Verify Authenticity of Applications
A program is considered safe to run if it is digitally signed by a 'Trusted Software publisher'. To prove their software is the genuine article, publishers digitally sign their software using a code signing certificate.If you would like to know more about this process, see Background details later in this section.
To check whether an application/program installed in your computer is digitally signed:
- Select a process in the KillSwitch process list
- Click 'Tools' > 'Verify File Signature'
The 'Verify Signatures' dialog will open:
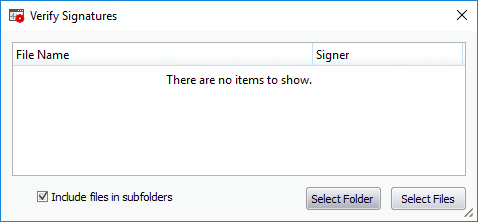
You can check the authenticity of a specific executable or make KillSwitch to scan a folder to identify all the .exe, .dll, .msi and .sys files in it and verify their authenticity.
- Click 'Select Files' and navigate to the folder containing the files of the program and select the binary/executable file, to check for authenticity of a file.
- Click 'Select Folder' and navigate to the folder , to scan a folder for binaries and verify their signatures. KillSwitch will identify the .exe, .sys, .msi and .dll files in the selected folder. If you want KillSwitch to check the files in the sub-folder(s) of the selected folder, select 'Include files in sub-folders'.
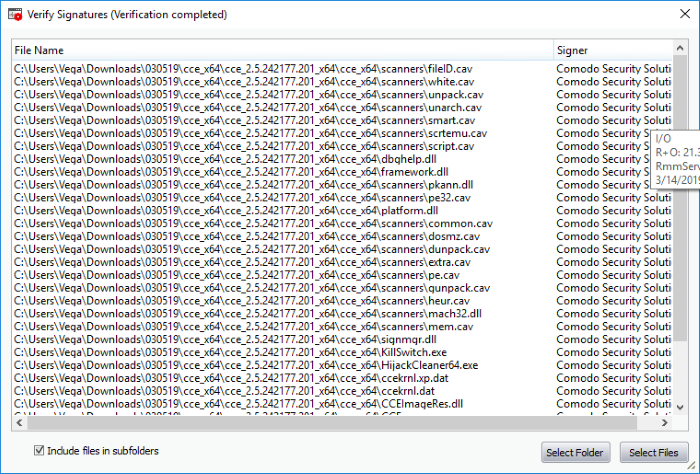
Many software vendors digitally sign their software with a code signing certificate. This practice helps end-users to verify:
-
Content Source: The software they are downloading and are about to install really comes from the publisher that signed it.
-
Content Integrity: That the software they are downloading and are about to install has not be modified or corrupted since it was signed.
In short, users benefit if software is digitally signed because they know who published the software and that the code hasn't been tampered with - that are are downloading and installing the genuine software.
The 'Vendors' that digitally sign the software to attest to it's probity are the software publishers. These are the company names you see listed in the first column in the graphic above.
However, companies can't just 'sign' their own software and expect it to be trusted. This is why each code signing certificate is counter-signed by an organization called a 'Trusted Certificate Authority'. 'Comodo CA Limited' and 'Verisign' are two examples of a Trusted CA's and are authorized to counter-sign 3rd party software. This counter-signature is critical to the trust process and a Trusted CA only counter-signs a vendor's certificate after it has conducted detailed checks that the vendor is a legitimate company.
If a file is signed by a Trusted Software Vendor and the user has enabled 'Trust Applications that are digitally signed by Trusted Software Vendors' then it will be automatically trusted by Comodo Internet Security (if you would like to read more about code signing certificates, see http://www.instantssl.com/code-signing/).
One way of telling whether an executable file has been digitally signed is checking the properties of the .exe file in question. For example, the main program executable for Comodo KillSwitch is called 'KillSwitch.exe' and has been digitally signed.
-
Browse for the folder containing the Comodo Cleaning Essentials files
-
Right-click on the file KillSwitch.exe
-
Select 'Properties' from the menu
-
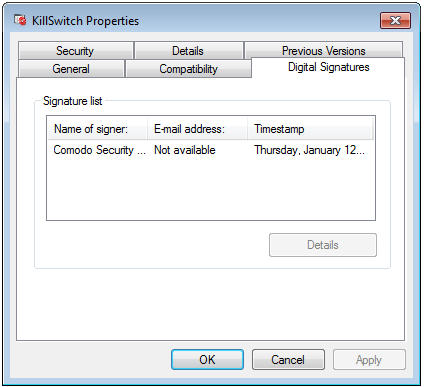
Click the tab 'Digital Signatures' (if there is no such tab then the software has not been signed).
This displays the name of the CA that signed the software as shown below:
- Select the certificate and click the 'Details' button to view digital signature information
- Click 'View Certificate' to inspect the actual code signing certificate. (see below)
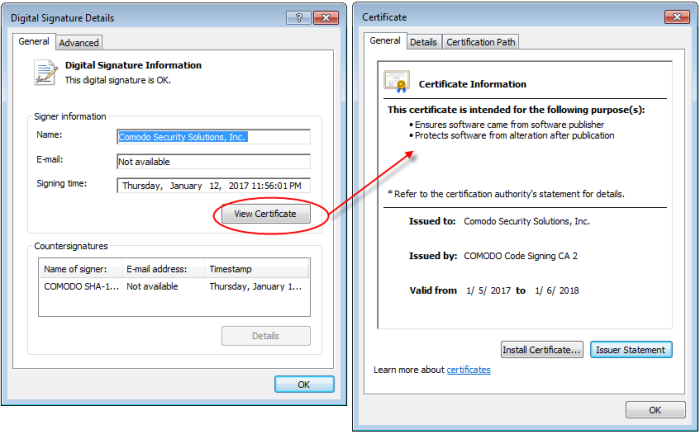
It should be noted that the example above is a special case in that Comodo, as creator of 'KillSwitch.exe', is both the signer of the software and, as a trusted CA, it is also the counter-signer (see the 'Countersignatures' box). In the vast majority of cases, the signer or the certificate (the vendor) and the counter-signer (the Trusted CA) are different.



