Unknown Threat Statistics
- Click 'Containment' in the top-menu to open the 'Unknown Threat Details' area.
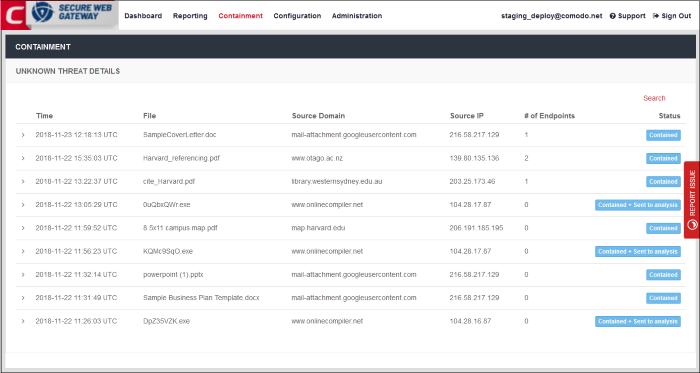
- This area shows details about unknown files discovered on your network.
- Unknown files are automatically run in a secure environment called the 'Container'. While running in the container, unknown files cannot access operating system resources, the file system, other processes or user data.
- Simultaneously, unknown files are uploaded to Valkyrie for analysis to establish their trust level.
|
Unknow Threat Details - Table of Column Descriptions |
|
|---|---|
|
Column Header |
Description |
|
Time |
Date and time the unknown file was detected. |
|
File |
Name of the file, including file extension. |
|
Source Domain |
Website from which the file originated. |
|
Source IP |
IP address of the domain from which the file originated. |
|
# of Endpoints |
Number of endpoints on which the file was contained. |
|
Status |
Shows whether the file was contained, or contained + uploaded to Valkyrie for analysis. Valkyrie is Comodo's file analysis system. It runs a barrage of tests on unknown files to discover their behavior and assign them a trust rating. |
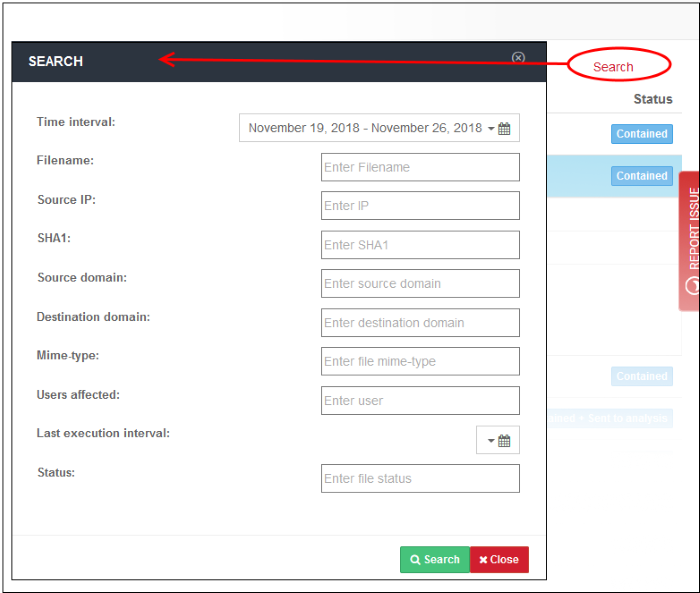
The 'Search' button allows you to find specific files by numerous criteria:
Click a file row to view its details:
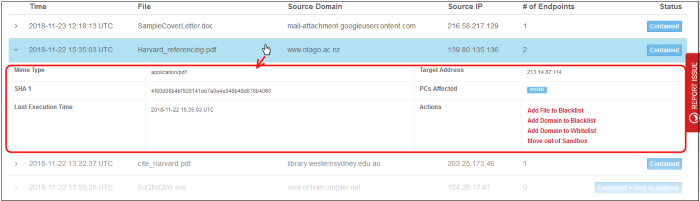
- MIME Type – File type
- SHA 1 – Hash value of the file
- Last Execution Time – The date and time the file was last run
- Target Address – The location network IP address the file was downloaded
- PCs Affected – The name of the affected computer(s)
- Actions - Click a link to categorize:
- Add File to Blacklist – File is added to Global Blocked File List ('Configuration' > 'Advanced Threat Protection' > 'Global Blocked File List')
- Add Domain to Blacklist - Domain is added to blacklist in the default profile of ATP on the Advanced Threat Protection Page ('Configuration' > 'Advanced Threat Protection' > 'Domain Blacklist')
- Add Domain to Whitelist - Domain is added to whitelist in the default profile of ATP on the Advanced Threat Protection Page ('Configuration' > 'Advanced Threat Protection' > 'Domain Whitelist')
- Move out of Sandbox - The file runs outside the container and will not be contained again.
Valkyrie
- You can view the status of unknown files you have submitted to Valkyrie at https://valkyrie.comodo.com/
- You can login to Valkyrie with your Comodo SWG username and password



