Application Rules
Overview of Rules and Rulesets
Whenever an application makes a request for Internet or network access, Comodo Firewall allows or denies this request based upon the Firewall Ruleset that has been specified for that application. Firewall Rulesets are, in turn, made up from one or more individual firewall rules. Each individual firewall rule contains instructions that determine whether the application should be allowed or blocked; which protocols it is allowed to use; which ports it is allowed to use and so forth.
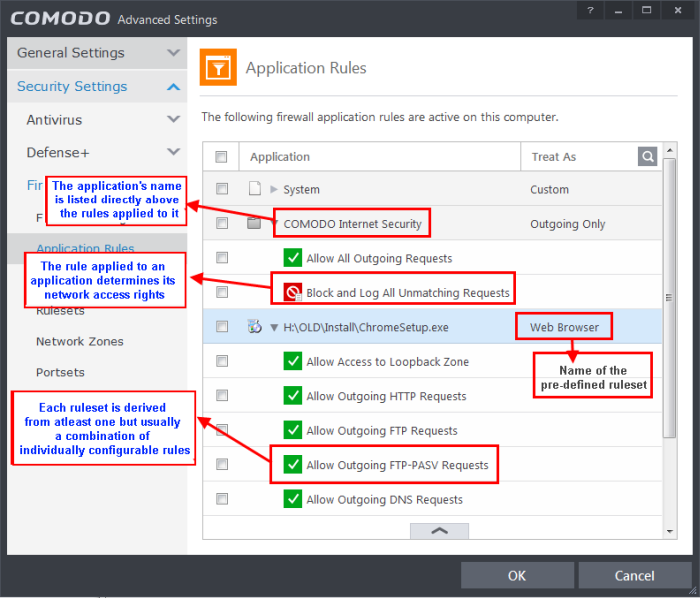
The first column, Application, displays a list of the applications on your system for which a Firewall ruleset has been deployed. If the application belongs to a file group, then all member applications assume the ruleset of the file group. The second column, Treat as, column displays the name of the Firewall ruleset assigned to the application or group of applications in column one.
You can use the search option to find a specific name in the list.
To use the search option, click the search icon ![]() at the far right in the column header.
at the far right in the column header.
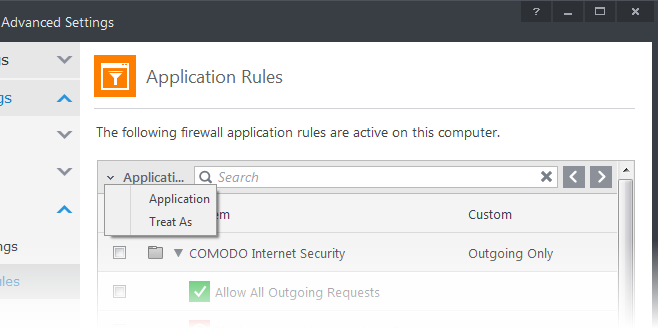
- Click the chevron on the left side of the column header and select the search criteria from the drop-down.
- Enter partly or fully the name of the item as per the selected criteria in the search field.
- Click the right or left arrow at the far right of the column header to begin the search.
- Click the
 icon in the search field to close the search option.
icon in the search field to close the search option.
General Navigation:
Clicking the handle at the bottom center of the interface opens a rule control panel:
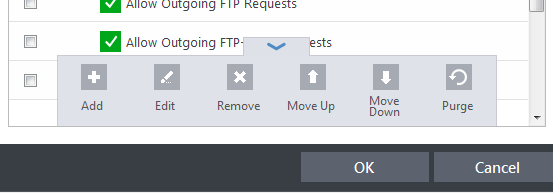
- Add - Allows the user to Add a new Application to the list then create it's ruleset. See the sections 'Creating or Modifying Firewall Ruleset' and 'Adding and Editing a Firewall Rule'.
