- Introduction To Comodo Internet Security
- General Tasks – Introduction
- Firewall Tasks – Introduction
- Sandbox Tasks – Introduction
- Advanced Tasks – Introduction
- Advanced Settings
- Comodo GeekBuddy
- TrustConnect Overview
- Microsoft Windows - Configuration And Connection
- Mac OS X - Configuration And Connection
- Linux / Open VPN - Configuration And Connection
- Apple IPhone / IPod Touch - Configuration And Connection
- Android Devices - Configuration And Connection
- Windows Mobile Devices - Configuration And Connection
- TrustConnect FAQ
- Comodo Dragon
- Comodo BackUp
- Appendix 1 CIS How To... Tutorials
- Enable / Disable Security Components Easily
- Set Up The Firewall For Maximum Security And Usability
- Block Internet Access While Allowing Local Area Network (LAN) Access
- Block/allow Websites Selectively To Users Of Your Computer
- Set Up The HIPS For Maximum Security And Usability
- Set Up The Behavior Blocker For Maximum Security And Usability
- Password Protect Your CIS Settings
- Reset Forgotten Password (Advanced)
- Run An Instant Antivirus Scan On Selected Items
- Create An Antivirus Scanning Schedule
- Run Untrusted Programs Inside Sandbox
- Run Browsers Inside Sandbox
- Run Untrusted Programs Inside Virtual Desktop
- Run Browsers Inside The Virtual Desktop
- Restore Incorrectly Quarantined Item(s)
- Submit Quarantined Items To Comodo For Analysis
- Enable File Sharing Applications Like BitTorrent And Emule
- Block Any Downloads Of A Specific File Type
- Disable Behavior Blocker And Auto-Sandboxing On A Per-application Basis
- Enabling Full Virtualization For Auto-Sandboxed Applications
- Switch Between Complete CIS Suite And Individual Components (just AV Or FW)
- Switch Off Automatic Antivirus And Software Updates
- Suppress CIS Alerts Temporarily While Playing Games
- Renewal Or Upgrading Your License
- How To Use CIS Protocol Handlers
- Appendix 2 - Comodo Secure DNS Service
- Appendix 3 - Glossary Of Terms
- Appendix 4 - CIS Versions
- About Comodo Security Solutions
Network Zones
The Network Zones panel allows you to:
- Define network zones that are trusted, and to specify access privileges to them
- Define network zones that are untrusted, and to block access to them
The Network Zones panel can be accessed by clicking Security Settings > Firewall > Network Zones from the 'Advanced Settings' interface.
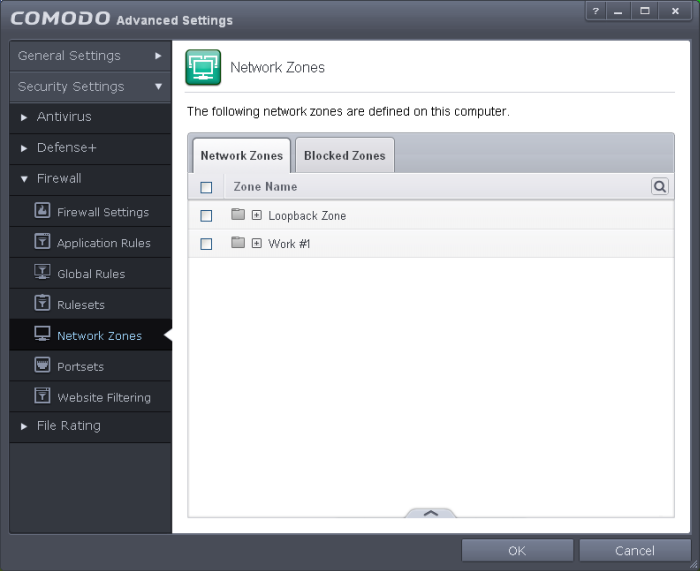
The panel has two tabs:
- Network Zones - Allows you to define network zones and to allow access to them for applications, with the access privileges specified through Application Rule interface. Refer to 'Creating or Modifying Firewall Rules' for more details.
- Blocked Zones - Allows you to define trusted networks that are not trustworthy and to block access to them.



