Viruscope
Viruscope monitors the activities of processes running on your computer and alerts you if they take actions that could potentially threaten your privacy and/or security. Apart from forming yet another layer of malware detection and prevention, the sub-system represents a valuable addition to the core process-monitoring functionality of the Defense+ by introducing the ability to reverse potentially undesirable actions of software without necessarily blocking the software entirely. This feature can provide you with more granular control over otherwise legitimate software which requires certain actions to be implemented in order to run correctly.
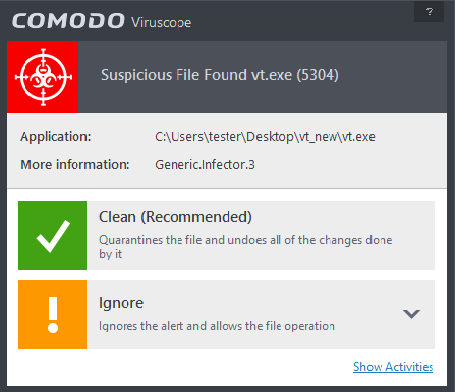
Viruscope alerts give you the opportunity to quarantine the process & reverse its changes or to let the process go ahead. Be especially wary if a Viruscope alert pops up 'out-of-the-blue' when you have not made any recent changes to your computer.
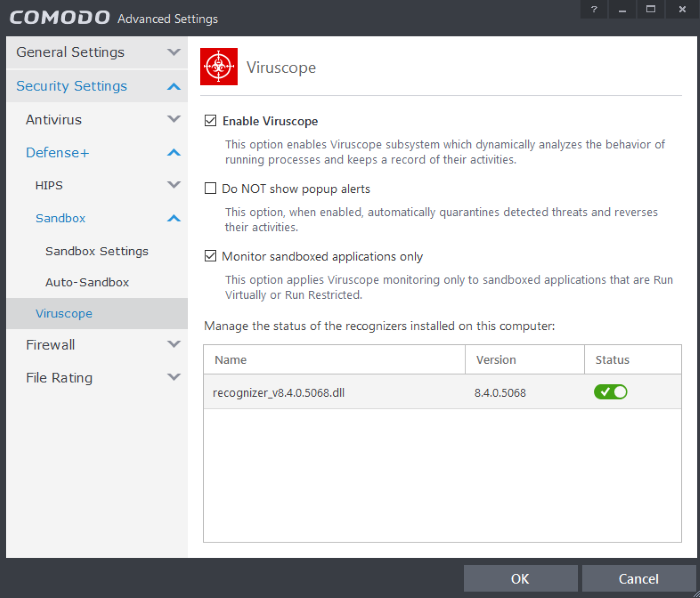
The 'Viruscope' configuration panel can be accessed by clicking 'Tasks > Advanced Tasks > Open Advanced Settings > Security Settings > Defense + > Viruscope'.
Viruscope is capable of monitoring all running processes and, if suspicious activity is detected, can generate alerts that let you quarantine the application and undo its activities.
- Enable Viruscope (Recommended) - Allows you to enable or disable Viruscope. If enabled, Viruscope monitors the activities of running processes and generates alerts if suspicious activity is detected. (Default = Enabled )
- Do NOT show pop-up alerts- Allows you to configure whether or not CIS should show an alert if Viruscope detects a suspicious activity. Choosing 'Do not show pop-up alerts' will minimize disturbances but at some loss of user awareness. If you choose not to show alerts then detected threats are automatically quarantined and their activities are reversed. (Default = Disabled)
- Monitor sandboxed applications only - If enabled, Viruscope will only monitor and generate alerts for processes running in the sandbox. (Default = Enabled)
Manage the status of recognizers
Viruscope detects zero-day malware by analyzing the behavior and actions of an application. If the detected behavior corresponds to that of known malware, then Viruscope will generate an alert which allows you to quarantine the application and reverse any changes that it made.
A 'recognizer' file contains the sets of behaviors that Viruscope needs to look out for. If you disable a particular recognizer, then Viruscope will no longer raise an alert if an application exhibits the behaviors referenced in the file. We recommend most users to leave the 'Status' of recognizers at their default settings. Advanced users, however, may want to try disabling recognizers if they are experiencing a large number of Viruscope false positives.



