Manage Quarantined Items
The quarantine facility removes and isolates suspicious files into a safe location before analyzing them for possible infection. Any files transferred in this fashion are encrypted- meaning they cannot be run or executed. This isolation prevents infected files from affecting the rest of your server. If a file cannot be disinfected, then it provides a reliable safe-house until the virus database is updated- neutralizing the impact of any new virus.
The Quarantine interface can be accessed by clicking View Quarantine from the 'General Tasks' interface.
The
'Quarantine' interface displays a list of items moved to Quarantine
from the results of real-time scanning, on-demand scanning and
manually.
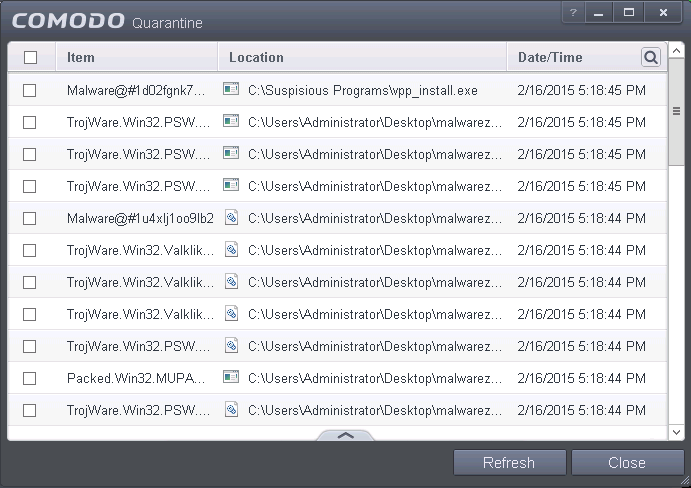
Column Descriptions
- Item - Indicates which application or process propagated the event;
- Location - Indicates the location where the application or the file is stored;
- Date/Time - Indicates date and time, when the item is moved to quarantine.
For details on adding executables identified as infected files during on-demand or real time scans to Quarantine, refer to G eneral Tasks > Scan and Clean Your Server.
The Quarantined Items interface also allows you to:
Manually adding files as Quarantined Items
If you have a file, folder or drive that you suspect may contain a virus and not been detected by the scanner, then you have the option to isolate that item in quarantine.
To manually add a Quarantined Item
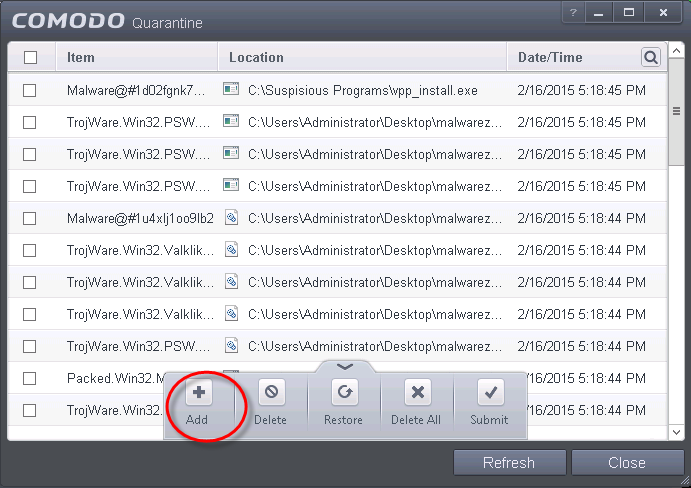
-
Click the handle from the bottom of the Quarantine interface and select 'Add' from the options.
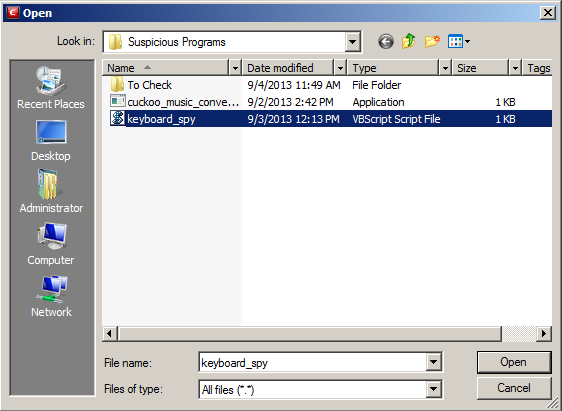
-
Navigate to the file you want to add to the quarantine and click 'Open'.
The file will be added to
Quarantine. You can even send the file for analysis to Comodo, for
inclusion in the white list or black list, by clicking Submit from
the options.
To delete a quarantined item from the system
- Select the item(s) from the 'Quarantine' interface
- Click the handle from the bottom of the interface and select 'Delete' option.
This deletes the file from the system permanently.
To restore a quarantined item to its original location
- Select the item(s) from the Quarantine interface
- Click the handle from the bottom of the interface and select 'Restore' option.
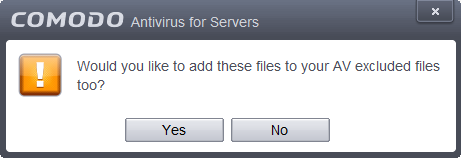
An option will be provided to add
the file(s) to Exclusions list and if 'Yes' is opted, these files will not be
scanned again.
The file will be restored to the
original location from where it was moved to Quarantine. If the
restored item does not contain a malware, it will operate as usual.
But if it contains a malware, it will be detected as a threat
immediately, if the Real-Time Scanning is enabled or during the next
scan if it is not added to Exclusions list while restoring.
To remove all the quarantined items permanently
- Click the handle from the bottom of the interface and select 'Clear' option.
All the quarantined items will be deleted from your system permanently.
To submit selected quarantined items to Comodo for analysis
- Select the item(s) from the Quarantine interface
- Click the handle from the bottom of the interface and select 'Submit' option.
You can submit the files which you suspect to be a malware or the files which you consider as safe but identified as malware by Comodo Antivirus (False Positives). Comodo will analyze all submitted files. If they are found to be trustworthy, they will be added to the Comodo safe list (i.e. white-listed). Conversely, if they are found to be malicious then they will be added to the database of virus signatures (i.e. black-listed).
| Note: Quarantined files are stored using a special format and do not constitute any danger to your server. |



