Syslog Policy
The 'Syslog' policy allows administrators to configure the agent installed on one endpoint to listen to a specified port of remote endpoints with no agent installed, in order to collect the logs from them, for example from a Syslog server, Linux servers and Windows servers that use syslog protocol in order to collect the logs. Please note that these systems must be configured to send logs from syslog to the endpoint on which the agent is installed. Multiple remote endpoints can be added for a single policy and each endpoint can be configured to provide log pertaining to specific events. No schedule and blackout options are available for this type of policy.
To create a syslog policy
- Open the Collection Policies interface by clicking the 'Navigational Menu' button from the top right, choosing 'Agents' from the options and then clicking 'Collection Policies'.
- Click the 'Add' button at the bottom of the 'Collection Policies' screen at the left.
The configuration screen for creating a new policy will be displayed.
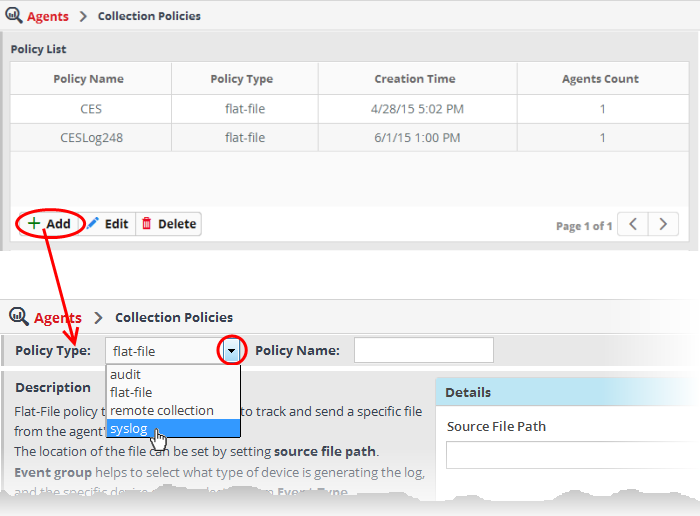
- Choose 'syslog' from the 'Policy Type' drop-down.
The configuration screen for syslog policy will be displayed.
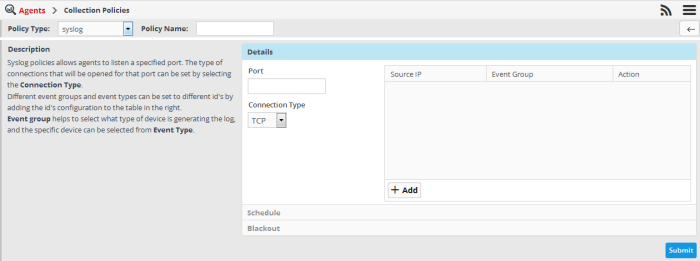
- Enter a name for the new policy in the 'Policy Name' field
Next you need to configure the details defining the source of log collection.
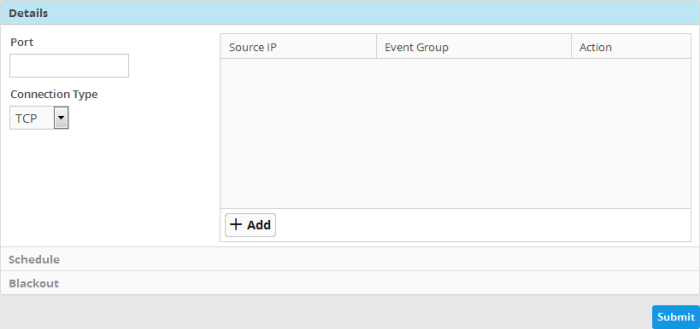
- Port - Specify the port number which will be used by the agent in one endpoint to connect to the remote endpoint(s).
- Connection Type - Select the type of connection protocol to be used for the agent to connect to the remote endpoint to collect the logs from the drop-down. The options available are TCP, UDP and BOTH.
|
Note: The port number and the connection type should match with the syslog connection configuration made at the remote endpoints. |
- Click the 'Add' button at the bottom end of the list of remote endpoints. to add the endpoints from which the logs should be fetched.
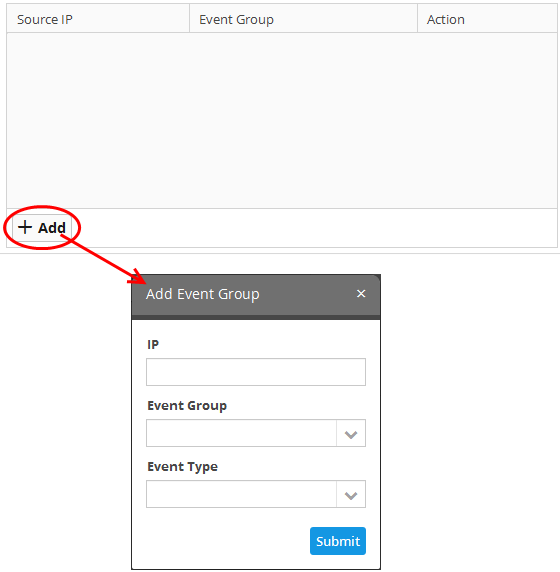
- IP - Enter the IP address of the remote endpoint.
- Event Group - Select the 'Event Group' for which the log should be collected. The options available are:
- Firewall and UTM
- Application
- Endpoint Security
- Data Protection
- Network Intrusion Detection & Protection
- Network Monitoring
- Event Type - Choose the product for which the logs are to be collected, based on the chosen event group.
- Click the 'Submit' button in the 'Add Event Group' dialog.
- Repeat the process to add more number of remote endpoints.
- Click the 'Submit' button to save your changes.
The policy will be added to NxSIEM and will be available for deployment to endpoints. Refer to the section. Refer to the section 'Configuring Log Collection Policies' for more details on deploying the newly created policy onto customer's endpoints.