- Edit - Allows the user to modify the Firewall rule or ruleset of the selected application. See the sections 'Creating or Modifying Firewall Ruleset' and 'Adding and Editing a Firewall Rule'.
- Remove - Deletes the selected ruleset.
- Purge - Runs a system check to verify that all the applications for which rulesets are listed are actually installed on the host machine at the path specified. If not, the rule is removed, or 'purged', from the list.
- Move and Move Down - The traffic is filtered by referring to the rules in order from the top. The Move Up and Move Down buttons enable you to change the priority of a selected rule.
If you wish to modify the firewall ruleset for an application:
- Double click on the application name to begin 'Creating or Modifying Firewall Ruleset'
- Select the application name click the handle at the bottom right and choose 'Edit' from the options to begin 'Creating or Modifying Firewall Ruleset'
If you wish to modify an individual rule within the policy:
- Double click on the specific rule to begin 'Adding and Editing a Firewall Rule'
- Select the specific rule and click the handle at the bottom center and choose 'Edit' from the options to begin 'Adding and Editing a Firewall Rule'
Although each ruleset can be defined from the ground up by individually configuring its constituent rules, this practice would be time consuming if it had to be performed for every single program on your system. For this reason, Comodo Firewall contains a selection of predefined rulesets according to broad application category. For example, you may choose to apply the ruleset 'Web Browser' to the applications like 'Internet Explorer', 'Firefox' and 'Opera'. Each predefined ruleset has been specifically designed by Comodo Firewall to optimize the security level of a certain type of application. Users can, of course, modify these predefined rulesets to suit their environment and requirements. For more details, see Predefined Rule Sets.
- See Application Rule interface for an introduction to the rule setting interface
- See Creating and Modifying Firewall Rulesets to learn how to create and edit Firewall rulesets
- See Understanding Firewall Rules for an overview of the meaning, construction and importance of individual rules
- See Adding and Editing a Firewall Rule for an explanation of individual rule configuration
Firewall rules can be added/modified/removed and re-ordered through the Application Rule interface. Any rules created using Adding and Editing a Firewall Rule is displayed in this list.
The Application Rule interface is displayed when you click 'Add' or 'Edit' from the options in 'Application Rules' interface
Comodo Firewall applies rules on a per packet basis and applies the first rule that matches that packet type to be filtered (see Understanding Firewall Rules for more information). If there are a number of rules in the list relating to a packet type then one nearer the top of the list is applied.
Users can also re-prioritize rulesets by clicking the handle at the bottom center and select 'Move Up' or 'Move Down' from the options. To begin creating Firewall Rule Sets, first read 'Overview of Rules and Rulesets' then 'Creating and Modifying Firewall Rulesets'.
You can use the search option to find a specific rule in the list.
To use the search option, click the search icon ![]() at the far right in the column header.
at the far right in the column header.
- Click the chevron on the left side of the column header and select the search criteria from the drop-down.
- Enter partly or fully the name of the item as per the selected criteria in the search field.
- Click the right or left arrow at the far right of the column header to begin the search.
- Click the
 icon in the search field to close the search option.
icon in the search field to close the search option.
Creating and Modifying Firewall Rulesets
To begin defining an application's Firewall ruleset, you need take two basic steps.
