Configure the Sandbox
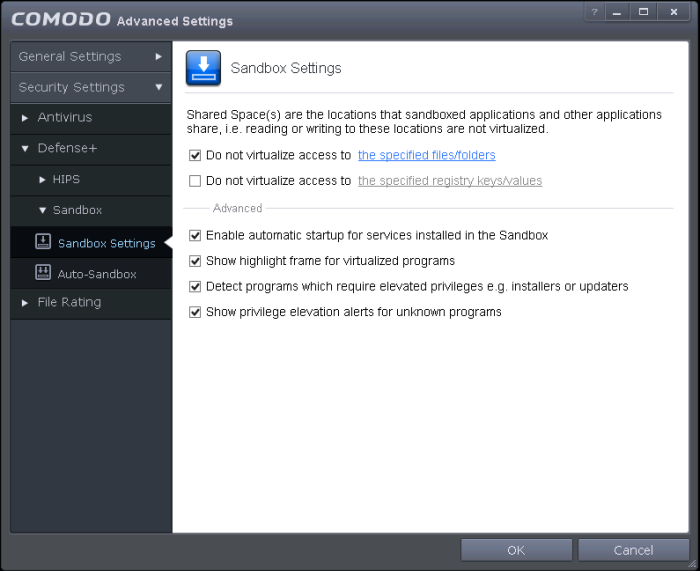
The 'Sandbox Settings' section of 'Advanced Settings' allows you to configure the Sandbox settings that determine how proactive the Sandbox should be and which types of files it should check.
- The 'Sandbox Settings' panel can be accessed by clicking 'Tasks > Sandbox Tasks > Open Advanced Settings > Security Settings > Defense+ > Sandbox > Sandbox Settings
Click the following links to find out more about each section:
- Shared Space Settings- Files downloaded or generated by sandboxed applications that you wish to be able to access from your real system should be downloaded to the shared space
- Advanced Settings – Allows you to configure Sandbox alert settings as well as to enable automatic startup services for programs installed in the Sandbox.
'Shared Space' is a dedicated area on your local drive that sandboxed applications are permitted to write to and which can also be accessed by non-sandboxed applications (hence the term 'Shared Space'). For example, any files or programs you download via a sandboxed browser that you wish to be able to access from your real system should be downloaded to the shared space. This is located by default at 'C:/Program Data/Shared Space'.
![]()
You can access the shared space folder in the following ways:
- Clicking the 'Shared Space' shortcut on your computer desktop
- Clicking 'Shared Space' button on the CAVS interface
- Opening 'Sandbox Tasks' from the Tasks interface then clicking 'Open Shared Space'
- By default, sandboxed applications can access folders and files on your 'real' system but cannot save any changes to them. However, you can define exceptions to this rule by using the 'Do not virtualize access to...' links.
To define exceptions for files and folders
- Enable the 'Do not virtualize access to the specified files/folders' check-box then click on the words the specified files/folders. The 'Manage Exclusions' dialog will appear.
- Click the handle at the bottom to open the tools menu then click 'Add.
Files - Allows you to specify files or applications that sandboxed applications are able to access
Folders - Specify a folder that can be accessed by sandboxed applications
File Groups - Enables you to choose a category of files or folders to which access should be granted. For example, selecting 'Executables' would enable you to create an exception for all files with the extensions .exe .dll .sys .ocx .bat .pif .scr .cpl. For more details on file groups, refer to the section File Groups.
Running Processes - Allows you to add a program that sandboxed applications are able to access
- To edit an exception, select it from the list, click the handle to open the tools menu then select 'Edit'.
- Change file or folder location path and click 'OK'
- Click 'OK' to implement your settings
- To manage available file groups, click the 'Groups' button from the tools menu. The 'Manage File Groups' dialog allows you to view, add and edit file groups. Please refer to File Groups if you need more information with this area.
To define exceptions for specific Registry keys and values
- Enable the 'Do not virtualize access to the specified registry keys/values' check-box then click on the words the specified registry keys/values. The 'Manage Exclusions' dialog will appear.
- Click the handle at the bottom to open the tools menu then click 'Add'.
- Registry Groups - Allows you to batch select a predefined group of important registry keys as exceptions. For an explanation of CAVS registry groups, refer to the section Registry Groups.
- Registry Entries - Opens an interface that allows you to quickly browse Windows registry keys and add them as exceptions:
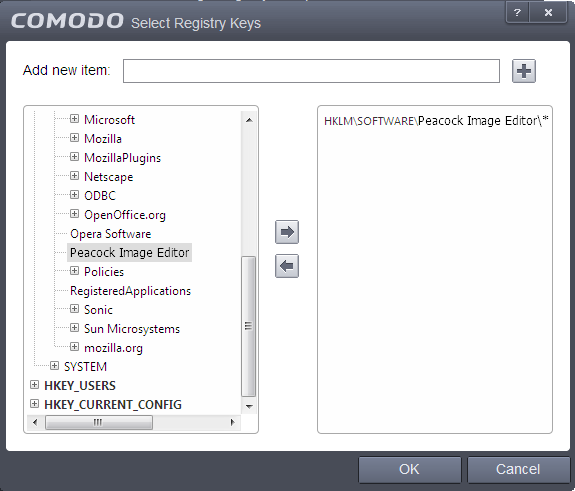
- Click 'OK' to implement your settings.
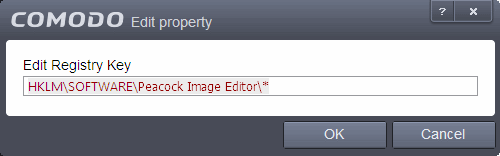
- To edit an exception, first select it from the list, click the handle to open the tools menu then select 'Edit'.
- Edit the key path and click OK.
- Enable automatic startup for services installed in the sandbox - By default, CAVS does not permit sandboxed services to run at Windows startup. Select this check-box to allow them to do so. (Default = Enabled)
- Show highlight frame for virtualized programs - If enabled, CAVS displays a green border around the windows of programs that are running inside the sandbox. (Default = Enabled)
The following example shows an .odt document opened with a sandboxed version OpenOffice Writer:
-
Detect programs which require elevated privileges:Allows you to instruct the Sandbox to display alerts when an installer or updater requires administrator or elevated privileges to run. An installer that is allowed to run with elevated privileges is permitted to make changes to important areas of your computer such as the registry. Refer to the section Understanding Security Alerts for more details.
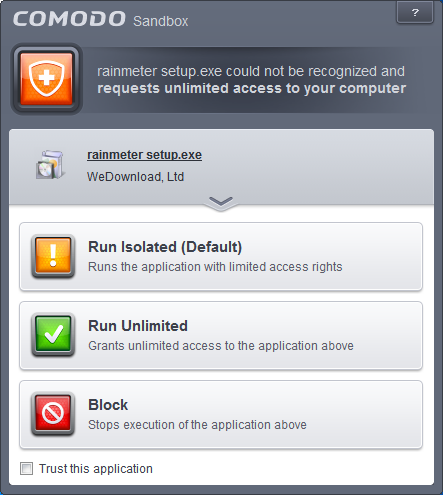
You can decide on whether or not to allow the installer or update based on your assessment, from the alert itself. (Default=Enabled)
- Show privilege elevation alerts for unknown programs : Allows you to instruct the Sandbox to display alerts when a new or unrecognized program, application or executable requires administrator or elevated privileges to run. You can decide on whether or not to allow the unknown application based on your assessment, from the alert itself. (Default=Enabled)



