Configure Containerization Settings
- Click 'Configuration' > 'Security Policy' > 'Containment', to open this interface.
- Containerization is a security technology whereby 'unknown' files are run inside a secure, virtual environment. This isolation prevents them from potentially attacking the endpoint or stealing data.
- A file can have one of three trust ratings – 'safe', 'malicious' or 'unknown'. Safe files are allowed to run on the host, while malicious files are deleted or quarantined.
- 'Unknown' files are those for which no trust rating exists in our database. They could not be classified as definitely safe, nor definitely malicious.
- Unknown files are delivered to the endpoint wrapped in Comodo's containment technology. Contained files write to a virtual file-system, cannot modify other processes, and are denied access to the registry and user data.
- The 'Containerization Settings' interface lets you configure which file-extensions are run in the container. You can also specify the maximum number of nested archives that should be unpacked and checked.
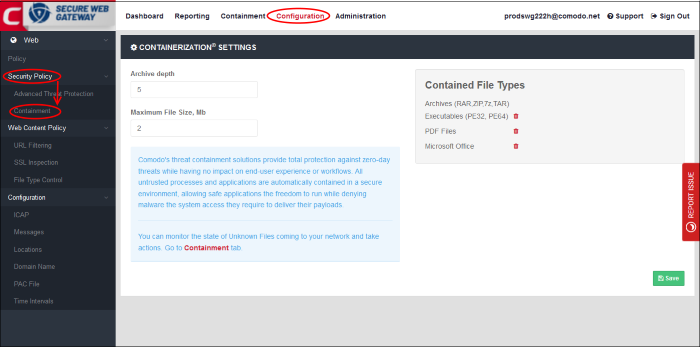
- Archive Depth – Maximum level the archive files will be unpacked to check for file within archive files. Enter the value till which the zip files will be checked. If the archive depth is more than the provided value, the files inside the exceeded layer will not be checked. For example, if the value is provided as 5, then files will be checked up to 5 layers only and others will be allowed to pass.
- Maximum File Size, MB – Enter the maximum file size that Comodo SWG should scan the archive files.
- Contained File Types – Displays the types of files that are scanned and sandboxed if required.
- Archives – File types with extensions RAR, ZIP, 7z and TAR. This type cannot be deleted from the list.
- Executables – Executable files of both 32 and 64 bit types inside the archive. You can remove this type by clicking the trash can icon beside it. If required, it can be added again by clicking the '+' button.
- PDF Files – Files with PDF extension inside the archive will be scanned. You can remove this type by clicking the trash can icon beside it. If required, it can be added again by clicking the '+' button.
- Microsoft Office – Files inside the archive with extensions of MS Office such as .doc, .xls and so on. You can remove this type by clicking the trash can icon beside it. If required, it can be added again by clicking the '+' button.
- Click the 'Save' button at the bottom.
The statuses of unknown files that are downloaded can be viewed in the 'Containment' interface. You can navigate to the page by clicking the 'Containment' tab at the top of the interface. See 'Unknown Threat Statistics' for more details.



