CIS Complete - Installation and Activation
Note - Before beginning installation, please ensure you have uninstalled any other antivirus and firewall products that are on your computer. Click here to read the full note.
Comodo Internet Security Complete can be downloaded from www.comodo.com/home/internet-security/internet-security-complete.php after signing up for subscription and includes Chromodo, GeekBuddy, TrustConnect and the Comodo Guarantee.
-
Choose whether you want the 32 or 64 bit version of CIS then click 'download'.
-
If you are unsure which version you need, select the 32/64-bit Windows Installer. This executable contains BOTH 32 and 64 bit installers. The setup routine will automatically detect which version of Windows you have and install the appropriate version. Please note, the Universal Windows Installer is a much larger download than the individual 32 or 64 bit setup files.
After downloading the required Comodo Internet Security setup file to your local hard drive, double click on the setup file to start the installation wizard.
Step 1 - Choosing the Interface Language
The Language selection dialog will be displayed.
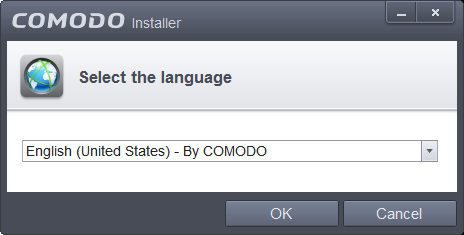
Comodo Internet Security is available in several languages.
-
Select the language in which you wish the wizard should continue and Comodo Internet Security Complete is to be installed, from the drop-down menu and click 'OK'.
Step 2 - Installation Configuration
The installation configuration screen will be displayed.
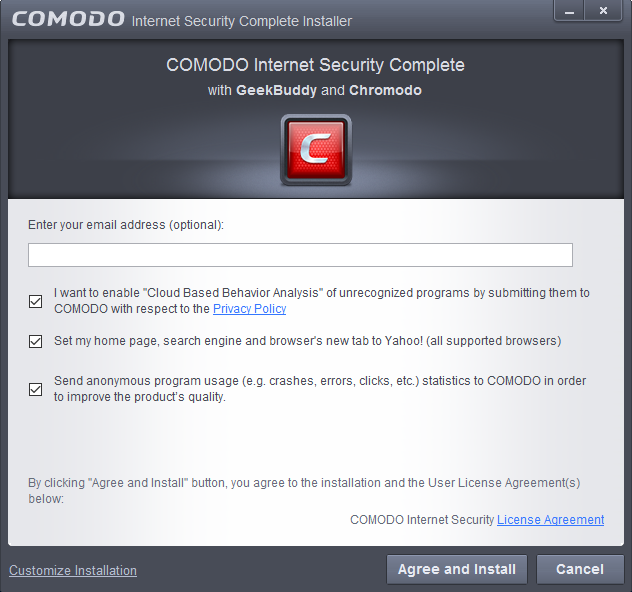
- If you click 'Customize Installation' then you can choose advanced options. These include which CIS components you wish to install, the ability to choose CIS installation path and other advanced CIS configuration settings.
Receive Comodo News and Notifications
If you wish to sign up for news about Comodo products then enter your email address in the space provided. This is optional.
Cloud Based Behavior Analysis
Any file that is identified as unrecognized is sent to the Comodo Instant Malware Analysis (CIMA) server for behavior analysis. Each file is executed in a virtual environment on Comodo servers and tested to determine whether it behaves in a malicious manner. If yes, the file is then manually analyzed by Comodo technicians to confirm whether it is a malicious file or not. The results will be sent back to your computer in around 15 minutes. Comodo recommends users leave this setting enabled. Read the privacy policy by clicking the 'Privacy Policy' link.
Browser Homepage
Leaving this setting enabled will:
- Set your home page, search engine and browser's new tab to Yahoo (all supported browsers)
- Currently supported browsers are Mozilla Firefox, Google Chrome, Internet Explorer, Comodo Dragon, Comodo Ice Dragon, Chromodo and Opera.
- Make Yahoo your default search engine. This means:
- When you enter a search item into the address bar of a supported browser, the search will be carried out by Yahoo
- A ‘Search with Yahoo’ menu entry will be added to the right-click menu of supported browsers.
- Yahoo will be set as the default search engine in the ‘Search’ box of supported browsers
- The instant ‘search suggestions’ that you see when you start typing a search item will be provided by Yahoo.