Step 1 - Select the application that you wish the ruleset is to be applied
If you wish to define a ruleset for a new application ( i.e. one that is not already listed) then click the handle from the Application Rules interface and select 'Add' from the options. This brings up the 'Application Rule' interface shown below:
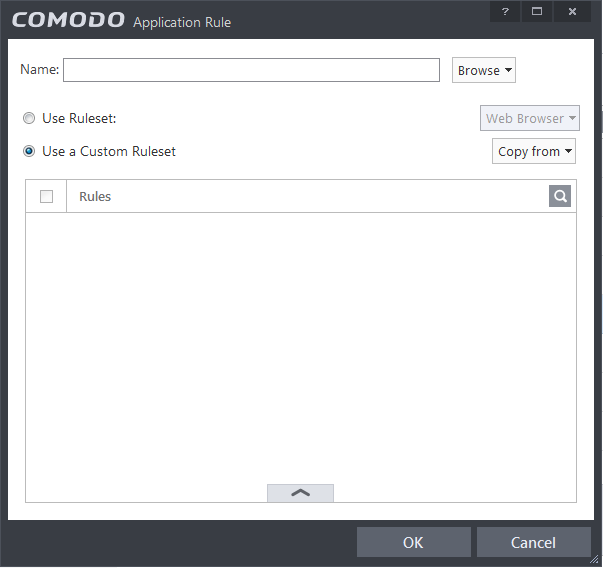
Because this is a new application, the 'Application Path' field is blank. (If you are modifying an existing policy, then this interface shows the individual rules for that application's policy).
-
Click 'Browse' button.
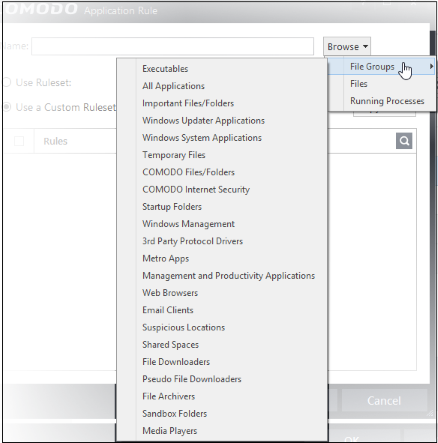
You now have 3 methods available to choose the application for which you wish to create a ruleset - File Groups; Files and Running Processes
-
File Groups - choosing this option allows you to create firewall ruleset for a category of pre-set files or folders. For example, selecting 'Executables' would enable you to create a firewall policy for any file that attempts to connect to the Internet with the extensions .exe .dll .sys .ocx .bat .pif .scr .cpl . Other such categories available include 'Windows System Applications' , 'Windows Updater Applications' , 'Start Up Folders' etc - each of which provide a fast and convenient way to apply a generic policy to important files and folders. To view the file types and folders that are affected by choosing one of these options, you need to visit the 'Protected Files' of Comodo Internet Security by navigating to: Advanced Settings > Security Settings > Defense+ > HIPS > File Protection> Protected Files and clicking the handle from the bottom center > Groups. For more details on file groups, refer to the section File Groups.
-
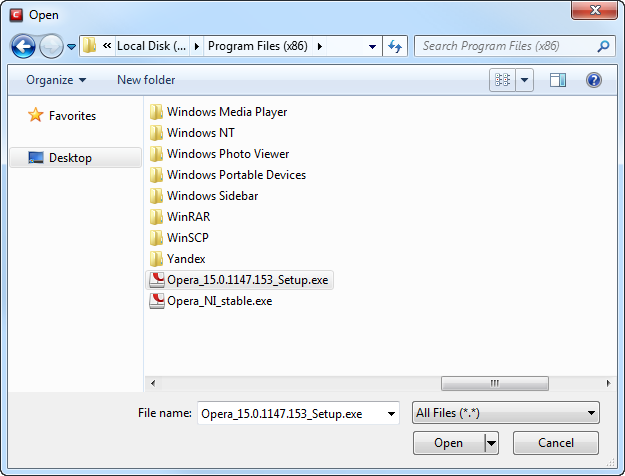
Files - this option is the easiest for most users and simply allows you to browse to the location of the application for which you want to deploy the firewall ruleset. In the example below, we have decided to create a firewall ruleset for the Opera web browser.
-
Running Processes - as the name suggests, this option allows you to create and deploy firewall ruleset for any process that is currently running on your PC.
