Run a Full Computer Scan
A 'Full System Scan' scans every local drive, folder and file on your system. External devices such as USB drives, storage drives and digital cameras will also be scanned.
You can customize which items are included in a full scan and set-up a scan schedule from the 'Advanced Tasks' interface.
Refer to Antivirus Settings > Scan Profiles for more details.
To run a Full Computer Scan
- Click 'Scan' from the General Tasks interface the click 'Full System Scan' from the 'Scan' interface.
The scanner will start and first check whether your virus signature database is up-to-date.
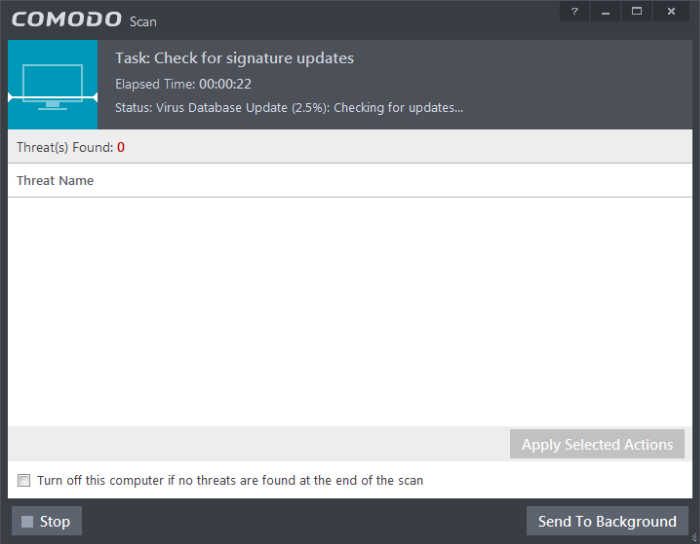
If the database is outdated, CIS will first download and install the latest database before commencing the scan.
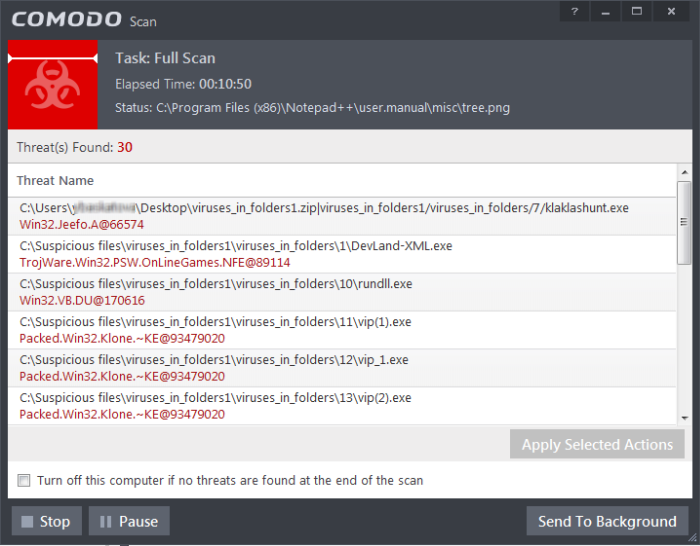
- You can pause, resume or stop the scan by clicking the appropriate button. If you want to run the scan in the background, click 'Send to Background'.
If you send to the background, you can continue to check scan progress by clicking 'Task
Manager' on the home screen or by clicking 'Open
Task Manager' icon from the Advanced Tasks interface.
