Create, Schedule and Run a Custom Scan
By creating a custom scan profile, you can choose exactly which files and folders are scanned, when they are scanned and how they are scanned. Once created and saved, your custom scan profile will appear in the scans interface and can be run, on demand, at any time.
-
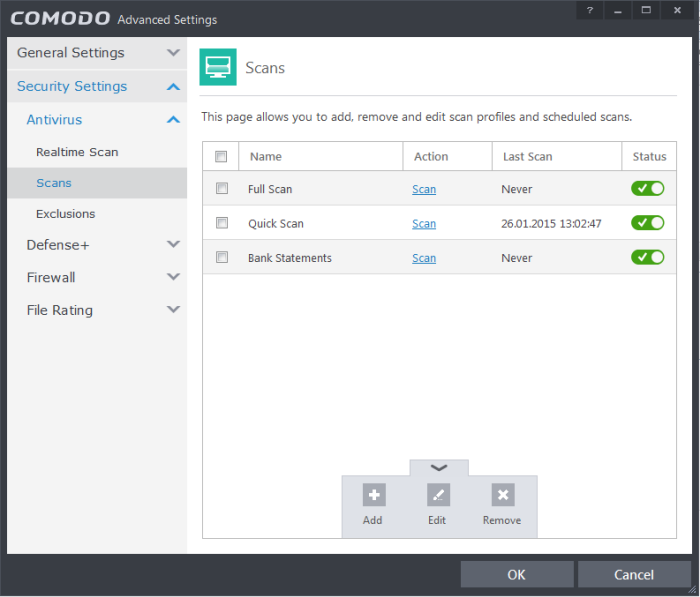
Click the 'Tasks' arrow on the home screen to open the main Tasks menu
-
In 'General Tasks', click 'Scan'
-
Select 'Custom Scan' then 'More Scan Options'
-
The 'Advanced Settings' interface will be displayed with 'Scans' panel opened
- Click the handle at the bottom of the interface then select 'Add':
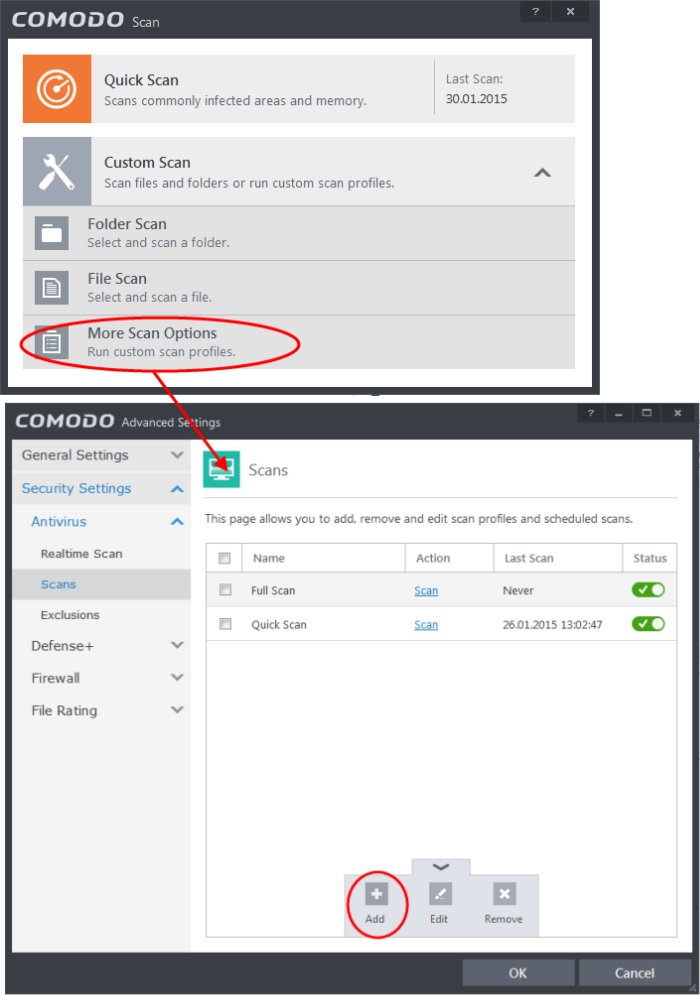
The scan profile interface will be displayed.