Send Program Usage Data
Comodo collects collects the usage details from millions of CIS users to analyze their usage patterns for the continual enhancement of the product. Your CIS instillation will collect details on how you use the application and send them periodically to Comodo servers through a secure and encrypted channel. Also your privacy is protected as this data is sent anonymous. This data will be useful to the engineers and developers at Comodo to identify the areas to be developed further for delivering the best Internet Security product. Disable this option if you do not want your usage details to be sent to Comodo. Comodo recommends users leave this setting enabled. You can change this setting from Advanced Settings > General Settings > Log Settings interface, at anytime after installation.
- Please review and/or modify the settings in the dialog.
-
If you click 'Customize Installation' then you can choose advanced options. These include which CIS components you wish to install, the ability to choose CIS installation path and other advanced CIS configuration settings.
End User License Agreement
Read the complete User License Agreements by clicking the 'License Agreement' links of Comodo Internet Security.
After reading the agreement, click the 'Back' button to return to the installation configuration screen.
Once back at the main installer screen, if you wish to configure advanced options, click 'Customize Installation'.
Otherwise, click 'Agree and Install' to begin installation.
Click the 'Customize Installer' link to select the components to be installed, enable security popup alerts to be minimized and choose installation path.
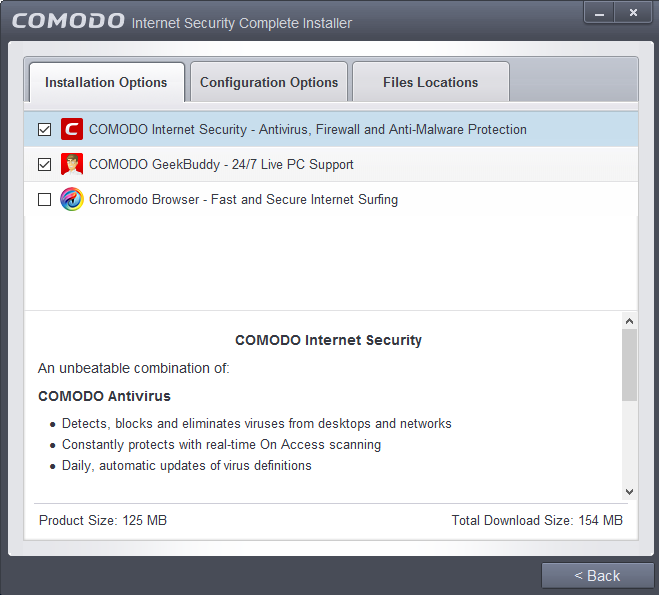
Selecting Components to Install (Click to go back to Step 2)
- Click the 'Installation Options' tab to select the components to be installed.
-
Install COMODO Internet Security - Selecting this option installs Comodo Antivirus, Comodo Firewall, Defense+ components. Installing CIS Complete is mandatory to qualify for the virus free guarantee.
-
Install COMODO GeekBuddy - Selecting this option installs GeekBuddy, a 24 x 7 remote support service in which Comodo experts can help you solve any computer related problems you may encounter. Refer to the section Comodo GeekBuddy for more details.
-
Install Chromodo Web Browser - Selecting this option installs Chromodo, a fast and versatile Internet browser based on Chromium technology and infused with Comodo's unparalleled level of security. Refer to the section Chromodo for more details.
Configuration Options
- Click the 'Configuration Options' tab to configure pop-up alert options.
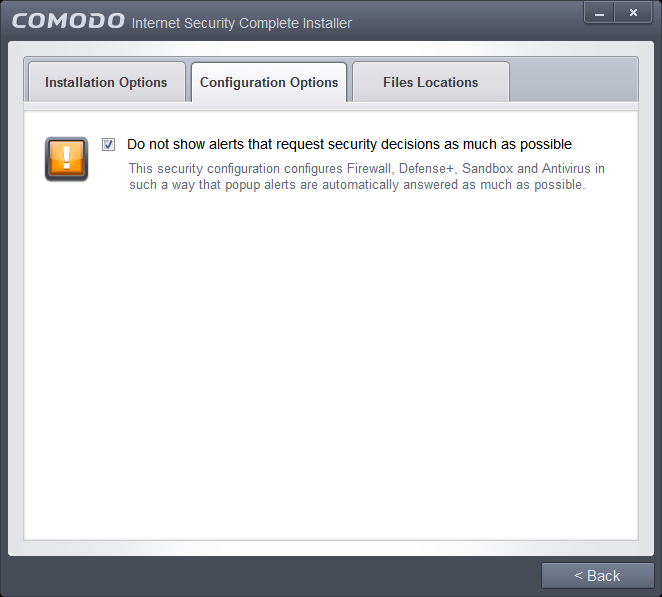
-
Do Not show alerts that request security decisions as much as possible - When this option is selected, CIS is configured to automatically deal with most issues in a secure manner without raising a popup alert - thus minimizing user intervention. Most users should leave this option at the default state of enabled. Advanced users wishing to gain greater insight into CIS actions and/or to have more control over security decisions may wish to disable this option.
