Boot Log and Handle Loaded Modules
- The Boot logger feature records all modules loaded when your system boots.
- These include items like drivers, system files, DLLs, executables and so on.
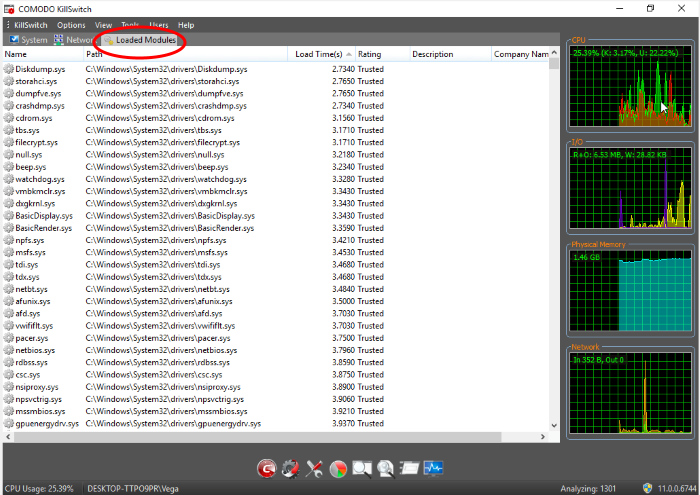
- KillSwitch displays these modules in a new 'Loaded Modules' tab after your system has rebooted.
- This functionality lets you check whether unsafe (or even just unwanted) modules are being loaded. In extreme cases, it will allow you to detect and delete malicious boot items installed by spyware, key loggers, rootkits or other malware.
To configure for Boot Logging
-
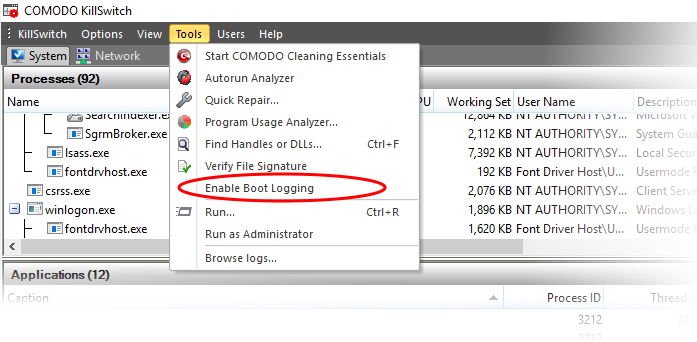
Click 'Tools' > 'Enable Boot Logging'
-
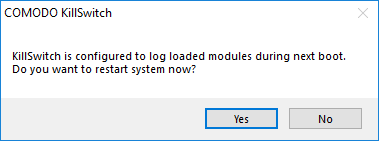
Save all your work and click 'Yes'. Your system will re-start. Upon restart, KillSwitch will be started automatically and show all the loaded modules loaded to your system.
|
Loaded Modules window - Descriptions of Columns |
|
|---|---|
|
Column |
Description |
|
Name |
The title of the module. Click the column header to sort the entries in alphabetical order of the module names. |
|
Path |
The storage location of the module. |
|
Load Time (in seconds) |
The time taken for loading the module. |
|
Rating |
The result of scanning performed by KillSwitch on the module. Modules that are rated as false positive, unsafe or unknown are highlighted for easy identification. |
|
Description |
A brief information of the module. |
|
Company Name |
The vendor of the module. |
|
Tip: Click any of the column header to sort the list in alphabetical/numerical order of the entries in it. |
- Double-click on a module to open its 'Properties' dialog
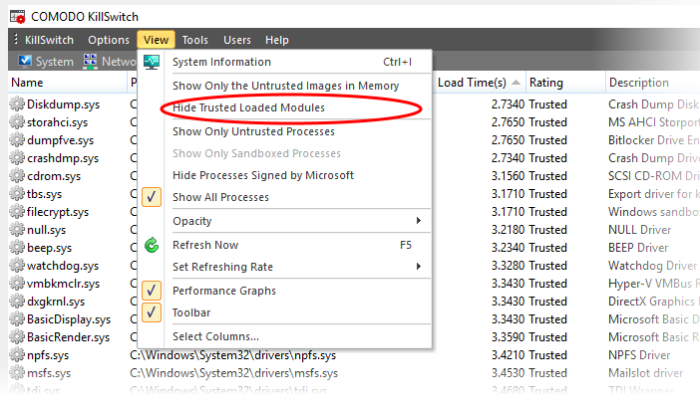
Filter the Loaded Modules List
Click 'View' > 'Hide Trusted Loaded Modules' to show only modules identified as 'untrusted' or 'unknown':
Handle Loaded Modules
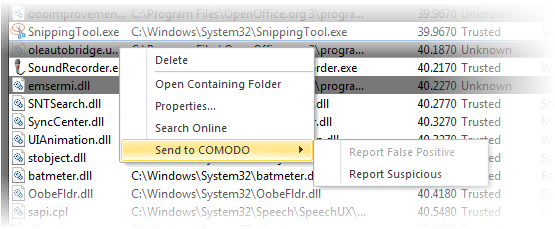
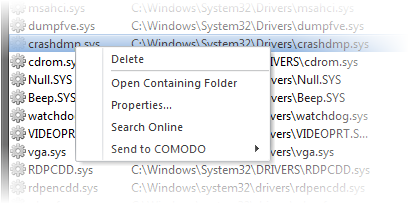
You can view properties of or remove loaded module by right clicking on it and selecting the required option from the context sensitive menu.
-
Delete - Removes the Module from your system. This ensures that the module is not loaded to your system from the next boot onwards.
- Open Containing Folder - Еhe location having the module in windows explorer.
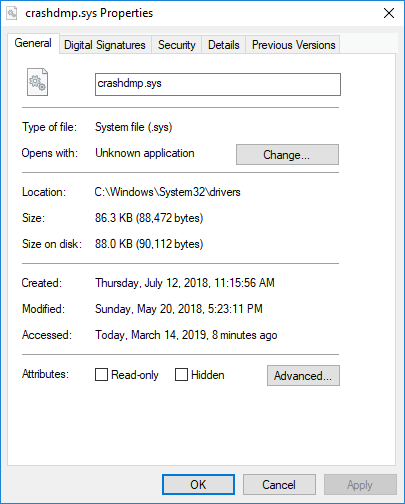
- Properties... - The attributes dialog of the selected Module.
- Search Online - Shows the default web browser of your system with the search engine specified and searches for information on the module
- Send to COMODO - Submit the module to Comodo for analysis:
- Report Suspicious - Submit items you believe are malicious but have been deemed safe by KillSwitch
- Report 'False Positive' - Submit items you think KillSwitch has falsey identified as suspicious
Submitted files will be analyzed by experts and added to the global white list or black list accordingly.