Manage Trusted Vendors
There are two way that an application can be treated as safe in Comodo Cleaning Essentials.
- It is whitelisted. This means it is on Comodo's list of software which we have tested and know to be safe.
- It is signed by one of the vendors in the 'Trusted Software Vendor' list.
- IF the vendor is on the 'Trusted Software Vendor' list, the application will be trusted and allowed to run.
Software publishers may be interested to know that they can have their signatures added, free of charge, to the 'master' Trusted Software Vendor List that ships to all users with CCE. Details about this can be found at the foot of this page.
To access the 'Trusted Software Vendors' interface, click 'Tools' > 'Manage Trusted Vendors'.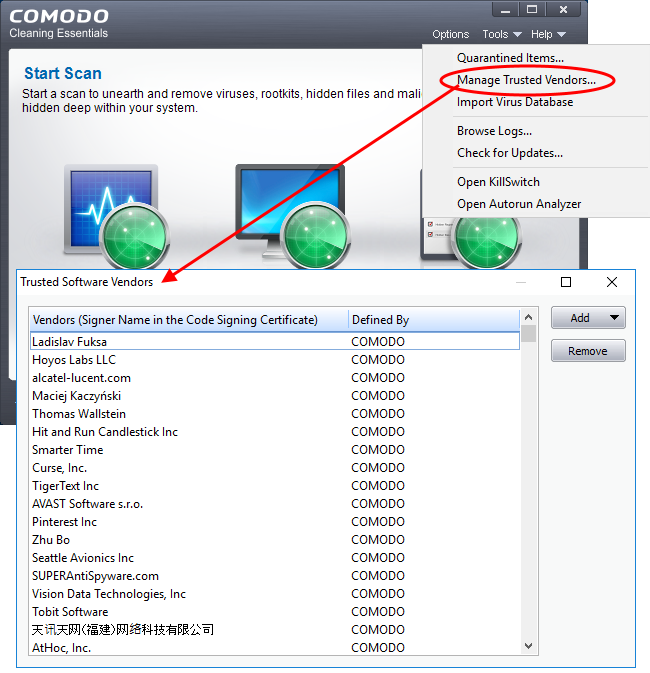
Column Descriptions
- Vendors - The company that published the software, and digitally signed their software.
- Defined By - Indicates whether the vendor was added to 'Trusted Software Vendor' list by Comodo (the vendor is globally whitelisted), or by the user
Background
Many software vendors digitally sign their software with a code signing certificate. This practice helps end-users to verify:
If a file is signed by a Trusted Software Vendor and the user has enabled 'Trust Applications that are digitally signed by Trusted Software Vendors' then it will be automatically trusted by CCE (if you would like to read more about code signing certificates, see http://www.instantssl.com/code-signing/).
One way of telling whether an executable file has been digitally signed is checking the properties of the .exe file in question. For example, the main program executable for CCE is called 'cce.exe' and has been digitally signed.