Choosing Installation Location
- Click the 'Files Locations' tab to choose the installation path.
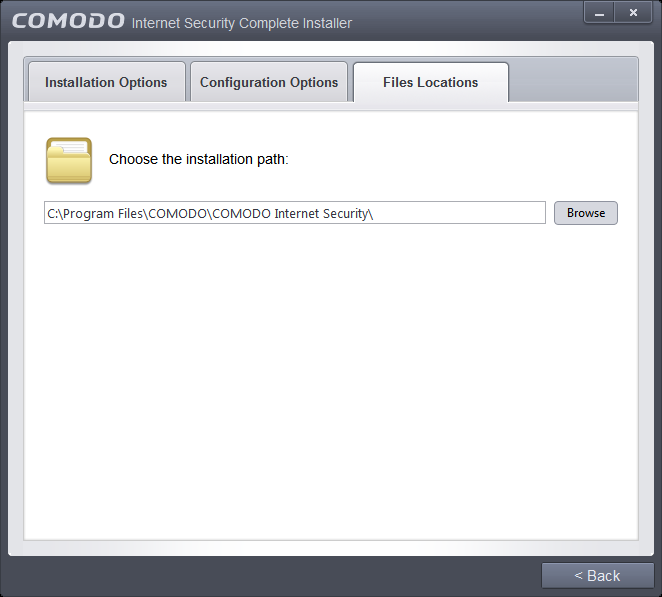
This interface allows you to set the installation folder for Comodo Internet Security. The default path is C:/Program Files/COMODO/COMODO Internet Security. If you want to install the application in a location other than the default location, click 'Browse' to choose a different location.
After customizing your installation, click the 'Back' button to return to the installation configuration screen.
- Click the 'Agree and Install' button to proceed with the installation.
Step 3 - Installation progress (Click to go back to Step 2)
The installation progress will be displayed...
...and on completion, the application initiates the first quick scan on your computer. The virus database will be updated automatically prior to the scan.
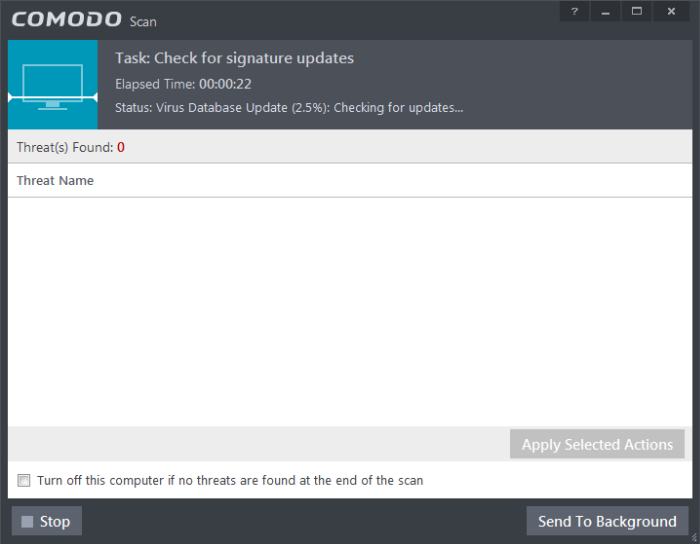
You can also send this task to the background by pressing the 'Send to Background' button and retrieve it in the 'Task Manager' interface. Refer to the section 'Manage CIS Tasks' for more details.
CIS will commence a Quick Scan of system memory, autorun entries, hidden services, boot sectors and other critical areas automatically after the virus database has been updated.
