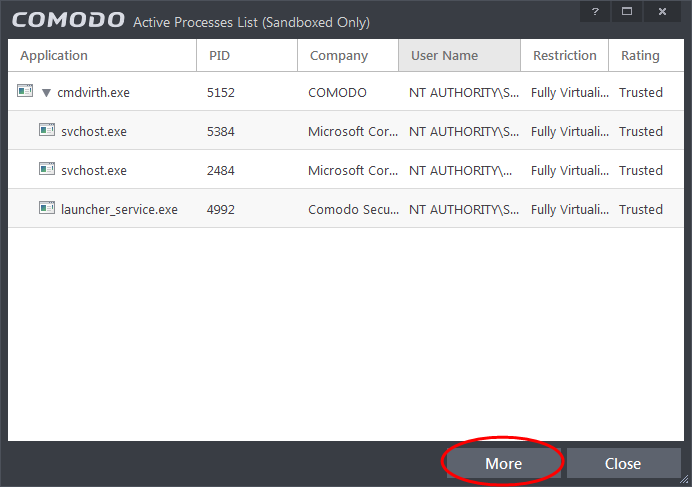
View Sandboxed Processes List
The Active Process List (Sandboxed Only) interface displays all currently active processes initiated by applications that are currently running in the sandbox environment. By tracing an application's parent process, CIS can detect whether a non-trusted application is attempting to spawn an already trusted application and thus deny access rights for that trusted application. This system provides the very highest protection against Trojans, malware and rootkits that try to use trusted software to launch an attack. By default, the list displays the processes of sandboxed applications only, but can be made to display all the processes from the right-click options.
The processes of sandboxed applications include:
-
Auto-Sandbox - Applications that are run inside the sandbox as per the rules defined for them or by default sandbox rules. Refer to the section 'Configuring Rules for Auto-Sandbox for more details on defining auto-sandbox rules.
-
Run Virtual - Applications that are selected and run in Sandbox. Refer to 'Run an Application in the Sandbox' for more details.
-
Applications that are run inside the sandbox using the context sensitive menu - Click here for more details.
-
Running browsers inside the sandbox from the Widget - Click here for more details.
-
Drag-and-drop applications on to CIS Home Screen - Click here for more details.
-
Programs that are added manually - Refer to the section 'Configuring Rules for Auto-Sandbox' for more details.
To view Active Process list
-
Click the first box in the third row in the CIS Widget.
| Note: The Status Pane is not displayed by default in the widget. To enable the Status Pane, right click on the CIS tray icon and select 'Show Status Pane' from the options. |
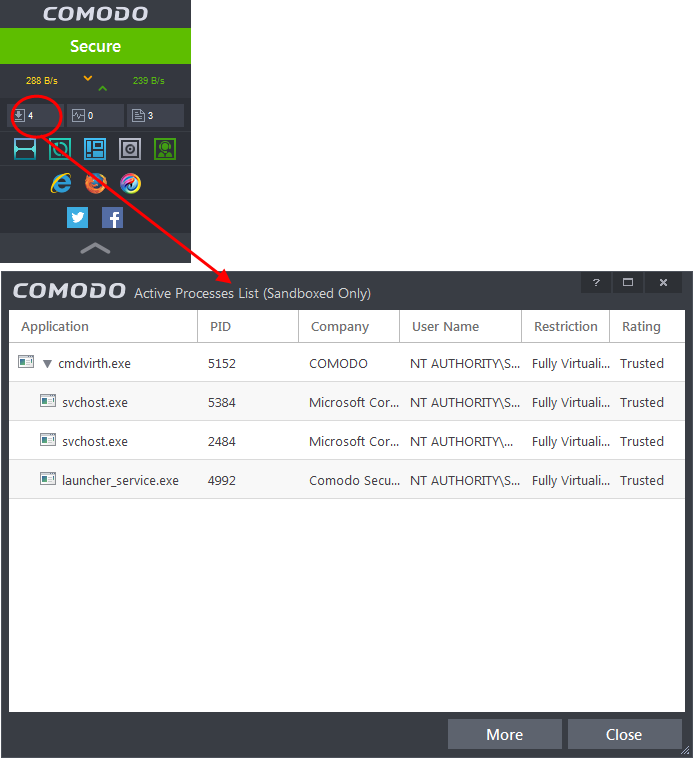
- Alternatively, the screen can be accessed by clicking the number beside 'Sandboxed Apps' in the Advanced View of the Home screen in the Defense+ and Sandbox pane.
Column Descriptions
-
Application – Displays the names of applications that are currently running.
-
PID – Process Identification Number.
-
Company – Displays the name of the software developer.
-
User Name – The name of the user that started the process.
-
Restriction – Displays the level of sandbox setting selected for the program.
-
Rating – Displays the rating of the application whether trusted or unknown.
Right-click on any process to:
-
Show full path: Displays the location of the the executable in addition to it's name.
-
Show Sandboxed Only: Displays the details of the sandboxed programs only. Disable this option to view all the current active process list.
-
Add to Trusted Files: The selected unknown program is added to Trusted Files list.
-
Online Lookup: The selected program is compared with the Comodo database of programs and results declared whether it is safe or not.
-
Submit: The selected application will be sent to Comodo for analysis.
- Show Activities: Opens the Process Activities List dialog. The Process Activities dialog will display the list activities of the processes run by the application. The 'Show Activities' option is available only if Viruscope is enabled under Advanced Settings > Defense+ > Viruscope.
Clicking the 'More' button at the bottom of the screen will open the Comodo KillSwitch application – an advanced system monitoring tool that allows users to quickly identify, monitor and terminate any unsafe processes that are running on your system.