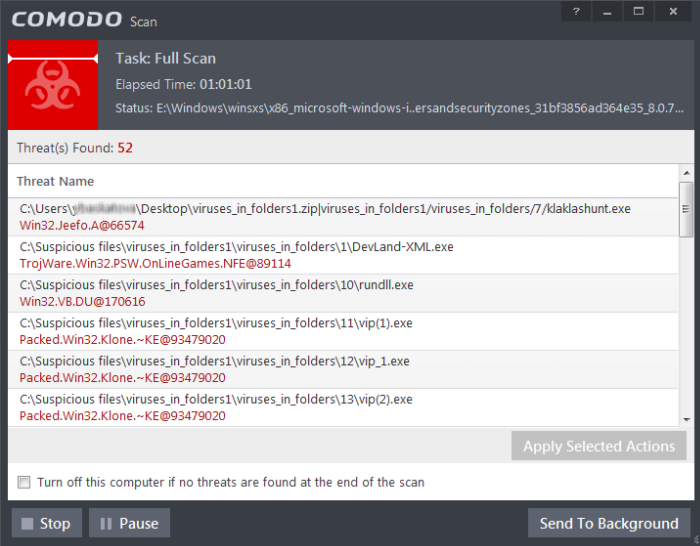
- Any detected threats will be displayed in full at the end of the scan. The alert will tell you how many threats were found; the name and location of the threats and will provide you with virus removal options:
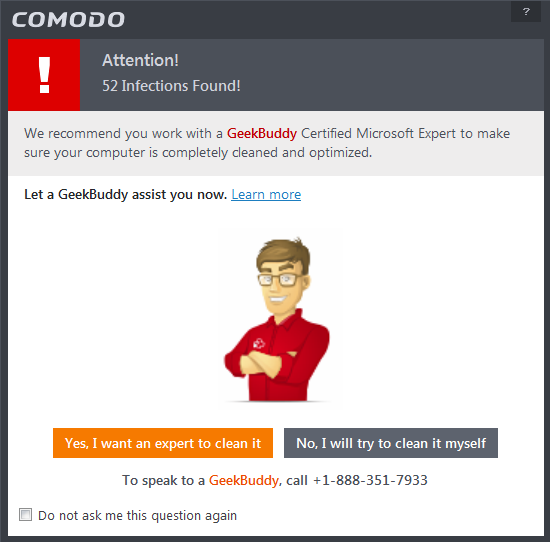
- If you wish to have a skilled professional from Comodo to access your system and perform an efficient disinfection, click 'Yes, I want an expert to clean it'. If you are a first-time user, you will be taken to Comodo GeekBuddy webpage to sign-up for a GeekBuddy subscription. If you have already signed-up for GeekBuddy services, the support chat session will start and a skilled technician will offer to clean your system.
For more details on Live Expert, refer to the section Comodo GeekBuddy.
- If you wish to clean the infections yourself, select 'No, I will try to clean it myself'. The scan results screen will be displayed.
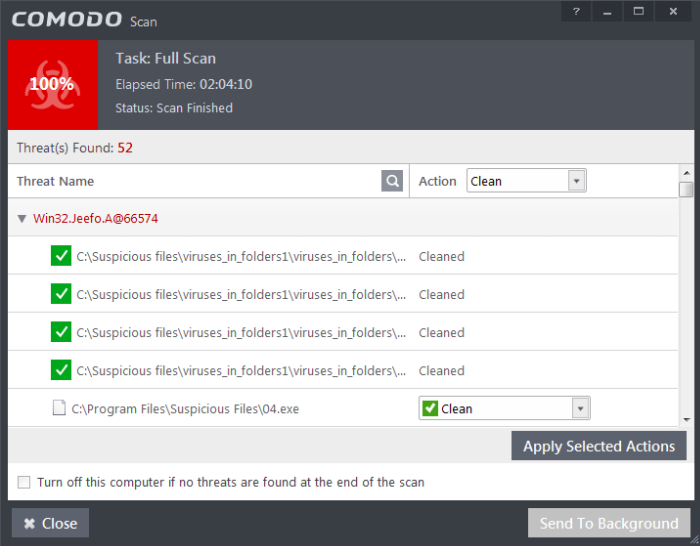
The scan results window displays the number of objects scanned and the number of threats (Viruses, Rootkits, Malware and so on). You can choose to clean, move to quarantine or ignore the threat based in your assessment. Refer to Processing the infected files for more details.



