Filtering Defense+ Logs
CAVS allows you to create custom views of all logged events according to user defined criteria. You can use the following types of filters:
Clicking on the handle at the bottom enables you to filter the logs for a selected time period:
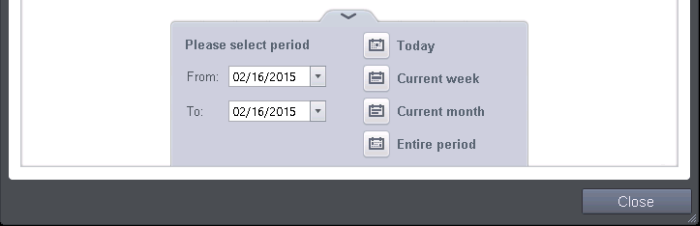
- Today - Displays all logged events for today.
- Current Week - Displays all logged events during the current week. (The current week is calculated from the Sunday to Saturday that holds the current date.)
- Current Month - Displays all logged events during the month that holds the current date.
- Entire Period - Displays every event logged since CAVS was installed. (If you have cleared the log history since installation, this option shows all logs created since that clearance).
- Custom Filter - Enables you to select a custom period by
choosing the 'From' and 'To' dates under 'Please Select Period'
Alternatively, you can right click inside the log viewer module and choose the time period.
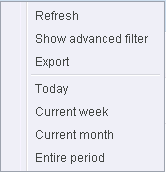
Having chosen a preset time filter from the top panel, you can further refine the displayed events according to specific filters. Following are available filters for Defense+ logs and their meanings:
- Application - Displays only the events propagated by a specific application
- Flags - Displays events according to the response (or action taken) by Defense+
- Target - Displays only the
events that involved a specified target application
To configure Advanced Filters for Defense+ events
-
Click the funnel button
 from
the title bar. The Advanced Filter interface for Defense+ events
will open.
from
the title bar. The Advanced Filter interface for Defense+ events
will open. -
Select the filter from the 'Advanced Filter' drop-down and click 'Add' to apply the filter.
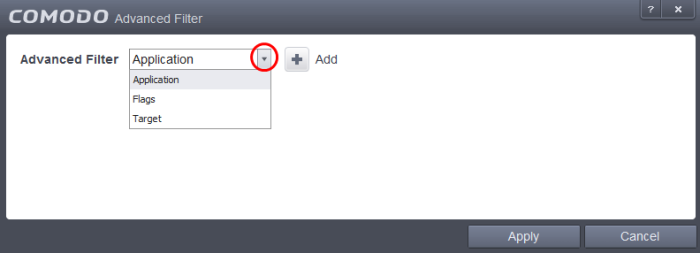
You have 3 categories of filter that you can add. Each of these categories can be further refined by either selecting or deselecting specific filter parameters or by the user typing a filter string in the field provided. Following are the options available in the 'Advanced Filter' drop-down:
-
Application: Selecting the 'Application' option displays a drop-down field and text entry field.
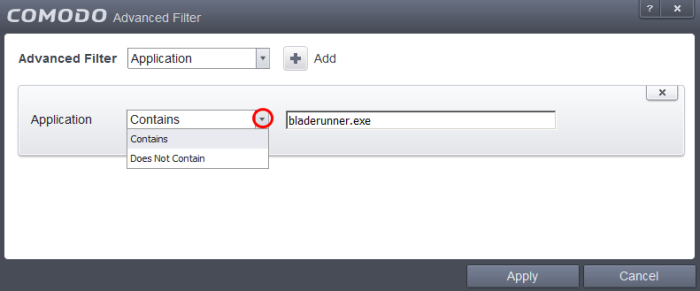
-
Select 'Contains' or 'Does Not Contain' option from the drop-down menu.
-
Enter the text or word that needs to be filtered.
For example, if you select 'Contains' option from the drop-down field and enter the phrase 'bladerunner.exe' in the text field, then all events containing the entry 'bladerunner.exe' in the 'Application' column will be displayed. If you select 'Does Not Contain' option from the drop-down field and enter the phrase 'bladerunner.exe' in the text field, then all events that do not have the entry 'bladerunner.exe' in the 'Application' column will be displayed.