-
Type a name for the profile in the 'Scan Name' text box
-
Click the handle at the bottom of the interface to select items to be included in the profile:
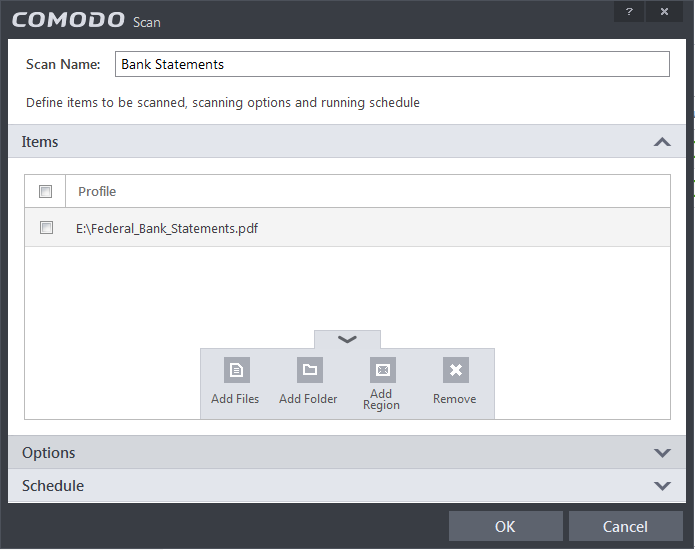
- Add File - Allows you to add individual files to the profile
- Add Folder - Allows you to select entire folders to be included in the profile
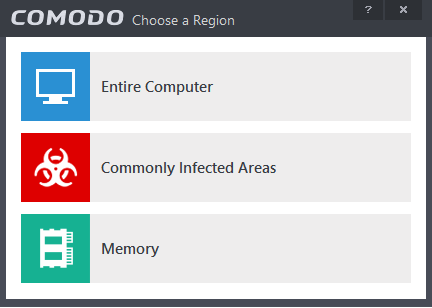
- Add Region - Allows you to add pre-defined regions to the profile (choice of 'Full Computer', 'Commonly Infected Areas' and 'System Memory')
-
Repeat the process to add more items to the profile. Click 'OK' to confirm your choice
-
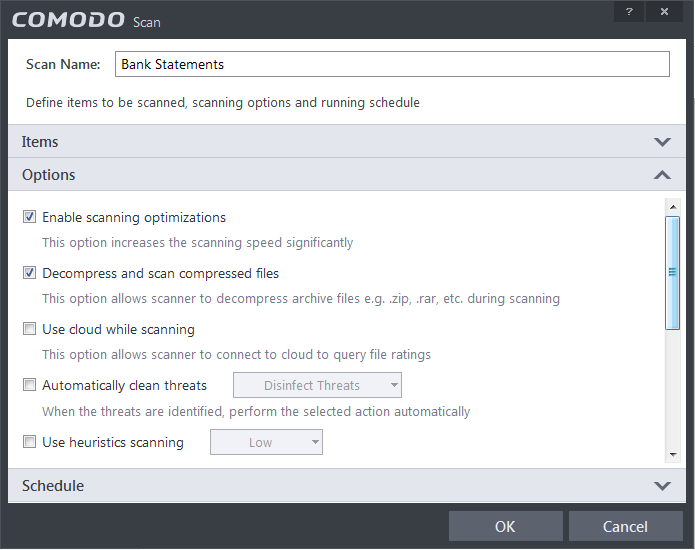
Next, click 'Options' to further customize the scan:
-
Options:
-
Enable scanning optimizations – On selecting this option, the antivirus will employ various optimization techniques like running the scan in the background in order to speed-up the scanning process (Default = Enabled) .
-
Decompress and scan compressed files - When this check box is selected, the Antivirus scans archive files such as .ZIP and .RAR files. Supported formats include RAR, WinRAR, ZIP, WinZIP ARJ, WinARJ and CAB archives (Default = Enabled) .
-
Use cloud while scanning - Selecting this option enables the Antivirus to detect the very latest viruses more accurately because the local scan is augmented with a real-time look-up of Comodo's online signature database. With Cloud Scanning enabled your system is capable of detecting zero-day malware even if your local anitvirus database is out-dated. (Default = Disabled).
-
Automatically clean threats – Enables you to select the action to be taken against the detected threats and infected files automatically from disinfecting Threats and moving the threats to quarantine.
-
Use heuristics scanning – Enables you to select whether or not Heuristic techniques should be applied on scans in this profile. You are also given the opportunity to define the heuristics scan level. (Default = Enabled).
Background Info: Comodo Internet Security employs various heuristic techniques to identify previously unknown viruses and Trojans. 'Heuristics' describes the method of analyzing the code of a file to ascertain whether it contains code patterns similar to those in known viruses. If it is found to do so then the application deletes the file or recommends it for quarantine. Heuristics is about detecting 'virus-like' traits or attributes rather than looking for a precise virus signature that matches a signature on the virus blacklist.
