- Introduction To Comodo Internet Security
- General Tasks – Introduction
- Firewall Tasks – Introduction
- Sandbox Tasks – Introduction
- Advanced Tasks – Introduction
- Advanced Settings
- Comodo GeekBuddy
- TrustConnect Overview
- Comodo Dragon
- Comodo BackUp
- Appendix 1 CIS How To... Tutorials
- Enabling / Disabling Security Components Easily
- Setting Up The Firewall For Maximum Security And Usability
- Blocking Internet Access While Allowing Local Area Network (LAN) Access
- Setting Up The HIPS For Maximum Security And Usability
- Setting Up The Behavior Blocker For Maximum Security And Usability
- Password Protect Your CIS Settings
- Reset Forgotten Password (Advanced)
- Running An Instant Antivirus Scan On Selected Items
- Creating An Antivirus Scanning Schedule
- Running Untrusted Programs Inside Sandbox
- Running Browsers Inside Sandbox
- Running Untrusted Programs Inside Virtual Kiosk
- Running Browsers Inside The Virtual Kiosk
- Restoring Incorrectly Quarantined Item(s)
- Submitting Quarantined Items To Comodo For Analysis
- Enabling File Sharing Applications Like BitTorrent And Emule
- Blocking Any Downloads Of A Specific File Type
- Disabling Behavior Blocker And Auto-Sandboxing On A Per-application Basis
- Switching Between Complete CIS Suite And Individual Components (just AV Or FW)
- Switch Off Automatic Antivirus And Software Updates
- Suppressing CIS Alerts Temporarily While Playing Games
- Renewing Your License
- Appendix 2 - Comodo Secure DNS Service
- Appendix 3 - Glossary Of Terms
- About Comodo Security Solutions
Antivirus Settings
The Antivirus Settings category has sub-sections that allow you to configure Real Time Scans (a.k.a 'On-Access' scanning), Custom Scans, and Exclusions (a list of the files you consider safe).
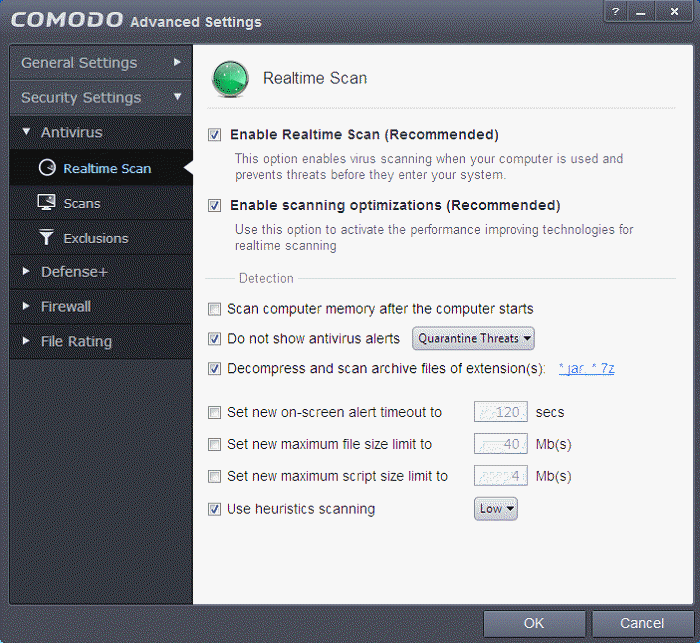
Click the following links to jump to each section:
- Real Time Scan - To set the parameters for on-access scanning;
- Custom Scan - To create scan profiles and run custom scans, schedule custom scans and set the parameters for custom scans;
- Exclusions - To see the list of ignored threats and to set the parameters for Exclusions.