-
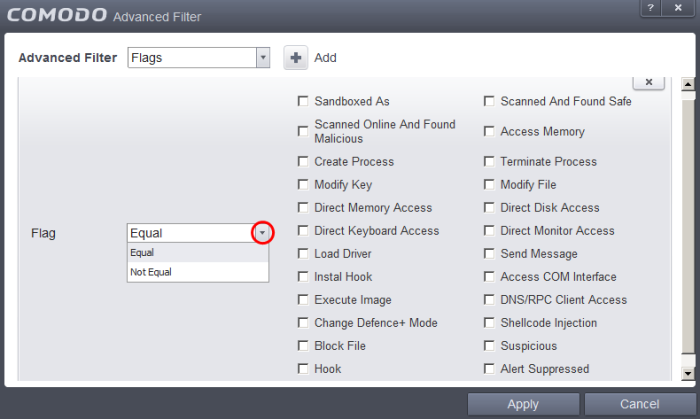
Flags: Selecting the 'Flags' option displays a drop down menu and a set of specific filter parameters that can be selected or deselected.
-
Select 'Equal' or 'Not Equal' option from the drop down menu. 'Not Equal' will invert your selected choice.
-
Now select the check-boxes of the specific filter parameters to refine your search. The parameter available are:
- Sandboxed As
- Scanned Online and Found Safe
- Scanned Online and Found Malicious
- Access Memory
- Create Process
- Terminate Process
- Modify Key
- Modify File
- Direct Memory Access
- Direct Disk Access
- Direct Keyboard Access
- Direct Monitor Access
- Load Driver
- Send Message
- Install Hook
- Access COM Interface
- Execute Image
- DNS/RPC Client Access
- Change Defense+ Mode
- Shellcode Injection
- Block File
- Suspicious
- Hook
- Alert Suppressed
For example, if you select 'Equal' option from the drop-down field and select 'Direct Memory Access' from the checkboxes, , then only events of applications that tried to access the server memory will be displayed. If you select 'Not Equal' option from the drop-down field and select 'Modify Key' check box, then all events that do not have the entry 'Modify Key' in the 'Flags' column will be displayed. You can select more than one check box options from this interface, as required.
-
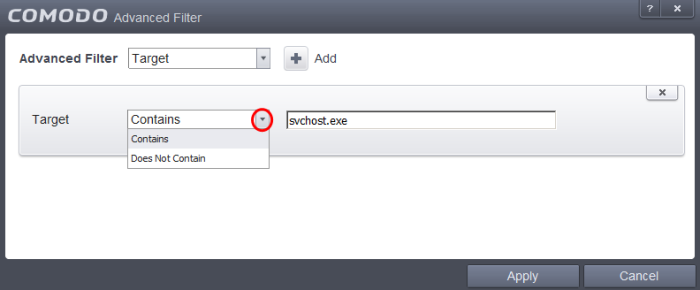
Target: Selecting the 'Target' option displays a drop-down menu and text entry field.
-
Select 'Contains' or 'Does Not Contain' option from the drop-down menu.
-
Enter the text or word that needs to be filtered from the Target column.
For example, if you select 'Contains' option from the drop-down field and enter the phrase 'svchost.exe' in the text field, then all events containing the entry 'svchost.exe' in the 'Target' column will be displayed. If you select 'Does Not Contain' option from the drop-down field and enter the phrase 'svchost.exe' in the text field, then all events that do not have the entry 'svchost.exe' in the 'Target' column will be displayed.
| Note: More than one filter can be added in the 'Advanced Filter' pane.
After adding one filter type, select the next filter type and
click 'Add'. You can also remove a filter type by clicking the 'X'
button at the top right of the filter pane.
|
- Click 'Apply' for the filters to be applied to the Defense+ log viewer. Only those Defense+ entries selected based on your set filter criteria will be displayed in the log viewer.



