Configure Source Network Address Translation Rules
- Source Network Address Translation (SNAT) is used when a private / internal host needs to connect to an public / external host.
- For example, when an internal host is running a web or mail service and the outgoing packets should be from a public facing IP address.
- SNAT rules can be added for a device / organization
- Note – Existing SNAT rules will not be imported when you add a device. We recommend you remove them from the device before importing then configure them again from central manager.
To create and manage SNAT rules:
- Click 'Firewall' > 'SNAT' in the left-hand menu.
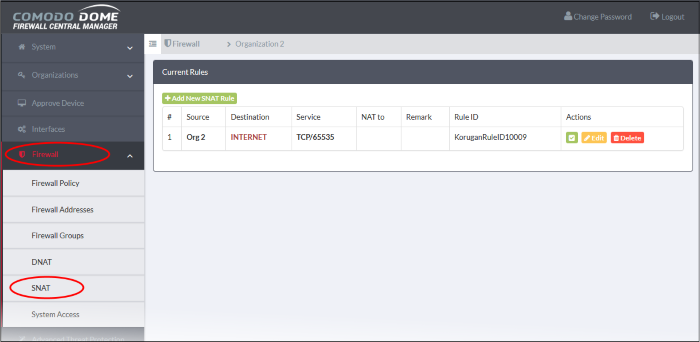
The interface displays all
current SNAT rules and allows you to create new rules.
|
SNAT Table - Column Descriptions |
|
|---|---|
|
Column |
Description |
|
# |
ID number of the rule. Translation is applied based on the first matching rule in the list, regardless of other matching rules that follow. |
|
Source |
The firewall object containing the IP address, IP address range or subnet of the host(s) from which the traffic originates. |
|
Destination |
The interface through which traffic is directed to the external network. |
|
Service |
The protocol and port used by the traffic. |
|
NAT to |
The address to which this traffic should be redirected. |
|
Remark |
A short description of the rule. |
|
Rule ID |
A unique identifier for the SNAT rule. This helps identify the rule in the back-end of the console. |
|
Actions |
Controls for managing the rule.
|
To create an SNAT rule
- Click 'Firewall' > 'SNAT' on the left menu
- Click 'Add New SNAT Rule'. The 'Add/Update Rule' dialog will open:
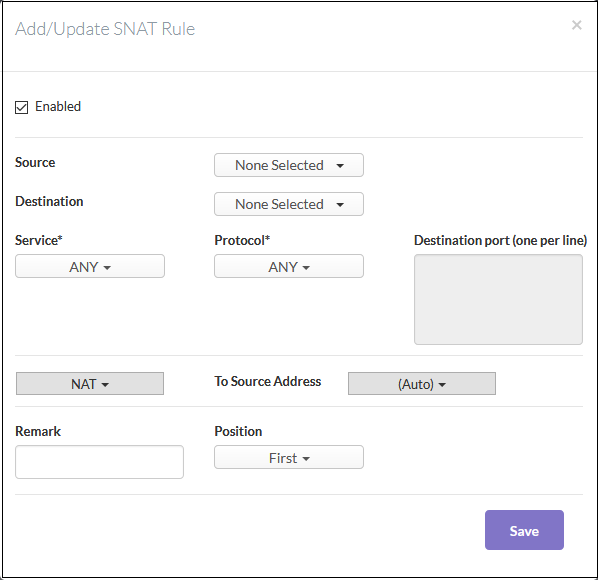
General Settings:
- Enabled - Leave this checkbox selected if you want the rule to be activated after saving.
- Source – Firewall Address object/object group from which traffic originates. Select the required object from the drop-down menu.
- Destination – Specify the interface / firewall address object / object group to which traffic is sent.
See 'Manage Firewall Address Objects' to find out how to create address objects.
- Service / Protocol / Destination Port - Select the type of service hosted by the source, its protocol and ports.
- NAT - Choose whether or not to apply network address translation. The options available are:
- No NAT - Network Address Translation will not be applied
- Map Network- All IPs from the source subnet will be statically mapped to another network of the same size. Specify the subnet to which the IPs are to be mapped in the textbox at the right.
- NAT (to Source Address) - Traffic will be directed to the address you select from the 'To source address' drop-down.
- Remark - Enter a short description of the rule (optional). The description will appear in the 'Remark' column of the respective rule
- Position - Set the priority of the rule among the rules listed in the rules interface. The rules are processed in the order they appear on the list.
- Click 'Save'. The new SNAT rule will be created and applied to the selected organization or device.