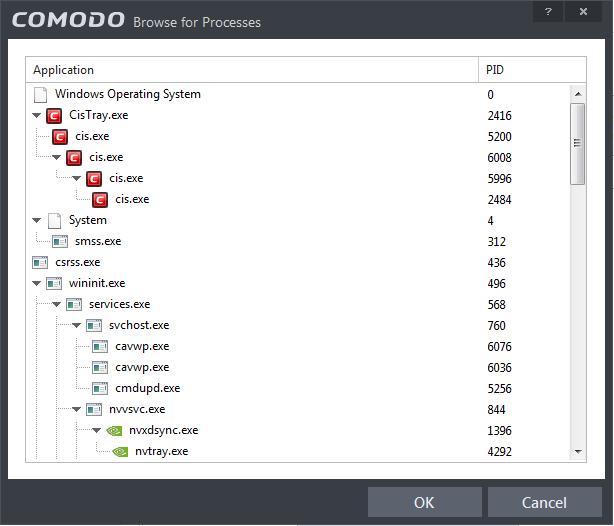
You can choose an individual process or the parent process of a set of running processes. Click 'OK' to confirm your choice.
Having selected the individual application, running process or file group, the next stage is to Configure the rules for this application's policy.
Step 2 - Configure the rules for this application's ruleset
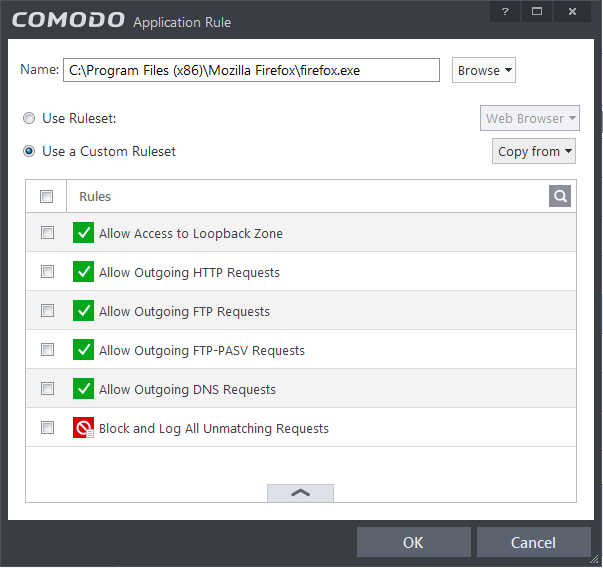
There are two broad options available for creating a policy that applies to an application - Use a Predefined Ruleset or Use a Custom Ruleset.
-
Use a Predefined Ruleset - Selecting the 'Use Ruleset' option allows you to quickly apply an existing ruleset to the target application. Choose the ruleset you wish to use from the drop-down menu. In the example below, we have chosen 'Web Browser' because we are creating a ruleset for the 'Opera' browser. The name of the predefined ruleset you choose is displayed in the Treat As column for that application in the interface (Default = Disabled).
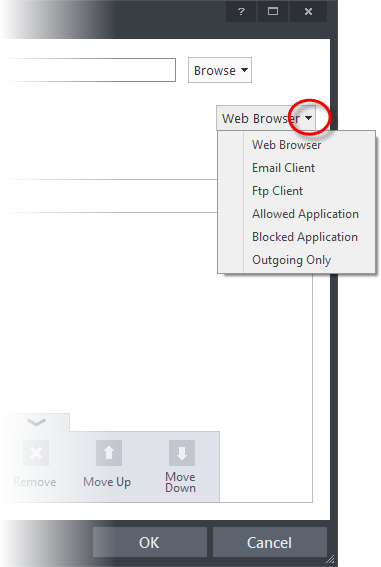
| Note: Predefined Rulesets, once chosen, cannot be modified directly from this interface - they can only be modified and defined using the Predefined Rulesets interface. If you require the ability to add or modify rules for an application then you are effectively creating a new, custom ruleset and should choose the more flexible Use Custom Ruleset option instead. |
- Use a Custom Ruleset - designed for more experienced users, the Custom Ruleset option enables full control over the configuration of firewall ruleset and the parameters of each rule within that ruleset (Default = Enabled).