- Browse to the (default) installation directory of Comodo Cleaning Essentials
- Right click on the file cce.exe
- Select 'Properties' from the menu
- Click the tab 'Digital Signatures (if there is no such tab then the software has not been signed)
This displays the name of the CA that signed the software as shown below: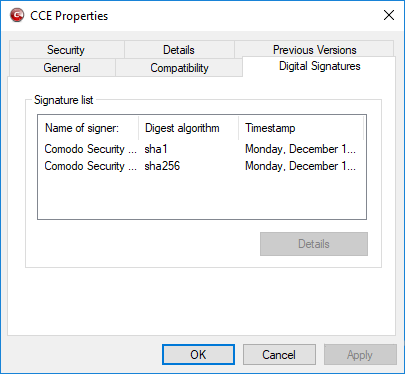
- Click the 'Details' button to view digital signature information
- Click 'View Certificate' to inspect the actual code signing certificate. (see below):
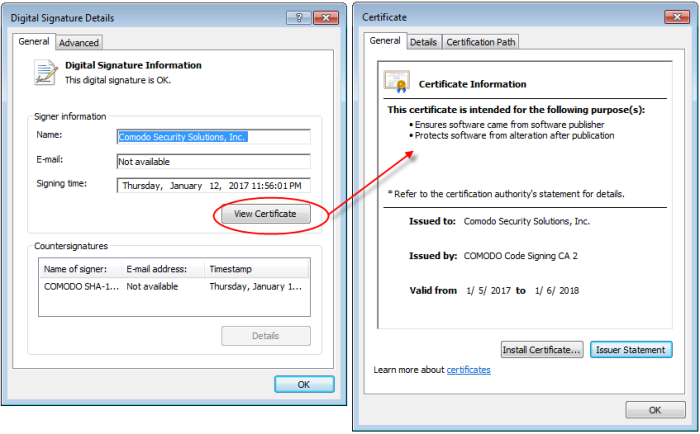
It should be noted that the example above is a special case in that Comodo, as creator of 'cce.exe', is both the signer of the software and, as a trusted CA, it is also the counter-signer (see the 'Countersignatures' box). In the vast majority of cases, the signer or the certificate (the vendor) and the counter-signer (the Trusted CA) are different. See this example for more details.
Add and Define a User-Trusted Vendor
A software vendor can be added to the local 'Trusted Software Vendors' list by reading the vendor's signature from an executable file on your local drive.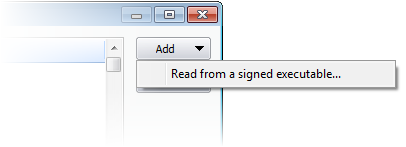
- Click the 'Add' button on the right and select 'Read from a signed executable...'. Browse to the location of the executable your local drive. In the example below, we are adding the executable 'Viber.exe'.
- After clicking 'Open', CCE checks that the .exe file is signed by the vendor and counter-signed by a Trusted CA. If so, the vendor (software signer) is added to the Trusted Vendor list (TVL):
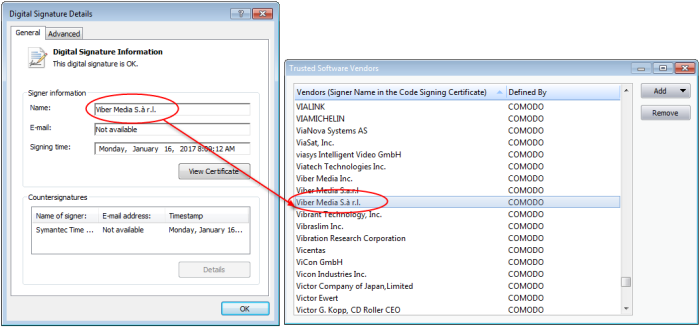
In the example above, CCE was able to verify and trust the vendor signature on Viber.exe because it had been counter-signed by the trusted CA 'Symantec'. The software signer 'Viber Media S.à r.l.' is now a Trusted Software Vendor and is added to the list. All future software that is signed by the vendor 'Viber Media Inc.' is automatically added to the Comodo Trusted Vendor list.
The Trusted Vendor Program for Software Developers
Software vendors can have their software added to the default Trusted Vendor list that is shipped with CCE. This service is free of cost and is also open to vendors that have used code signing certificates from any Certificate Authority. Upon adding the software to the Trusted Vendor list, CCE automatically trusts the software and does not generate any warnings or alerts on installation or use of the software.
The vendors have to apply for inclusion in the Trusted Vendors list through the sign-up form at http://internetsecurity.comodo.com/trustedvendor/signup.php and make sure that the software can be downloaded by our technicians. Our technicians check whether:
- The software is signed with a valid code signing certificate from a trusted CA;
- The software does not contain any threats that harm a user's PC;
More details are available at http://internetsecurity.comodo.com/trustedvendor/overview.php



