Configure System Access Rules
- System access rules govern the rights that various hosts and zones have to access a firewall device.
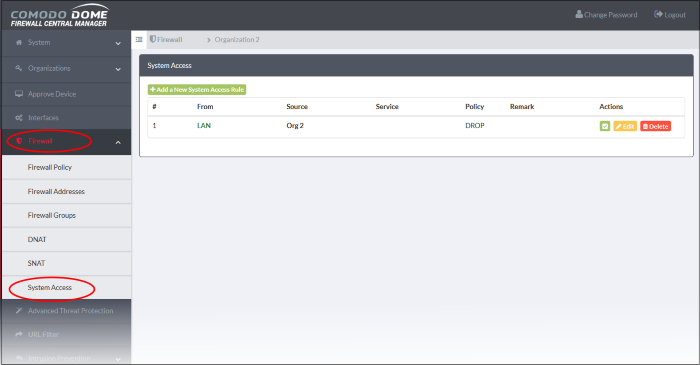
- Click 'Firewall' > 'System Access' on the left to open the rules interface.
- Select a firewall device or organization from the gray bar above the table.
- The system access table shows all existing access rules for the organization or device, and allows you to add new rules.
|
System Access Rules Table - Column Descriptions |
|
|---|---|
|
Column |
Description |
|
# |
ID number of the rule. A packet is allowed or denied based on the first matching rule in the list, regardless of other matching rules that follow. |
|
From |
The interface over which traffic is received. E.g. 'LAN', 'Internet', 'WiFi'. |
|
Source |
The firewall address object/object group from which traffic originates. |
|
Service |
The port and protocol used by traffic which will be affected by this rule. |
|
Policy |
Action taken on traffic affected by this rule. |
|
Remark |
A short description of the rule. |
|
Actions |
Controls for managing the rule.
|
To create a new rule
- Click 'Firewall' > 'System Access' on the left
- Select a firewall device or organization from the gray bar above the table
- Click the 'Add a New System Access Rule' link button. The rule configuration screen will open:
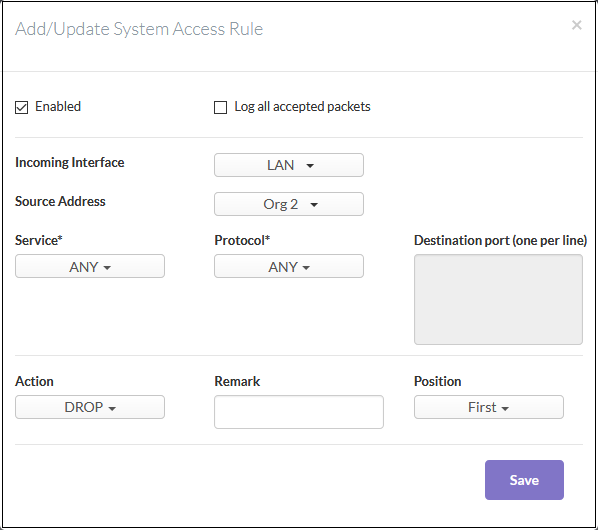
- Enabled - Leave selected if you want the rule to be activated immediately after saving. You can enable or disable the rule later in the rules list if required.
- Log all accepted packets - Enable to create a record of all data packets accepted by the rule.
- Incoming Interface - Select the interface from which traffic is received
- Source Address - The firewall address object/object group from which traffic originates.
- Service/Protocol/Port
- Service - Choose the service over which the traffic is sent. Selecting a service will auto-populate the 'Protocol' and 'Destination Port' fields. You can, of course, edit the port fields if required.
- Protocol - Choose the protocol used by the service. Selecting a protocol will change the 'Service' to 'User defined'. Assuming a match on incoming interface and source address, the rule will affect all traffic using the chosen protocol regardless of service type.
- Destination port - Specify the destination port(s) of the service one by one.
- Action - Specify whether packets matching the rule should be allowed or denied. The options available are:
- Accept - The data packets will be allowed without filtering
- Drop - The packets will be denied
- Reject - The packets will be rejected, and error packets will be sent in response
- Remark - Enter a short description of the rule (optional)
- Position - Set the priority for the rule in the list of rules in the respective rules interface. The rules in the IP tables are processed in the order that appears on the list.
- Click 'Save'. The
new system access rule will be created and applied to the selected
organization or device.




 - Enable or disable the
rule.
- Enable or disable the
rule. - Edit rule parameters.
The 'Edit' interface is similar to the 'Add/Update System Access
Rule' interface.
- Edit rule parameters.
The 'Edit' interface is similar to the 'Add/Update System Access
Rule' interface.  - Removes the rule.
- Removes the rule.