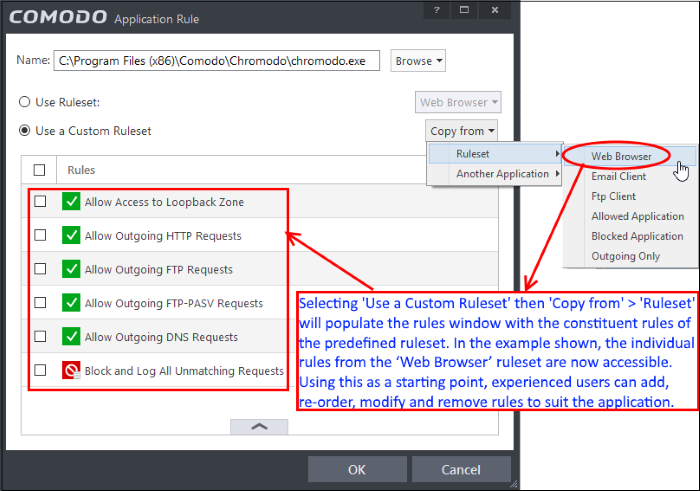
You can create an entirely new ruleset or use a predefined ruleset as a starting point by:
- Clicking the handle at the bottom and choosing 'Add' to add individual firewall rules. See 'Adding and Editing a Firewall Rule' for an overview of the process.
- Use the 'Copy From' button to populate the list with the Firewall rules of a Predefined Firewall Rule.
- Use the 'Copy From' button to populate the list with the Firewall rules of another application's ruleset.
|
General Tips:
|
At their core, firewall rule can be thought of as a simple IF THEN trigger - a set of conditions(or attributes) pertaining to a packet of data from a particular application, and an action that is enforced if those conditions are met.
As a packet filtering firewall, Comodo Firewall analyzes the attributes of every single packet of data that attempts to enter or leave your computer. Attributes of a packet include the application that is sending or receiving the packet, the protocol it is using, the direction in which it is traveling, the source and destination IP addresses and the ports it is attempting to traverse. The firewall then tries to find a Firewall rule that matches all the conditional attributes of this packet in order to determine whether or not it should be allowed to proceed. If there is no corresponding Firewall control rule, then the connection is automatically blocked until a rule is created.
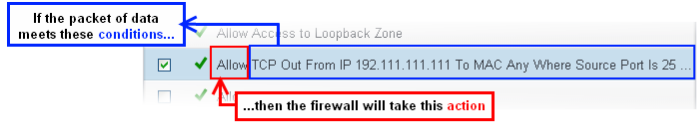
The actual conditions (attributes) you see* on a particular Firewall Rule are determined by the protocol chosen in Adding and Editing a Firewall Rule
If you chose 'TCP' , 'UDP' or 'TCP and 'UDP', then the rule has the form: Action|Protocol|Direction|Source Address | Destination Address| Source Port|Destination Port
If you chose 'ICMP', then the rule has the form: Action|Protocol|Direction |Source Address |Destination Address| ICMP Details
If you chose 'IP', then the rule has the form: Action|Protocol|Direction | Source Address|Destination Address|IP Details
- Action: The action the firewall takes when the conditions of the rule are met. The rule shows 'Allow', 'Block' or 'Ask'.**
- Protocol: States the protocol that the target application must be attempting to use when sending or receiving packets of data. The rule shows 'TCP', 'UDP', 'TCP or UDP', 'ICMP' or 'IP'
- Direction: States the direction of traffic that the data packet must be attempting to negotiate. The rule shows 'In', 'Out' or 'In/Out'
- Source Address: States the source address of the connection attempt. The rule shows 'From' followed by one of the following: IP , IP range, IP Mask , Network Zone, Host Name or Mac Address
- Destination Address: States the address of the connection attempt. The rule shows 'To' followed by one of the following: IP, IP range, IP Mask, Network Zone, Host Name or Mac Address
- Source Port: States the port(s) that the application must be attempting to send packets of data through. Shows 'Where Source Port Is' followed by one of the following: 'Any', 'Port #', 'Port Range' or 'Port Set'
- Destination Port: States the port(s) on the remote entity that the application must be attempting to send to. Shows 'Where Source Port Is' followed by one of the following: 'Any', 'Port #', 'Port Range' or 'Port Set'
- ICMP Details: States the ICMP message that must be detected to trigger the action. See Adding and Editing a Firewall Rule for details of available messages that can be displayed.