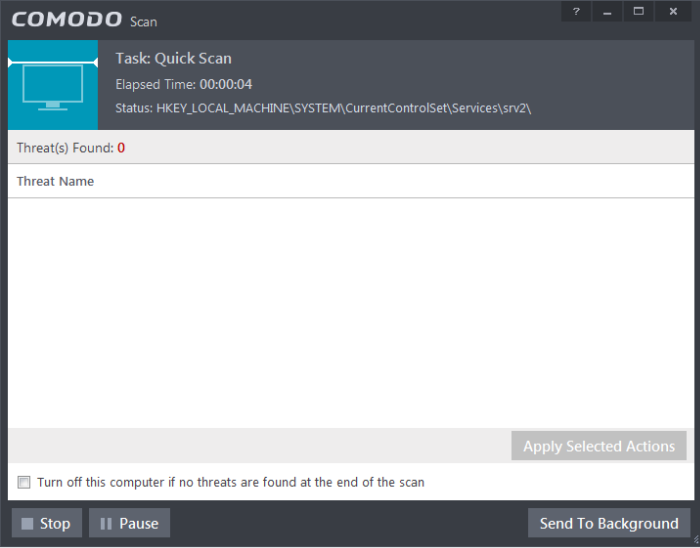
If you do not want the scan to continue at this time, click the 'Stop' button.
After the scanning is complete, and any threats are found, an alert screen will be displayed. The alert will display the number of threats/infections discovered by the scanning and provide you the options for cleaning.
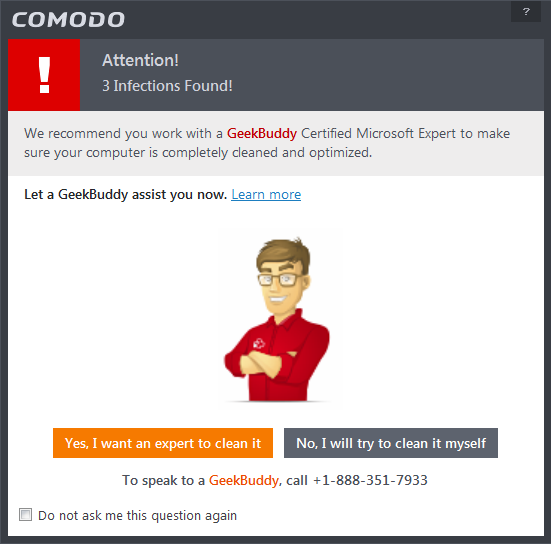
- If you wish to have a skilled professional from Comodo to access your system and perform an efficient disinfection, click 'Yes, I want an expert to clean it'. If you are a first-time user, you will be taken to Comodo GeekBuddy webpage to sign-up for a GeekBuddy subscription. If you have already signed-up for GeekBuddy services, the GeekBuddy chat session will start and a skilled technician will offer to clean your system.
For more details on GeekBuddy, refer to the section Comodo GeekBuddy.
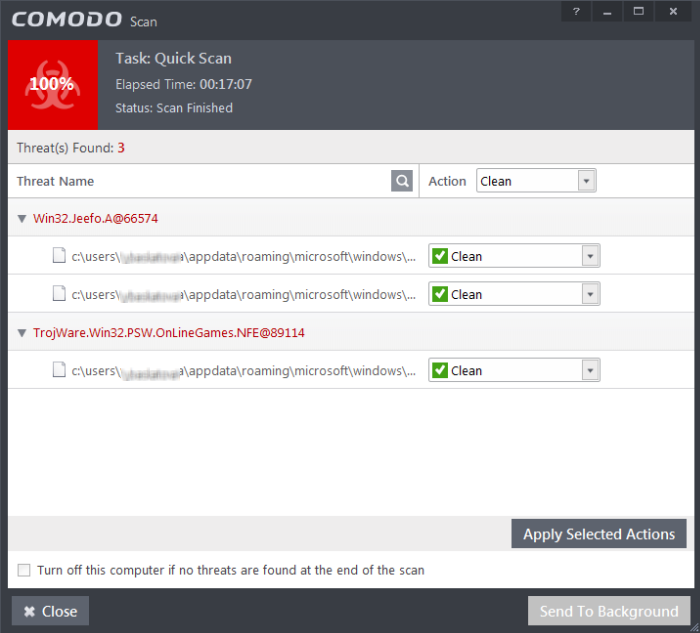
- If you wish to clean the infections yourself, select 'No, I will try to clean it myself'. The scan results screen will be displayed. The results will contain a list of files identified with threats or infections (Viruses, Rootkits, Malware and so on) and provide you the options for cleaning. Refer to the section Processing Infected Files for more details.
