Behavior Blocker
The Behavior Blocker is an integral part of the Defense+ engine and is responsible for authenticating every executable image that is loaded into the memory. The Behavior Blocker intercepts all files before they are loaded into memory and intercepts prefetching/caching attempts for those files. It calculates the hash of the executable at the point it attempts to load into the memory. It then compares this hash with the list of known / recognized applications that are on the Comodo safe list. If the hash matches the one on record for the executable, then the application is safe and the Behavior Blocker allows it to run. If no matching hash is found on the safelist, then the executable is 'unrecognized' and is run inside the auto-sandbox. You will be notified via an alert when this happens.
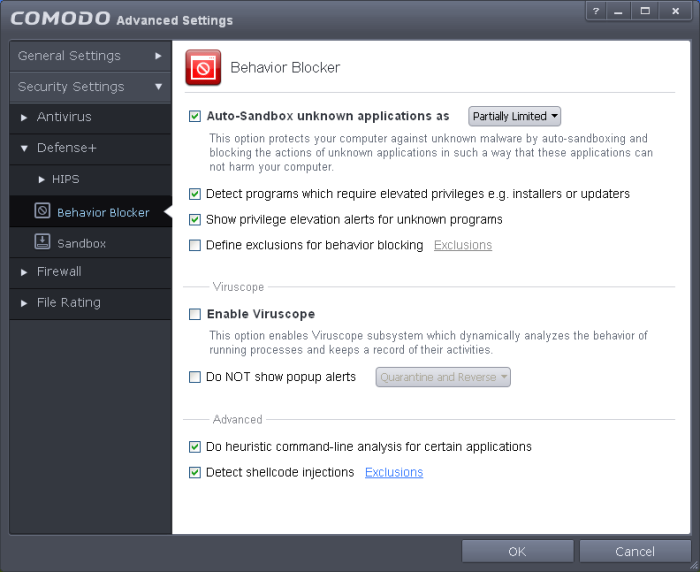
The 'Behavior Blocker' configuration panel can be accessed by clicking 'Tasks > Advanced Tasks > Open Advanced Settings > Security Settings > Defense + > Behavior Blocker'. This panel allows you to quickly determine how proactive the Behavior Blocker should be and which types of files it should check.
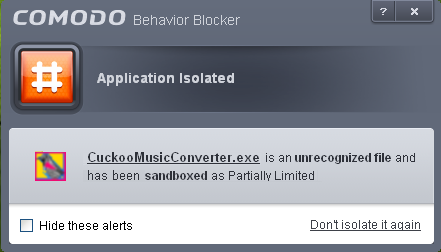
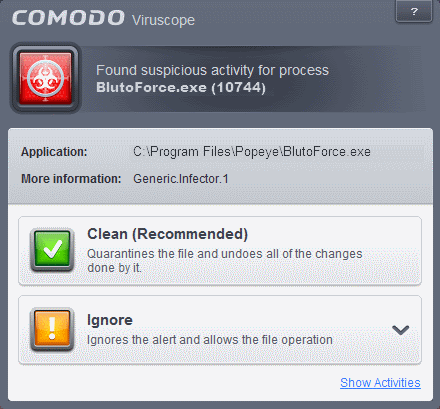
Viruscope monitors the activities of processes running on your computer and alerts you if they take actions that could potentially threaten your privacy and/or security. Apart from forming yet another layer of malware detection and prevention, the sub-system represents a valuable addition to the core process-monitoring functionality of the Behavior Blocker by introducing the ability to reverse potentially undesirable actions of software without necessarily blocking the software entirely. This feature can provide you with more granular control over otherwise legitimate software which requires certain actions to be implemented in order to run correctly.
Viruscope alerts give you the opportunity to quarantine the process & reverse its changes or to let the process go ahead. Be especially wary if a Viruscope alert pops up 'out-of-the-blue' when you have not made any recent changes to your computer.
The Behavior Blocker settings panel allows you to configure the following:
|
Note: The Behavior Blocker configuration setting can also be set in the 'Advanced View' of the 'Home' screen beside the Auto-Sandbox status link in the 'Defense+ and Sandbox' pane. |
-
Auto-sandbox unknown applications as - Allows you to enable or disable the Behavior Blocker. If enabled, the Behavior Blocker runs unrecognized applications inside the auto-sandbox with the access restriction as selected in the drop down menu. (Default = 'Enabled' with 'Partially Limited')
|
Note: The 'auto-sandbox' referred to here is distinct from the Virtual Desktop discussed in Sandbox Tasks. For the most part, the 'auto-sandbox' is a non-virtual environment under which unrecognized applications are allowed to run under a set of strict access restrictions (default='Partially Limited'). These restrictions prevent the application from taking actions that are damaging to your system. Users can, however, enable 'Full Virtualization' of auto-sandboxed files in the Behavior Blocker settings. |
Configuring Access Restriction
The Behavior Blocker will auto-sandbox an unknown executable and restrict its execution privileges according to an access restriction level set by you. Access restriction levels determine what level of rights a sandboxed application has to access other software and hardware resources on your computer:
-
Partially Limited - The application is allowed to access all operating system files and resources like the clipboard. Modification of protected files/registry keys is not allowed. Privileged operations like loading drivers or debugging other applications are also not allowed.(Default)
-
Limited - Only selected operating system resources can be accessed by the application. The application is not allowed to execute more than 10 processes at a time and is run without Administrator account privileges.