This allows CIS to 'predict' the existence of new viruses - even if it is not contained in the current virus database.
-
Low- Lowest' sensitivity to detecting unknown threats but will also generate the fewest false positives. This setting combines an extremely high level of security and protection with a low rate of false positives. Comodo recommends this setting for most users. (Default)
-
Medium - Detects unknown threats with greater sensitivity than the 'Low' setting but with a corresponding rise in the possibility of false positives.
-
High - Highest sensitivity to detecting unknown threats but this also raises the possibility of more false positives too.
-
Limit maximum file size to – Select this option if you want to impose size restrictions on files being scanned. Files of size larger than that specified here, are not scanned, if this option is selected (Default = 40 MB).
-
Run this scan with – Enables you to set the priority of the scan profile. You can select the priority from the drop-down.(Default = Disabled).
-
Update virus database before running - Instructs Comodo Internet Security to check for latest virus signature database updates from Comodo website and download the updates automatically before starting the scanning (Default = Enabled).
-
Detect potentially unwanted applications - When this check box is selected, Antivirus scans also scans for applications that (i) a user may or may not be aware is installed on their computer and (ii) may functionality and objectives that are not clear to the user. Example PUA's include adware and browser toolbars. PUA's are often installed as an additional extra when the user is installing an unrelated piece of software. Unlike malware, many PUA's are 'legitimate' pieces of software with their own EULA agreements. However, the 'true' functionality of the software might not have been made clear to the end-user at the time of installation. For example, a browser toolbar may also contain code that tracks a user's activity on the Internet (Default = Enabled).
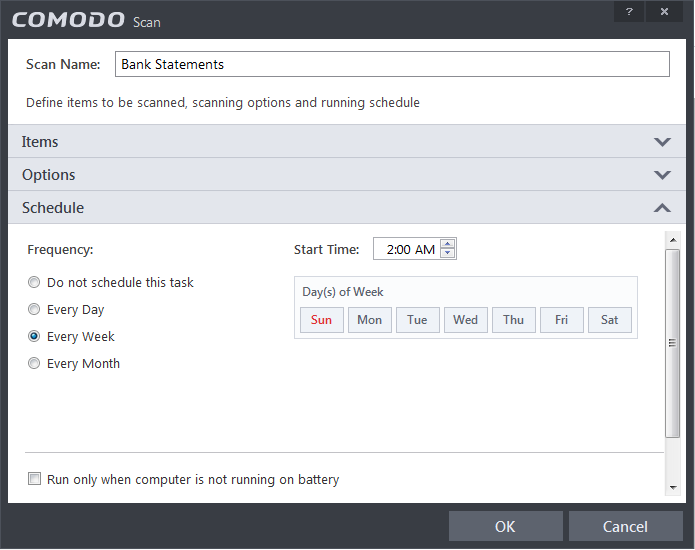
- If you want the scan to run at specific times, click 'Schedule':
-
Do not schedule this task – The scan profile will be created but will not be run automatically. The profile will be available for manual on-demand scanning
-
Every Day - The Antivurus starts scanning the areas defined in the scan profile every day at the time specified in the Start Time field
-
Every Week - The Antivurus starts scans the areas defined in the scan profile on the day(s) of the week specified in 'Days of the Week' field and the time specified in the 'Start Time' field. You can select the days of the week by directly clicking on them
-
Every Month - The Antivurus starts scans the areas defined in the scan profile on the day(s) of the month specified in 'Days of the month' field and the time specified in the 'Start Time' field. You can select the days of the month by directly clicking on them
-
Run only when computer is not running on battery - This option is useful when you are using a laptop or any other battery driven portable computer. Selecting this option runs the scan only if the computer runs with the adopter connected to mains supply and not on battery
-
Run only when computer id IDLE - Select this option if you do not want to disturbed when involved in computer related activities. The scheduled can will run only if the computer is in idle state
-
Turn off computer if no threats are found at the end of the scan - Selecting this option turns your computer off, if no threats are found during the scan. This is useful when you are scheduling the scans to run at nights.
-
Click OK to save the profile.
| Note: The schedule scan will run only if it is enabled. Click the button under the Active column beside the respective profile row to toggle between on and off status. |
The profile will be available will be available for deployment in future.