- IP Details: States the type of IP protocol that must be detected to trigger the action: See Adding and Editing a Firewall Rule to see the list of available IP protocols that can be displayed here.
*If you chose to add a descriptive name when creating the rule then this name is displayed here rather than it's full parameters. See the next section, 'Adding and Editing a Firewall Rule', for more details.
**If you selected 'Log as a firewall event if this rule is fired' then the action is postfixed with 'Log'. (e.g. Block & Log)
Adding and Editing a Firewall Rule
The Firewall Rule Interface is used to configure the actions and conditions of an individual Firewall rule. If you are not an experienced firewall user or are unsure about the settings in this area, we advise you first gain some background knowledge by reading the sections 'Understanding Firewall Rules', 'Overview of Rules and Policies' and 'Creating and Modifying Firewall Rulesets'.
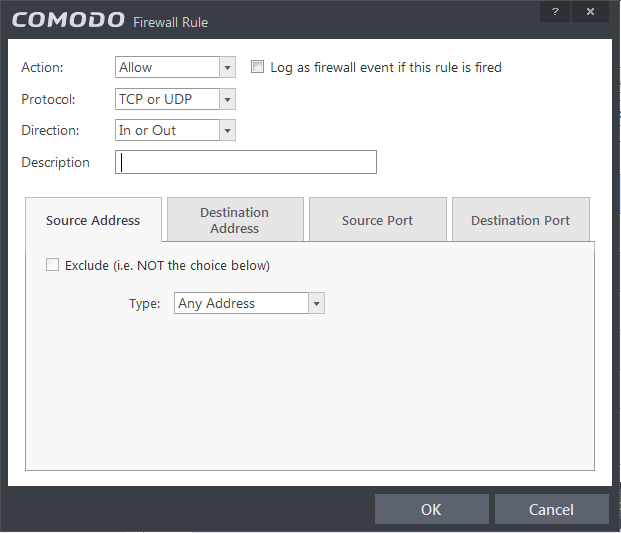
- Action: Define the action the firewall takes when the conditions of the rule are met. Options available via the drop down menu are 'Allow' (Default), 'Block' or 'Ask'.
- Protocol: Allows the user to specify which protocol the data packet should be using. Options available via the drop down menu are 'TCP', 'UDP', 'TCPor UDP' (Default), 'ICMP' or 'IP'.
|
Note: Your choice here alters the choices available to you in the tab structure on the lower half of the interface. |
- Direction: Allows you specify the direction in which the packets are traveling in order for the rule to apply. Options available via the drop down menu are 'In', 'Out' or 'In or Out' (Default).
- Log as a firewall event if this rule is fired: Checking this option creates an entry in the firewall event log viewer whenever this rule is called into operation. (i.e. when ALL conditions have been met) (Default = Disabled).
- Description: Allows you to type a friendly name for the rule. Some users find it more intuitive to name a rule by it's intended purpose. ( 'Allow Outgoing HTTP requests'). If you create a friendly name, then this is displayed to represent instead of the full actions/conditions in the main Application Rules interface and the Application Rule interface.
Protocol
-
TCP', 'UPD' or 'TCP or UDP'
If you select 'TCP', 'UPD' or 'TCP or UDP' as the Protocol for your network, then you have to define the source and destination IP addresses and ports receiving and sending the information.