- An example results screen is shown below:
If your computer is connected to a home or work network, then you are prompted to configure it at the 'New Network Detected!' dialog. At the top of the dialog, the connectivity mode will be displayed, whether wired or wireless.
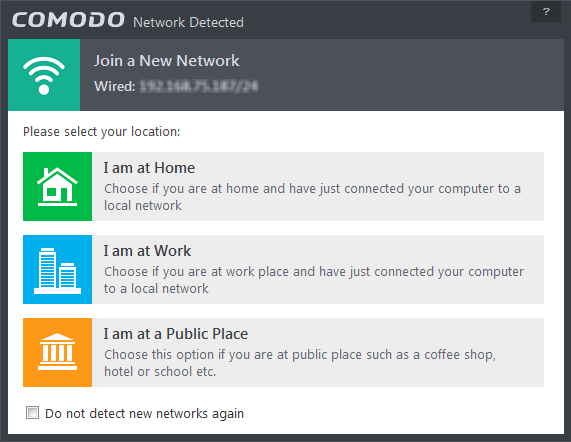
- Select your location from the three options
- Select 'Do not detect new networks again' If you are an experienced user that wishes to manually set-up their own trusted networks (this can be done in 'Network Zones' interface and through the Stealth Ports Wizard).
Step 4 - Restarting Your System
In order for the installation to take effect, your computer needs to be restarted.
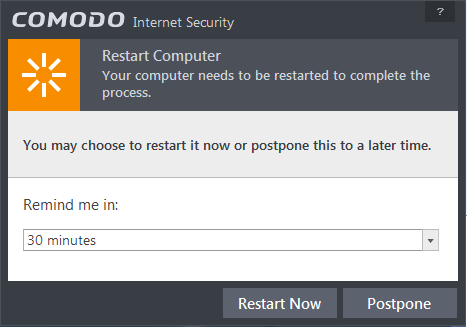
- If your want to restart the computer immediately, save all your work and click 'Restart Now'.
- If you want to restart the computer at a later time, select when you need to be reminded from the drop-down and click 'Postpone'.
|
Note: The installation will take effect only on the next restart of the computer. |
Step 5 - After Restarting Your System
After restarting, a 'Welcome' screen will appear. This contains a summary of the components you chose to install as well as some friendly advice. You can also purchase license key from this screen if you have not done so already.
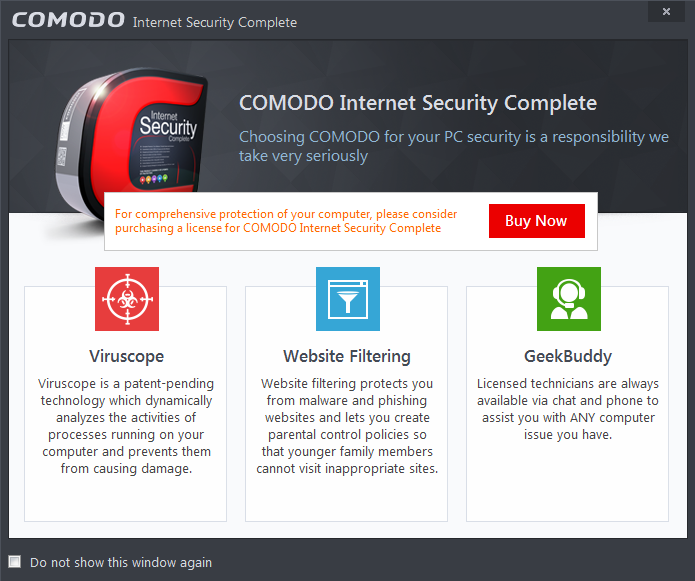
This screen will appear every time you start your system. If you do not want the screen to be displayed on every start up, select the check box 'Do not show this window again' before closing the window.
The CIS Widget will be displayed:
|
Important Note: After successful installation, you need to activate the license for using the product. In order to get your guarantee coverage and TrustConnect service enabled, you need to activate the license first.
|