-
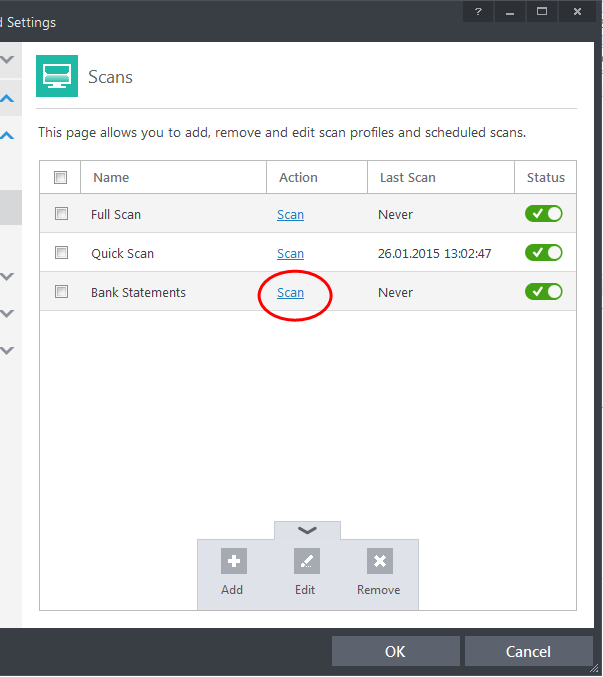
Click 'Scan' from the 'General Tasks' interface and Click 'Custom Scan' from the 'Scan' interface
-
Click 'More Scan Options' from the 'Custom Scan' pane
The 'Advanced Settings' interface will be displayed with 'Scans' panel opened.
-
Click 'Scan' beside the required scan profile.
-
The scan will be started
-
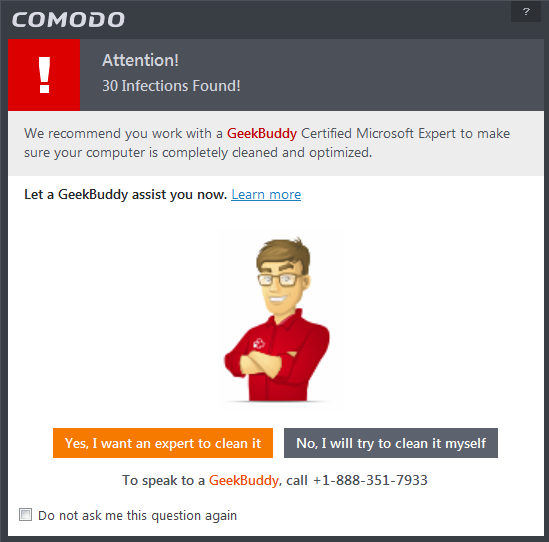
On completion of scanning, if any threats are found, an alert screen will be displayed. The alert will display the number of threats/infections discovered by the scanning and provide you the options for cleaning
-
If you wish to have a skilled professional from Comodo to access your system and perform an efficient disinfection, click 'Yes, I want an expert to clean it'. If you are a first-time user, you will be taken to Comodo GeekBuddy webpage to sign-up for a GeekBuddy subscription. If you have already signed-up for GeekBuddy services, the support chat session will start and a skilled technician will offer to clean your system.
For more details on GeekBuddy, refer to the section Comodo GeekBuddy.
- If you wish to clean the infections yourself, select 'No, I will try to clean it myself'. The scan results screen will be displayed.
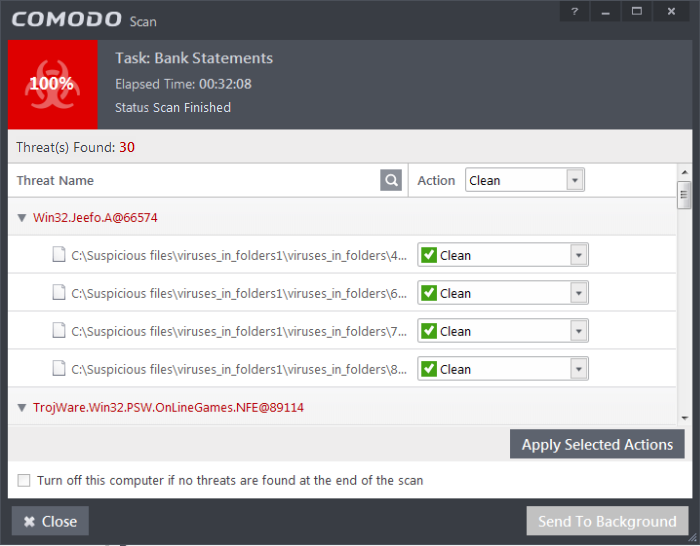
The scan results window displays the number of objects scanned and the number of threats (Viruses, Rootkits, Malware and so on). You can choose to clean, move to quarantine or ignore the threat based in your assessment. Refer to Processing the infected files for more details.