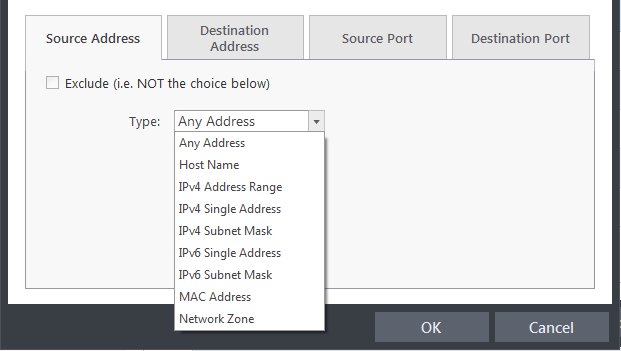
Source Address and Destination Address:
-
You can choose any IP Address by selecting Any Address in the Type drop-down box. This menu defaults to an IP range of 0.0.0.0- 255.255.255.255 to allow connection from all IP addresses.
-
You can choose a named host by selecting a Host Name which denotes your IP address.
-
You can choose an IPv4 Range by selecting IPv4 Address Range - for example the range in your private network and entering the IP addresses in the Start Range and End Range text boxes.
-
You can choose a Single IPv4 address by selecting IPv4 Single Address and entering the IP address in the IP address text box, e.g., 192.168.200.113.
-
You can choose IPv4 Mask by selecting IPv4 Subnet Mask. IP networks can be divided into smaller networks called sub-networks (or subnets). An IP address/ Mask is a subnet defined by IP address and mask of the network. Enter the IP address and Mask of the network.
-
You can choose a Single IPv6 address by selecting IPv6 Single Address and entering the IP address in the IP address text box, e.g., 3ffe:1900:4545:3:200:f8ff:fe21:67cf.
-
You can choose IPv6 Mask by selecting IPv6 Subnet Mask. IP networks can be divided into smaller networks called sub-networks (or subnets). An IP address/ Mask is a subnet defined by IP address and mask of the network. Enter the IP address and Mask of the network.
-
You can choose a MAC Address by selecting MAC Address and entering the address in the address text box.
-
You can choose an entire network zone by selecting Zone .This menu defaults to Local Area Network. But you can also define your own zone by first creating a Zone through the 'Network Zones' area.
-
Exclude (i.e. NOT the choice below): The opposite of what you specify is applicable. For example, if you are creating an Allow rule and you check the Exclude box in the Source IP tab and enter values for the IP range, then that IP range is excluded. You have to create a separate Allow rule for the range of IP addresses that you DO want to use.
Source Port and Destination Port:
Enter the source and destination Port in the text box.
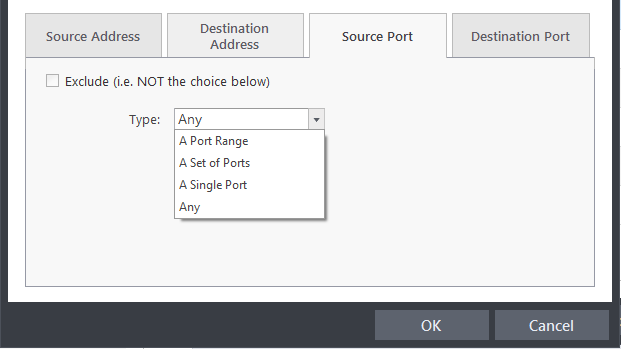
-
You can choose any port number by selecting Any - set by default , 0- 65535.
-
You can choose a Single Port number by selecting Single Port and selecting the single port numbers from the list.
-
You can choose a Port Range by selecting Port Range and selecting the port numbers from the From and To list.
-
You can choose a predefined Port Sets by choosing A Set of Ports.1.If you wish to create a custom port set then please see the section 'Port Sets'.