-
Restricted - The application is allowed to access very few operating system resources. The application is not allowed to execute more than 10 processes at a time and is run with very limited access rights. Some applications, like computer games, may not work properly under this setting.
-
Untrusted - The application is not allowed to access any operating system resources. The application is not allowed to execute more than 10 processes at a time and is run with very limited access rights. Some applications that require user interaction may not work properly under this setting.
-
Blocked - The application is not allowed to run at all.
-
Detect programs which require elevated privileges : Allows you to instruct the Behavior Blocker to display alerts when an installer or updater requires administrator or elevated privileges to run. An installer that is allowed to run with elevated privileges is permitted to make changes to important areas of your computer such as the registry. Refer to the section Understanding Security Alerts for more details.
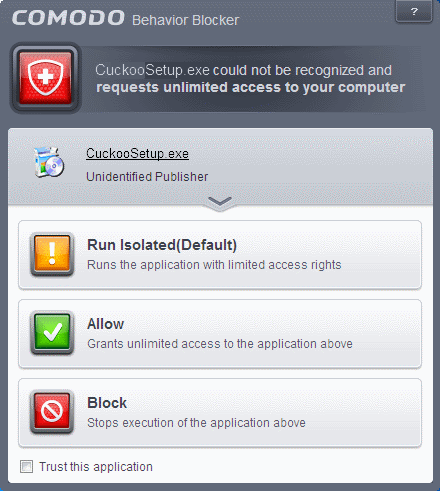
You can decide on whether or not to allow the installer or update based on your assessment, from the alert itself. (Default=Enabled)
-
Show privilege elevation alerts for unknown programs : Allows you to instruct the Behavior Blocker to display alerts when a new or unrecognized program, application or executable requires administrator or elevated privileges to run. You can decide on whether or not to allow the the unknown application based on your assessment, from the alert itself. (Default=Enabled)
-
Define exclusions for behavior blocking - Allows you to add file paths which are to be excluded from monitoring by the Behavior Blocker. The executables included in the exclusions area are allowed to run without authenticity checking. (Default = Disabled)
|
Note: The files added through this interface will be exempted only from monitoring by Behavior Blocker. To exclude a file from monitoring by all the components of CIS including Antivirus, Firewall, HIPS and Behavior Blocker, add it to Trusted Files list. |
To define exclusions
-
Select the 'Define exclusions for behavior blocking' checkbox and click the Exclusions link. The 'Manage exclusions' dialog will appear.
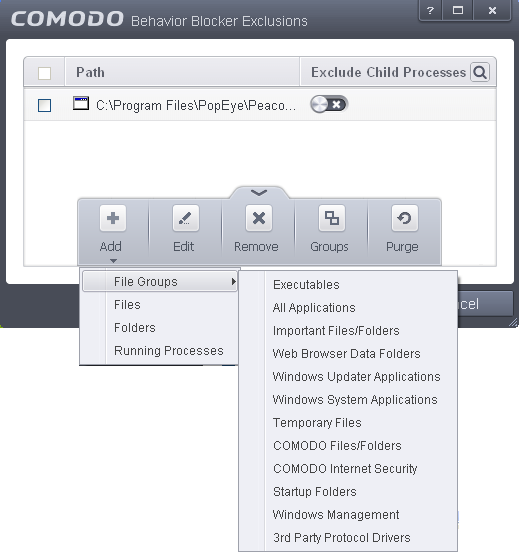
-
Click the handle at the bottom of the interface and choose 'Add'
-
You can add items by selecting the required option from the drop-down:
-
File Groups - Enables you to select a category of pre-set files or folders. For example, selecting 'Executables' would enable you to create a ruleset for all files with the extensions .exe .dll .sys .ocx .bat .pif .scr .cpl . Other such categories available include 'Windows System Applications' , 'Windows Updater Applications' , 'Start Up Folders' etc. For more details on file groups, refer to the section File Groups.
-
Running Processes - As the name suggests, this option allows you to select an application or executable from the processes that are currently running on your PC.
-
Browse Folders - Opens the 'Browse for Folders' window and enables you to navigate to the folder you wish to add.
-
Browse File - Opens the 'Open' window and enables you to navigate to the application or file you wish to add.
-
After adding an item, choose whether or not the child processes of the files/applications also need to be excluded from Behavior Blocking using the toggle switch under the 'Exclude Child Process' column.
-
Click 'OK' to implement your settings.
Viruscope monitors the activities of all processes, regardless of whether they are running normally or inside the sandbox. If suspicious activity is detected, Viruscope will generate a pop-up alert that allows you to block or allow the activity.
