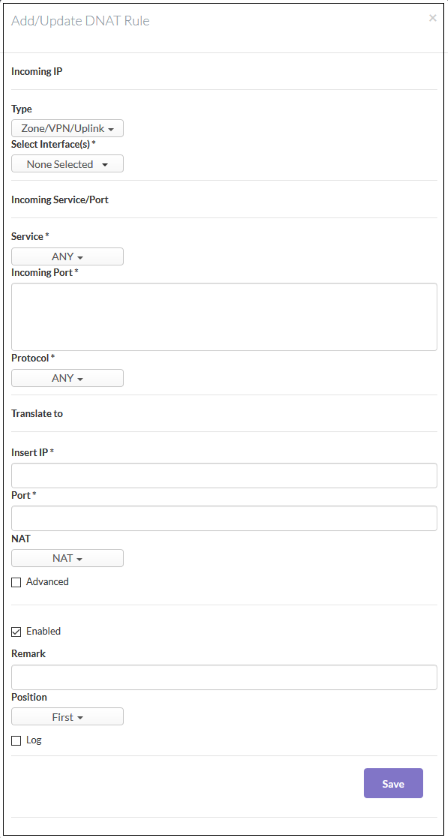
- The 'Add / Update DNAT Rule' dialog will open.
-
Incoming IP - Select the type of incoming source and specify the source in the text box below it.
- Zone/VPN/Uplink – The interfaces configured in the 'Interface Configuration' screen will be available for selection. Select this option if the incoming source is a network zone or an Interface connected to the virtual appliance. Choose the network zone and/or the interface from the options listed in the text box. Press and hold the Ctrl key in the keyboard to choose multiple zones/interfaces.
- Network/IP/Range - Select this option if the rule is to be applied to incoming traffic from a network IP or from a specific IP address or address range. Enter the IP address of the network(s) in CIDR notation or the specific IP address(es) or address range in the text box, as one entry per line.
- SSL VPN User - Select this option if the rule is to be applied to traffic from VPN user(s) added to the network. Choose user(s) from the list of pre-registered users displayed in the textbox. Press and hold the Ctrl key in the keyboard to choose VPN users.
- Incoming Service / Port - Specify the service, protocol and incoming destination port for the rule.
- Service - Select the service for which the rule to be applied from the drop-down.
- Incoming port - Select the destination port for the service. Usually this field will be auto selected based on the service selected.
- Protocol - Select the protocol for the service. Usually this field will be auto selected based on the service selected.
- Translate to – Specify to which IP and port the incoming traffic should be forwarded to. Select whether network address translation should be performed or not.
- Insert IP – Enter the IP to which the traffic should be forwarded to. Note – You have to specify a single IP only.
- Port – Enter the port number / port range to which the incoming traffic should be forwarded to.
- NAT – Select whether network address translation should be done or not. If you select 'Do not NAT', destination address translation will not be performed.
- Advanced Mode - Allow traffic from specific sources and choose whether traffic for a matching DNAT rule should be allowed, dropped or rejected.
- Select the type of incoming source from the drop-down. Press and hold the Ctrl key in the keyboard to choose multiple sources.
- Filter Policy – Select whether network packets from a matching rule should be allowed, dropped or rejected from the drop-down.
- General Settings - Configure the general settings to enable/disable, enter a short description and select a position for the rule in the list.
DNAT rule management activities are logged in System > Tasks. See 'View Management Tasks' for more details.
- Enabled - Leave this checkbox selected if you want the rule to be activated upon creation.
- Remark - Enter a short description for the rule. The description will appear in the remark column of the respective rules interface
- Position - Set the priority for the rule in the list of rules in the respective rules interface. The rules are processed in the order they appear on the list.
- Log - Select this checkbox if you want the packets allowed by the rule are to be logged.
- Click 'Save'. The new DNAT rule will be created and applied to the selected organization or device.




 - Enable or disable the
rule.
- Enable or disable the
rule.