-
ICMP
When you select ICMP as the protocol in General Settings, you are shown a list of ICMP message types in the 'ICMP Details' tab alongside the Destination Address tabs. The last two tabs are configured identically to the explanation above. You cannot see the source and destination port tabs.
-
ICMP Details
ICMP (Internet Control Message Protocol) packets contain error and control information which is used to announce network errors, network congestion, timeouts, and to assist in troubleshooting. It is used mainly for performing traces and pings. Pinging is frequently used to perform a quick test before attempting to initiate communications. If you are using or have used a peer-to-peer file-sharing program, you might find yourself being pinged a lot. So you can create rules to allow / block specific types of ping requests. With Comodo Firewall you can create rules to allow/ deny inbound ICMP packets that provide you with information and minimize security risk.
Type in the source/ destination IP address. Source IP is the IP address from which the traffic originated and destination IP is the IP address of the computer that is receiving packets of information.
Under the 'ICMP Details' tab, choose the ICMP version from the 'Type' drop-down.
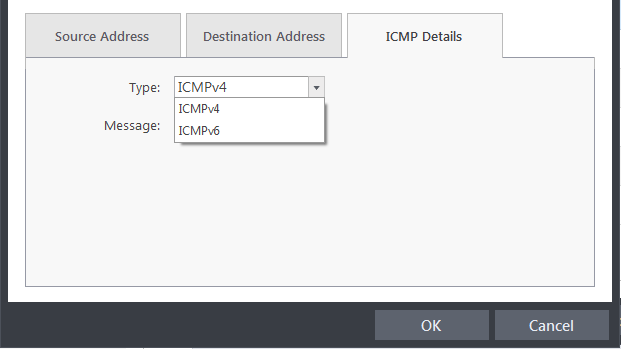
3. Specify ICMP Message, Types and Codes. An ICMP message includes a Message that specifies the type, that is, the format of the ICMP message.
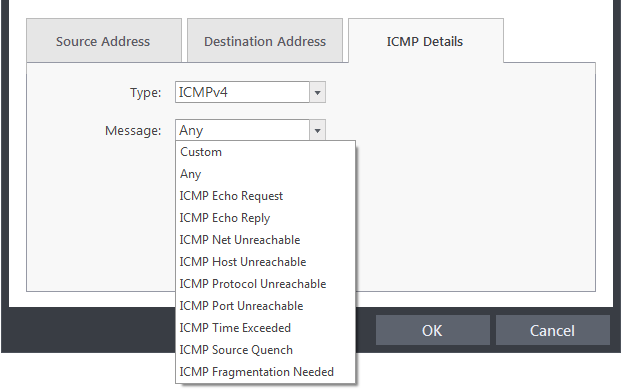
When
you select a particular ICMP message , the menu defaults to set its
code and type as well. If you select the ICMP message type 'Custom'
then you are asked to specify the code and type.
-
IP
When you select IP as the protocol in General Settings, you are shown a list of IP message type in the 'IP Details' tab alongside the Source Address and Destination Address tabs. The last two tabs are configured identically to the explanation above. You cannot see the source and destination port tabs.
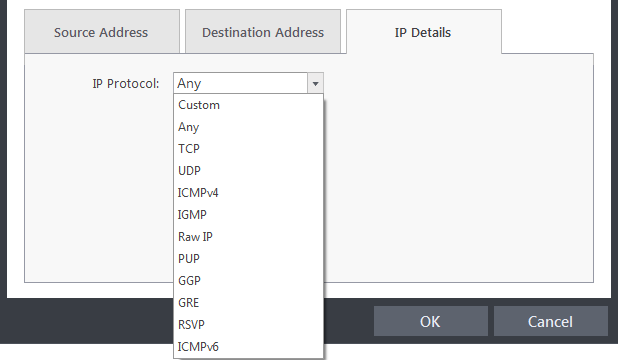
- IP Details
Select the types of IP protocol that you wish to allow, from the ones that are listed.