-
Enable Viruscope (Recommended) - Allows you to enable or disable Viruscope. If enabled, the Viruscope monitors the activities of all the running processes and generates alerts on suspicious activities. (Default = 'Disabled')
-
Do NOT show popup alerts - Allows you to configure whether or not to show Viruscope alerts when a suspicious activity is recognized. Choosing 'Do not show popup alerts' will minimize disturbances but at some loss of user awareness. If you choose not to show alerts then you have a choice of default responses that CIS should automatically take - either 'Quarantine and Reverse' or 'Ignore'. (Default = Disabled)
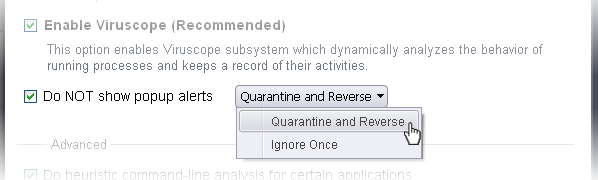
-
Quarantine and Reverse - Moves the process and its parent application to quarantine and reverses the action that was taken by the process. (Default)
-
Ignore Once - The action will be allowed for one time. If the same activity is recognized again, an alert will be generated.
Advanced Settings:
-
Do heuristic command-line analysis for certain applications - Selecting this option instructs Comodo Internet Security to perform heuristic analysis of programs that are capable of executing code such as visual basic scripts and java applications. Example programs that are affected by enabling this option are wscript.exe, cmd.exe, java.exe and javaw.exe. For example, the program wscipt.exe can be made to execute visual basic scripts (.vbs file extension) via a command similar to 'wscript.exe c:teststest.vbs'. If this option is selected, CIS detects c:teststest.vbs from the command-line and applies all security checks based on this file. If test.vbs attempts to connect to the Internet, for example, the alert will state 'test.vbs' is attempting to connect to the Internet (Default = Enabled).
If this option is disabled, the alert would only state 'wscript.exe' is trying to connect to the Internet'.
|
Background note: 'Heuristics' describes the method of analyzing a file to ascertain whether it contains codes typical of a virus. Heuristics is about detecting virus-like behavior or attributes rather than looking for a precise virus signature that matches a signature on the virus blacklist. This helps to identify previously unknown (new) viruses. |
-
Detect shellcode injections (i.e. Buffer overflow protection) - Enabling this setting turns-on the Buffer over flow protection.
Background: A buffer overflow is an anomalous condition where a process/executable attempts to store data beyond the boundaries of a fixed-length buffer. The result is that the extra data overwrites adjacent memory locations. The overwritten data may include other buffers, variables and program flow data and may cause a process to crash or produce incorrect results. They can be triggered by inputs specifically designed to execute malicious code or to make the program operate in an unintended way. As such, buffer overflows cause many software vulnerabilities and form the basis of many exploits.
Turning-on buffer overflow protection instructs the Comodo Internet Security to raise pop-up alerts in every event of a possible buffer overflow attack. You can allow or deny the requested activity raised by the process under execution depending on the reliability of the software and its vendor. Click here for more details on the alerts.
Comodo recommends that this setting to be maintained selected always (Default = Enabled).
To exclude some of the file types from being monitored under Detect Shellcode injections.
-
Select the 'Detect shellcode injections' checkbox and click the Exclusions link. The 'Manage Exclusions' dialog will appear.
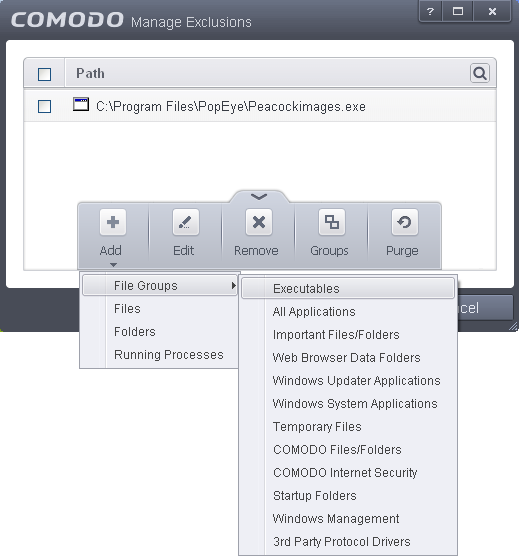
-
Click the handle from the bottom of the interface and choose 'Add'
-
You can add items by selecting the required option from the drop-down:
-
File Groups - Enables you to select a category of pre-set files or folders. For example, selecting 'Executables' would enable you to create a ruleset for all files with the extensions .exe .dll .sys .ocx .bat .pif .scr .cpl . Other such categories available include 'Windows System Applications' , 'Windows Updater Applications' , 'Start Up Folders' etc. For more details on file groups, refer to the section File Groups.
-
Running Processes - As the name suggests, this option allows you to select an application or executable from the processes that are currently running on your PC.
-
Browse Folders - Opens the 'Browse for Folders' window and enables you to navigate to the folder you wish to add.
-
Browse File - Opens the 'Open' window and enables you to navigate to the application or file you wish to add.
|
Note: These settings are recommended for advanced users only. |
-
Click 'OK' to implement your settings.



